Several vulnerabilities rated “high severity” have been discovered by researchers in Fuji Electric V-Server. The vendor has released updates that should address the flaws.
The existence of the security holes, all of which could allow a remote attacker to execute arbitrary code, was made public this week when ICS-CERT published two advisories.
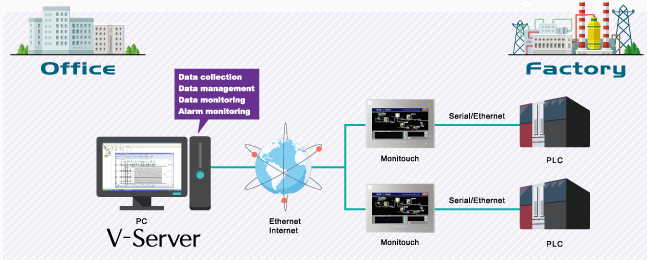
Fuji Electric V-Server is a tool that allows organizations to access programmable logic controllers (PLCs) located in the plant from PCs located on the corporate network. The two systems are linked over Ethernet via the Monitouch human-machine interfaces (HMI) that are used to monitor the PLCs. ICS-CERT says the product is used worldwide, mainly in the critical manufacturing sector.
According to ICS-CERT, Fuji Electric V-Server is affected by use-after-free, untrusted pointer dereference, heap-based buffer overflow, out-of-bounds write, integer underflow, out-of-bounds read, and stack-based buffer overflow vulnerabilities that may allow remote code execution, which could lead to a denial-of-service (DoS) condition or information disclosure.
Register for SecurityWeek’s 2018 ICS Cyber Security Conference
A separate advisory from ICS-CERT describes a high severity buffer overflow affecting V-Server Lite. The flaw can be exploited for code execution – and again it can lead to a DoS condition or information leakage – using specially crafted project files.
All the vulnerabilities have been patched by Fuji Electric with the release of version 4.0.4.0.
The V-Server vulnerabilities were reported to the vendor via Trend Micro’s Zero Day Initiative (ZDI) by Steven Seeley of Source Incite. The flaw affecting the Lite version was identified by Ariele Caltabiano (aka kimiya) and also reported to Fuji Electric via ZDI.
ICS-CERT warned that public exploits are available for some of the vulnerabilities. This may refer to the fact that ZDI has published more than a dozen advisories describing security holes found by Seeley and Caltabiano in Fuji Electric V-Server. The ZDI advisories were published just as this article was being written – several hours after ICS-CERT released its own advisories – but they do not contain any technical information on the flaws.
According to the ZDI advisories, Seeley reported the vulnerabilities to the vendor in March 2018, while Caltabiano did so in June.
ZDI says the flaws “exist within the parsing of a VPR file” and they are caused by either the lack of validating the existence of an object prior to performing operations on that object, or the lack of proper validation for user-supplied data.
While the ICS-CERT advisories assign a “high severity” rating to the vulnerabilities, the ZDI advisories describe them as “medium severity” with a CVSS score of 6.8. The weakness found by Caltabiano has a CVSS score of 9.3 (critical) in the ZDI advisory.
Vulnerabilities affecting products that connect the corporate network to industrial control systems (ICS) can pose a serious threat since that is how many threat actors attempt to make their way onto sensitive systems.
A study conducted recently by Positive Technologies showed that in many organizations hackers can easily gain access to industrial environments from the corporate network.
Related: Five Threat Groups Target Industrial Systems
Related: Phishing Campaign Targets 400 Industrial Organizations














