New report from Akamai provides insight into the recent surge of game-related hacking
Attacks against the video gaming industry and its gamers skyrocketed during the pandemic lockdown year of 2020, with more than 240 million web app attacks (a growth of 340% over the previous year). While the pandemic conditions likely contributed to this growth, researchers believe that attacks will continue, and continue to grow, even after the pandemic is over.
Akamai’s research paper, Gaming in a Pandemic, shows that web application attacks in the gaming industry grew by 415% between 2018 and 2020. Global growth was only 2% per year. This growth has been accompanied by a steady increase with significant spikes in phishing and credential stuffing attacks targeting gamers and the games industry.
As usual, the criminals are generally after users’ (in this case gamers’) PII. This is primarily a financial motivation. PII in the form of credentials can be sold on to other hackers and even other gamers seeking a cheap entree into a new game. But ‘revenge’ attacks from disgruntled gamers in gaming may be even more frequent than revenge attacks from terminated employees in the business world.
“Game accounts actually sell well,” Steve Ragan, author of the report (PDF) and security researcher at Akamai, told SecurityWeek. “Let’s say you wanted to buy access to a specific type of shooter game. There are criminals that will sell you usernames and passwords to that game so you can walk in and play.”
The ROI for the criminal is in bulk. “Let’s say a criminal’s going out and they launch a credential stuffing attack, and they come back with, say, 100 accounts that are valid,” he continued. “They can sell those hundred for $5 a pop. If you take the time spent versus what they’re bringing in, that’s a fair profit!”
In effect, this introduces a new, more predatory form of game piracy; rather than games being shared for free at the publisher’s expense, they are now being stolen directly from the player and sold on.
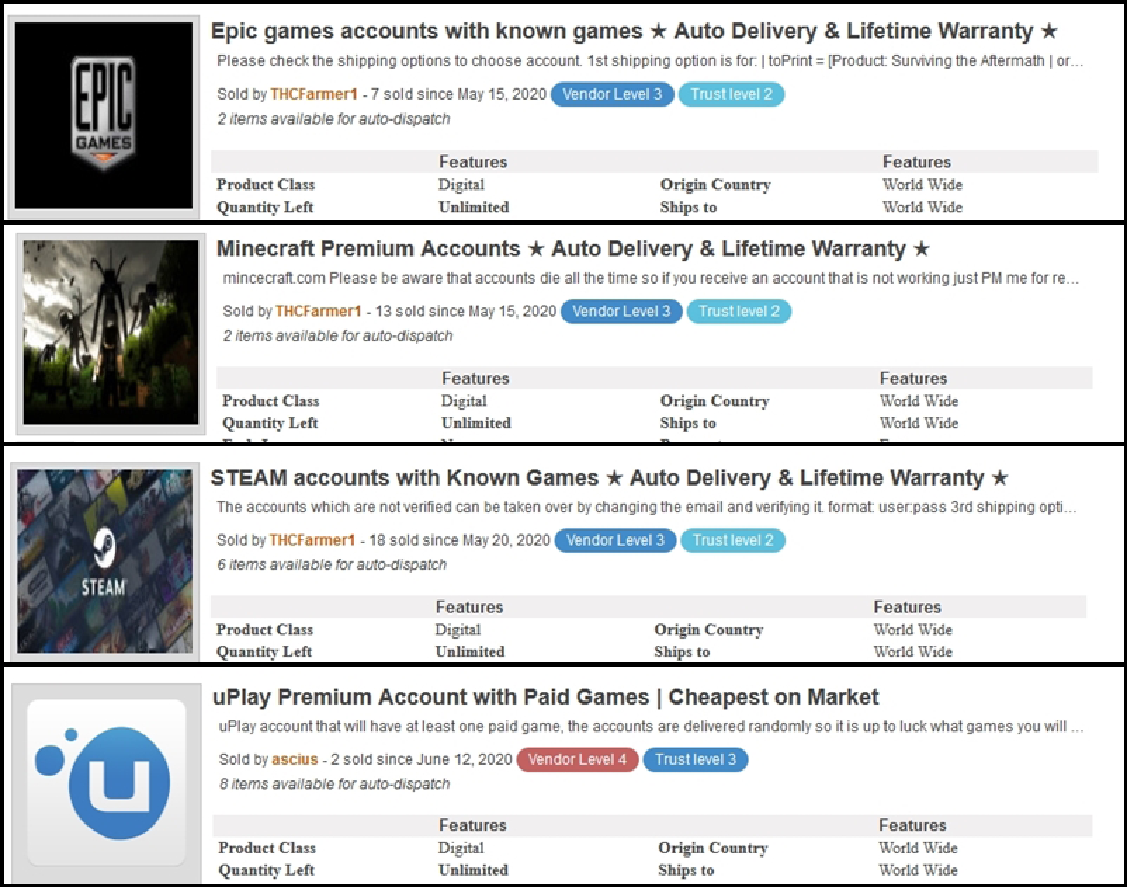
Figure 1 Online marketplace selling stolen game accounts
There are surprisingly slick and professional online marketplaces, offering illegally obtained access to premium gaming accounts and game libraries. These entries have trust ratings for the criminal vendors, and most even promise a lifetime warranty on the illegal goods. Hackers have effectively formed their own digital gaming black market.
This does give the gaming sector a target for hackers that other industries don’t necessarily have; an additional end-product, on top of the usual payloads cybercriminals can target in other sectors. However, profitability is not just a matter of what you can sell, but how easily you can acquire it.
Phishing is an ever-popular attack vector against both gamers and game companies, but the Akamai report shows a degree of divergence between player-oriented attacks and business-oriented attacks. While players were targeted with account-takeover attacks to steal and sell the content they owned, companies had to face the usual issue of PII-harvesting and large-scale data breaches.
Automation is the common factor for both target groups. Gaming companies must contend with SQL injection (SQLi) attacks more than any other attack vector, with Local File Inclusion (LFI) attacks at a distant second place. Together, SQLi and LFI attacks accounted for 83% of web application attacks. Gamers themselves were targeted by phishing and credential stuffing attacks more than any other vector.
SQLi, LFI, phishing and credential stuffing are all notable for their ability to be automated. Hackers can make or use a simple script, feed in some acquired information (usually from large-scale data-dumps on the dark web) and automatically target millions of users. Even with a 1% success rate, that would still be tens of thousands of successful attacks. At the same time, security in gaming is a tricky issue to navigate for both players and businesses.
“The gaming industry does want to defend its players, but security is a balancing act,” said Ragan. “Gaming companies spend a lot of time and effort researching their security posture as well as their players’ needs, and they try to find a balance between the two of them… the thing is, you can’t force somebody to do something”.
Although the security practices adopted by individual gamers are not in the scope of the report, the effect of user friction is a universal constant in security. Gaming is a leisure activity; gamers want to relax, unwind, and have fun. Players may be more reluctant to spend time and energy going the extra mile to secure their ‘fun’ activity than they would with work, finance, or life admin.
With gamers’ security posture already on shaky ground, the effect is compounded by the relative skill-barrier for hackers. The gaming sphere offers more potential profitable targets for cyber-criminals, and the most popular attack vectors can run with a ‘set it and forget it’ level of automation. Akamai has discovered hacking-oriented chats on Discord, Telegram, public chat services and forums; all consumer-level social platforms rather than the clandestine and obfuscated communication channels that one would expect cyber-criminals to use.
While this is not confirmed by the data, this suggests that there may be a higher rate of neophyte hackers targeting gamers, or even gamers themselves getting into hacking for the first time. Ragan comments: “Because the tools are so readily available, and really do not require a high degree of sophistication to use, it is entirely possible that some of the attacks we saw last year came from gamers who got banned for cheating, or violations of terms, trying to target the company and express their displeasure.”
The elephant in the room is the timing of this surge in hacking activity, coinciding near-perfectly with the Covid-19 pandemic and consequent lockdowns. Gamers and hackers alike have been stuck at home with more free time on their hands, and looming economic anxiety providing motivation for trying to make some extra money – even through unscrupulous methods.
Akamai’s data gives a lot of insight into the recent surge of game-related hacking, but the underlying causes are still a matter of inference, interpretation and conjecture. When we can only make an educated guess at these reasons, we can only make an educated guess at what the future holds. Gaming companies are putting more resources into protecting players and their data, and more players are coming to terms with adopting better security practices. Eighty percent of gamers surveyed by Akamai said they were willing to adopt MFA and password management to help stay secure.
As much as players and gaming companies can do, the potential profitability offered to hackers is not going away. It’s possible that as lockdowns ease, there will be fewer players to target and we’ll see at least some drop-off in these statistics, but the gaming industry has been growing rapidly in value and popularity since long before Covid-19. Whether the pandemic has any direct, causal link with the explosion of games-industry attacks is impossible to say with certainty, but Ragan has the last word:
“When you look at the data, and you remember what happened over the course of 2020, you can’t ignore the pandemic. But I just can’t conclusively prove that it’s all related to the pandemic. The optimist in me wants to say that [this growth is] going to go down and things will get better, but the pessimist and the realist in me, based on what I see every day when I’m just lurking on the web and working… I think this is going to continue. I think the criminals have found the gaming industry to be a very resourceful area to target.”
Related: Gaming Giant EA Confirms Breach, Theft of Source Code
Related: Chinese Hackers Target South Korean Gaming Company
Related: Man Behind DDoS Attacks on Gaming Companies Pleads Guilty
Related: Hacker Who Disrupted Sony Gaming Firm Gets Federal Prison















