A researcher received a $5,000 reward from Facebook after finding a vulnerability that could have been exploited to impersonate users on other websites.
Facebook allows developers to use Facebook Login as the login system for their applications and websites. When a user signs up for an app via Facebook Login, an account is created for them and Facebook handles authentication.
Bitdefender vulnerability researcher Ionut Cernica discovered that the Facebook Login feature could have been abused to impersonate users on websites where they had previously registered an account.
For the attack to work, the attacker needed to identify an email account used by the targeted individual to sign up on a website that allows social logins. However, the condition was that the targeted email address had not been used to register a Facebook account.
As Cernica demonstrated, the attacker could have created a Facebook account with the victim’s email address, and then swap that email address with one they controlled in the Facebook settings panel. The attacker could have used their own address for the email confirmation process and then switch them back to make the victim’s address the primary email again.
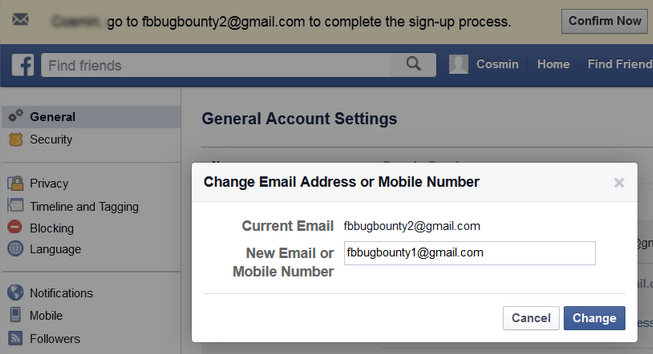
Using the Facebook account that had the targeted user’s address set as the primary email, the attacker could have used the social login feature to sign in to the account where the victim had used that email address.
“This is a serious vulnerability – it allows attackers to login on most websites that feature Facebook Login,” Cernica said. “This means an attacker can make payments on the user’s behalf on an e-commerce site, for instance.”
The issue was reported to Facebook on March 31 and the social media company informed the researcher that the vulnerability had been patched on April 14.
While Bitdefender has classified the issue as a serious vulnerability, Facebook believes the risk was low considering that the bug was not easy to exploit on a large scale. Furthermore, Facebook noted that an attack required the creation of a fake account, which its systems can quickly detect and remove.
Bitdefender noted that it’s often not difficult to find a user’s email addresses, but Facebook pointed out that it might not be easy to determine which address has been used for a certain online service.
“This bug was difficult to exploit at a large scale and didn’t involve compromising Facebook accounts or company networks. However, we appreciate Ionut’s coordination with our bug bounty team to quickly resolve this issue,” a Facebook spokesperson told SecurityWeek.
Although it assigned the flaw a “low risk” exploitability rating, Facebook awarded the researcher $5,000 based on the potential risk.
The company’s guide on using the Facebook Login system includes recommendations for developers on how to safely merge accounts on a website or app if someone attempts to use Facebook Login with a different email address.
Related: Researcher Finds Malicious Web Shell on Facebook Server
Related: Facebook Password Reset Flaw Earns Researcher $15,000














