The hacker who last week sent out thousands of fake emails from FBI systems is offering to sell data allegedly stolen in the recent breach at mobile stock trading platform Robinhood.
Robinhood last week revealed that it had suffered a data breach in early November after someone used social engineering to trick an employee into giving them access to some customer support systems.
The company said the attacker gained access to email addresses for five million users, and full names for a different group of roughly two million people. Approximately 310 users also had additional personal information exposed, including name, date of birth, and zip code. Ten of them also had “more extensive account details” exposed.
Robinhood noted at the time that the hacker had “demanded an extortion payment,” suggesting that the attack was conducted by a profit-driven cybercriminal.
Sure enough, a few days after Robinhood disclosed the incident, someone offered to sell the data allegedly stolen from the company on a well-known, publicly accessible hacker forum. The seller said they were looking to get at least “five figures” for the data, noting that “this is highly profitable if in the right hands.”
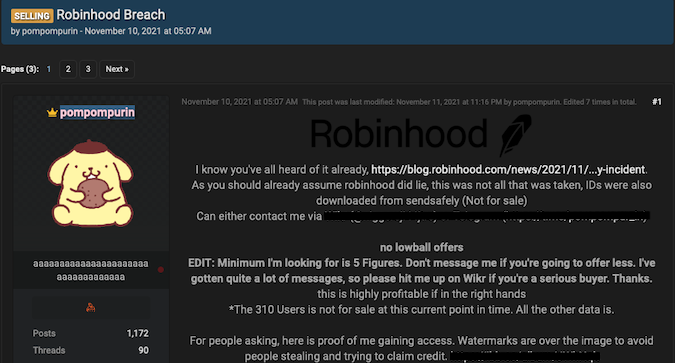
However, the seller is only offering the seven million email addresses and names — they specifically said that the records of the 310 users who had additional data compromised is not for sale. They also claimed that some IDs, which are also not for sale, were also obtained.
Robinhood told Bleeping Computer that some IDs were associated with the 10 users who had more extensive personal information compromised.
The individual who is offering to sell the Robinhood data is known online as pompompurin, the hacker who took credit for sending out thousands of emails last week from an email address belonging to the FBI.
More than 100,000 fake emails were sent out, informing recipients about a threat actor in their systems. The hoax emails claimed the threat actor was a security researcher, who suggested after the incident came to light that the operation was the work of a cybercriminal he had previously exposed.
The FBI said the compromised server was associated with its Law Enforcement Enterprise Portal (LEEP), which is used to communicate with state and local law enforcement partners. The agency claimed that the attacker did not gain access to any data on its network.
It’s unclear if pompompurin was indeed involved in the Robinhood hack. The hacker told Bleeping Computer that they had used a RAT in the attack on the trading platform, but the company said no malware was involved.
“It’s currently unclear whether there is any real relationship between pompompurin—who is the actor widely suspected as having conducted the FBI email breach—and the data breach affecting Robinhood,” the Digital Shadows Photon Research Team told SecurityWeek.
“The [hacker’s thread on the cybercrime forum] contains screenshots reportedly taken from Robinhood, which are inconclusive. Several posters have also replied to the thread, which also do not confirm or deny proof of access to the stolen data. pompompurin has previously advertised access to several other data breaches, albeit typically providing the accounts for free. pompompurin’s claims could be plausible, however remains unclear at this time,” the Digital Shadows researchers added.















