While Anti-Virus Solutions Are Effective in Fighting Widespread Malware, There is a Good Chance Newer Malware Will Evade Those Solutions.
There has been a recent surge in reports of major security incidents, many of which were caused as a result of a malware-infected endpoint within a corporate network. Among the breaches victims were Coca-Cola, BG Group and the South Carolina Department of Revenue, to name a few. These malware infected endpoints likely had anti-virus (AV) solutions installed, as incident investigation reports didn’t mention the lack of AV as a reason for the success of the attack, yet they were still compromised by malware. That discrepancy might be explained with “First Months Security Gap” that AV solutions seem to suffer from.
The First Months Security Gap
The AV-TEST Institute is a “leading international and independent service provider in the fields of IT security and anti-virus research”. According to AV-TEST’s website , in order to test the protective effect of a security solution, AV-TEST researchers simulate a variety of realistic attack scenarios such as the threat of e-mail attachments, infected websites or malicious files that have been transferred from external storage devices. When carrying out these tests, AV-TEST takes the entire functionality of the protection program into account.
But even when all of the Anti-virus functionality enabled, the results reveal a worrisome security gap.
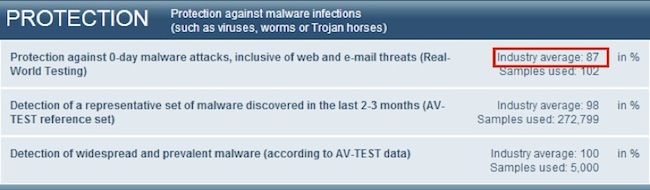
Figure 1 AV-TEST’s Antivirus Industry Detection Results for Windows 7 Malware
While antivirus solution are very effective in fighting widespread malware, and slightly less effective for older malware (2-3 month old), for a new malware, there is a good chance, 13% according to AV-TEST, it will evade the antivirus solutions. If you think that 13% is a sufficient misdetection rate consider the following example: Say you have 10 new malware attacks on your organization and your AV has 13% misdetection ratio, then one of the computers within the organization network is likely to get infected and stay that way for 2 months.
This two-month long security gap is a golden opportunity for the attackers and might be the “valley of death” for the defenders. Remember, it took the attackers less than two month to breach South Carolina Department of Revenue databases.
First Mover Advantage
Sun-Tzu, the ancient Chinese military strategist, stated: “Whoever is first in the field and awaits the coming of the enemy, will be fresh for the fight; whoever is second in the field and has to hasten to battle, will arrive exhausted”.
One of the main reasons for this security gap is that the attackers hold the “first mover advantage”. Attackers have access to anti-virus products, as they are publicly available. Therefore attackers can release their malware product, only after it passed “Quality assurance” tests in the attackers’ labs, making sure it goes undetected by antivirus solutions.
A demonstration of how a malicious payload can be modified to evade detection by AV product can be found in the following video. Graviton, a malware development framework executable, is initially (1:40 into the video) detected by the AV product, but later on (16:14 into the video) as some modifications are applied to the file, it evades the AV product, although its core functionality had not changed.
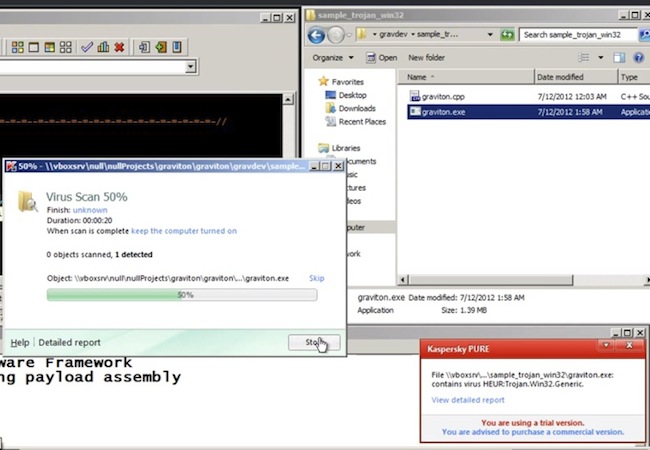
Figure 2 Original Graviton Malware Caught by AV
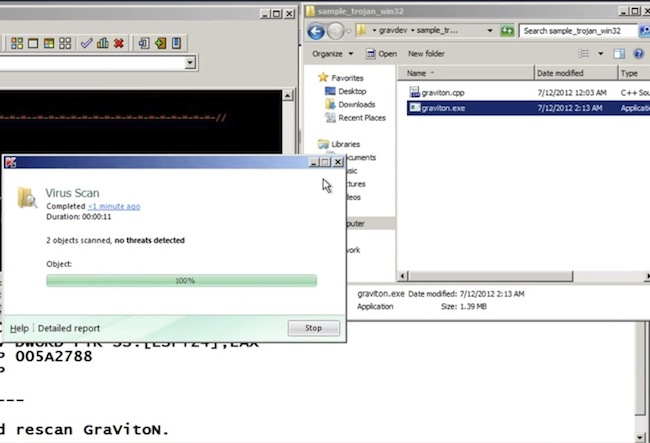
Figure 3 Modified Graviton Malware Evades AV
The phenomena and its explanation is not new, it dates back to 2005. That year, the AusCERT (Australian Computer Emergency Response Team) had announced that eighty(!) percent of new malware defeats antivirus and explained: “What is happening is that the bad guys, the criminals, are testing their malicious code against the antivirus products to make sure they are undetectable”.
Mitigating First Mover Advantage with Defense in Depth
How should we, as defenders, react to that imminent security gap? A famous psychological quote states that “The first step toward change is awareness”. We need to accept the fact that AV is not a perfect solution and that some of our machines within our networks will get infected. Next, we need to create some depth for our defense. We cannot let our first line of defense be our last of defense too.
Therefore, we need to augment our corporate defenses by rebalancing our security portfolio and investing in data protection solution. That way, even when our first line of defense (AV) gets breached, and it will get breached, our valuable data will still remain safe due to the data protection solutions mounted on our secondary line of defense.
















