Identity and information security solutions firm Entrust, on Tuesday announced updates to its Entrust IdentityGuard Mobile Smart Credential offering.
Its new IdentityGuard Mobile Credential 2.0 helps protect against potentially fraudulent transactions triggered by malware, by giving users the ability to authenticate enterprise, web or cloud transactions via a mobile channel.
“By moving transactions out-of-band to the mobile channel, users cannot only review the exact details of the transaction they are about to perform, they can also confirm and approve them in real time from the convenience of their phone,” Entrust explained.
 Additionally, with the new mobile smart credential, enterprises and banks can streamline business processes by eliminating requirements for in-person, paper-based signatures or desktop-bound digital signatures, Entrust said. Even documents requiring legally-binding, digital signatures can be signed directly from a phone or tablet.
Additionally, with the new mobile smart credential, enterprises and banks can streamline business processes by eliminating requirements for in-person, paper-based signatures or desktop-bound digital signatures, Entrust said. Even documents requiring legally-binding, digital signatures can be signed directly from a phone or tablet.
“Today’s financial institutions, enterprises, and governments need to be ready to address the exponential growth of mobile device adoption and begin better leveraging this new technology to address day-to-day business needs,” said Entrust President and CEO Bill Conner. “We know mobile architecture is significantly more secure than traditional PCs, making it an ideal avenue for convenient, secure digital signing of legally-binding documents and approving of critical transactions.”
“Authenticators such as passwords or hard tokens simply don’t provide the same level of protection that one can find by using smart credentials on a mobile device. Additionally, paperwork slows down the process, frustrates employees and customers, and can even provide a roadblock to receiving revenue,” Conner added. “By using a mobile device with a smart credential, companies can protect sensitive transactions of all types by stopping the transaction midstream and sending it to a mobile device for verification.”
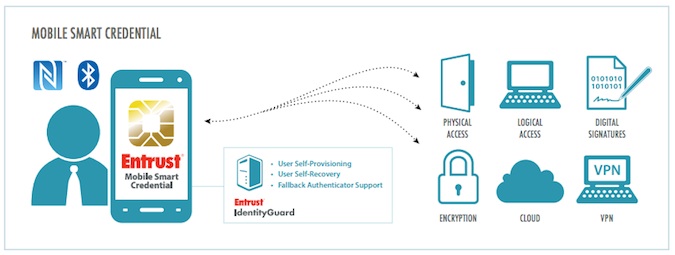
As an additional benefit, mobile identities eliminate the reliance on Java, Flash or desktop device drivers, which have proven to be extremely vulnerable, and a popular attack vector for cybercriminals.
Additionally, the Entrust IdentityGuard Mobile Smart Credential 2.0 SDK lets customers embed identity-based security into their own mobile applications for mobile authentication.
Entrust IdentityGuard Mobile Smart Credential 2.0 will continue to offer existing capabilities including authenticators for physical, logical and cloud access, as well as out-of-band transaction verification and NFC and Bluetooth integration, the company said.















