For many months it was expected that privacy protections afforded to consumers by GDPR would also benefit the bad guys. It was feared that security researchers would no longer be able to track new bad domains through WHOIS data, and that spammers would rush to register new domains under new GDPR-enforced anonymity; and that spam would spike once GDPR became effective in May 2018. It hasn’t happened.
A new analysis from Recorded Future, combining spam volume data from Cisco’s research and domain registrations from its own data sets shows — if anything — the reverse to be true. Allan Liska, threat intelligence analyst at Recorded Future, told SecurityWeek, “In the first 90 days since GDPR has been enacted, spam has actually declined, even taking into account the normal seasonal slump that happens during the summer. But it’s not just spam volumes,” he said, “but there have also been fewer new domains registered in the spammy gTLDs that tend to have a lot of spam.”
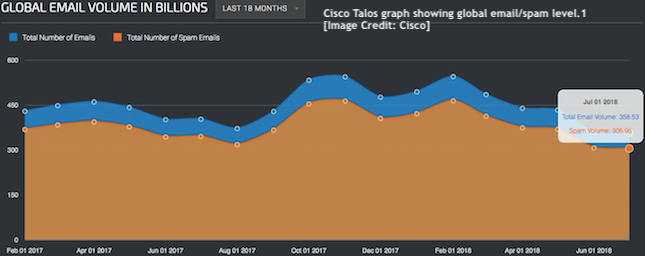
In raw figures, according to Cisco’s data, total email at May 1, 2018 stood at 433.9 billion messages, with spam accounting for 85.28% of all email. By August 1, 2018, the total email had fallen to 361.83 billion (probably helped by GDPR’s privacy requirements on email marketing) with spam making up 85.14%. Those figures show spam dropping from 370 billion messages in early May (pre-GDPR) to to 308 billion messages in August (post GDPR).
The reason for the drop is not clear. “I don’t have a good answer yet,” Liska told SecurityWeek. “It may be that the bad guys are sitting back and waiting to see how it all plays out before they decide on their path forward.” The last thing they will want to do is register a bunch of domains, “and then everything gets worked out between ICANN and the GDPR — and the security researchers have full access to that WHOIS data again. So, the beginning groups may be in a wait and see mode.”
Another possible cause for the non-appearance of the expected post-GDPR spike in spam is that the spammers don’t think anything has really changed. It’s true that most registrars have enacted the GDPR restrictions, so WHOIS data is now unavailable. “But there’s no slackening in the researchers use of other methodologies to track spam domains,” said Liska. “IP tracking, for example: jumping from IP address to IP address through domain algorithms. That type of capability is still being used by the researchers, and researchers are relying more heavily on such techniques.”
Possibly arguing in favor of a ‘wait and see’ approach by the spammers is a corresponding drop in new domain registrations in the more spammy gTLD domains. “Spamhaus keeps track of the top 10 most malicious domains,” explained Liska, “and all of the gTLDs saw a strong drop in activity post GDPR. That’s a bit unusual and you would think that if nothing’s changed from the bad guys’ point of view, then they would continue registering these bad domains — but that doesn’t seem to be the case.”
The implication of this lack of activity in the spammy gTLDs is that spammers aren’t currently planning any major new spam campaigns for the immediate future.
The best possible cause for this dip in spam — which cannot be fully explained by the summer recess — is that defenders are finally winning the battle against spam. New techniques and technologies — especially machine learning algorithms — are getting better at recognizing and blocking spam. If the spammers aren’t making money, they’ll move on to something different.
“We’ve seen a big drop in dot-biz registrations,” commented Liska. Dot-biz has long been considered a particularly spammy gTLD, with around 40% of dot-biz domains considered to be spam domains. That still means that 60% of these are genuine, making it impossible to simply block all dot-biz domains. However, with machine learning working to probabilities rather than binary decisions, dot-biz plus a few other lesser flags could rapidly identify and block spam.
Where machine learning is particularly useful, added Liska, is in identifying new phishing and watering hole domains. This would include typosquatting domains and cybersquatting domains. The former would include look-alike spellings and a range of country suffixes that could be mistyped. Liska gave an example of misspelled domains. “Take Wells Fargo,” he said. “There are numerous ways that could be misspelled while still looking the same. The letter ‘o’ could be changed to the numeric zero (Wells Farg0) or the lowercase ‘ls’ could be changed to uppercase ‘Is’ (WeIIs Fargo).”
Other examples include registering a well-known brand name in a country-specific domain — such as dot-cm (Cameroon), dot-co (Columbia), dot-om (Oman) and dot-ne (Nigeria). Each suffix is only a short typo from the major dot-com and dot-net suffixes. Criminals register big brand names in these country domains and wait for people to make a typing mistake to visit their sites.
Cybersquatting domains do not rely on the user making an error while typing the domain, but on appearing to be a genuine company URL. Bad actors will sometimes add a new company tag line or use a new product and register it as a new domain. An example can be seen in the 2017 registration of ‘cybfx.co.uk’ by a resident of Beijing immediately after the Clydesdale Bank introduced its new online cyber foreign exchange service called CYBFX. It wasn’t until February 14, 2018 that the UK domain registrar declared it an ‘abusive registration’ and transferred ownership to Clydesdale Bank.
“There are hundreds of thousands of new domains registered every day,” commented Liska. “It’s almost impossible for a human to look through all of those domains to find bad things. Machine learning helps us find new registrations that are meant to look like well-known sites.”
“I’ve been in this industry for almost 18 years,” Liska told SecurityWeek, “and for 18 years we’ve been fighting spam and losing. I’d love to see that this dip is the beginning of a decline in spam; but my feeling is the bad guys are figuring out how to regroup, and assess the situation. They’ll figure out a way round any problems, because that’s what they always do. At some point we’ll probably see a new uptick in spam volumes again, so we better just enjoy the lull while we have it.”
Boston, Mass.-based Recorded Future, founded in 2009, raised $25 million in a Series E funding round led by Insight Venture Partners in October 2017 — bringing the total funding raised to $57.9 million.
Related: Spam Rate Hits Two-Year High
Related: State of Email Security: What Can Stop Email Threats?
Related: As EU Privacy Law Looms, Debate Swirls on Cybersecurity Impact















