Thousands of fake emails coming from an FBI email address were sent out on Friday by someone who exploited a vulnerability in a law enforcement portal. The FBI has confirmed the breach, but said impact was limited.
Threat intelligence organization Spamhaus reported seeing more than 100,000 fake emails being sent out in two waves.
The hoax emails, coming from “[email protected],” carried the subject line “Urgent: Threat actor in systems.” The message appeared to come from the DHS and it informed recipients about “exfiltration of several of your virtualized clusters in a sophisticated chain attack.”
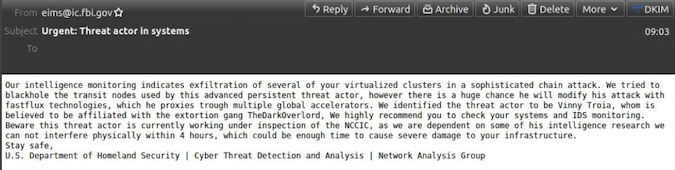
The emails claimed the threat actor was identified as Vinny Troia. Troia is a security researcher who claims to have been targeted numerous times by some hackers for exposing them.
Troia on Twitter said he suspected an individual who uses the online moniker “pompompur_in” was behind the attack. He said the individual is associated with a cybercrime group named The Dark Overlord, whose alleged members were exposed in a report published last year by Troia’s company, NightLion Security.
Indeed, an individual with the online nickname pompompurin contacted security blogger Brian Krebs shortly after the fake FBI emails were sent out, taking credit for the attack.
In a statement issued on Sunday, the FBI said the emails were sent out by someone who leveraged a “software misconfiguration” affecting the Law Enforcement Enterprise Portal (LEEP), which is used by the agency to communicate with state and local law enforcement partners.
“While the illegitimate email originated from an FBI operated server, that server was dedicated to pushing notifications for LEEP and was not part of the FBI’s corporate email service,” the FBI stated. “No actor was able to access or compromise any data or PII on the FBI’s network. Once we learned of the incident, we quickly remediated the software vulnerability, warned partners to disregard the fake emails, and confirmed the integrity of our networks.”
Pompompurin told Krebs that they exploited a vulnerability in the LEEP portal account registration process to be able to send out emails from the fbi.gov email address.
Specifically, the registration process involves sending a one-time passcode to the email address of the user who creates an account on the LEEP portal. Pompompurin discovered — or learned from someone else — that this one-time passcode was generated on the client side and included in a POST request. The same request also included parameters for the subject and body content of an email coming from eims(at)ic.fbi.gov, which the hacker replaced with their own subject and content.
The hacker created a script that automated the process, enabling them to send out thousands of fake emails.
The FBI says it has taken steps to prevent exploitation of the weakness leveraged in this attack.
Related: Phishers Target C-Suite with Fake Office 365 Password Expiration Reports
Related: Enterprises Warned About Zix-Themed Credential Phishing Attacks













