Critical vulnerabilities in enterprise virtual private network (VPN) solutions from Palo Alto Networks, Fortinet and Pulse Secure allow attackers to infiltrate corporate networks, obtain sensitive information, and eavesdrop on communications, researchers warn.
Orange Tsai and Meh Chang of the research team at security consulting firm DEVCORE told SecurityWeek that they set out to find the most serious types of vulnerabilities in these products — namely unauthenticated remote code execution — and they claim to have achieved their goal.
The vulnerabilities were identified in Palo Alto Networks GlobalProtect, Fortinet FortiGate (FortiOS), and Pulse Secure’s Pulse Connect Secure (PCS) and Pulse Policy Secure (PPS). Each of the impacted vendors has released patches and advisories for their customers.
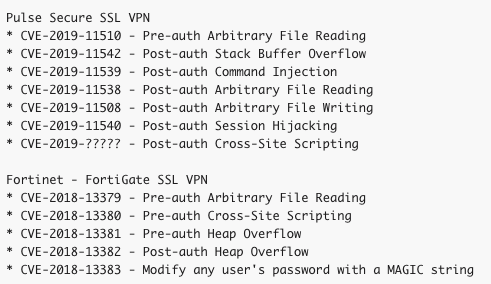
In the Pulse Secure products the researchers said they identified a total of 7 vulnerabilities, including an arbitrary file read issue that can be exploited without authentication, and post-authentication stack buffer overflow, command injection, arbitrary file read/write, session hijacking, and cross-site scripting (XSS) flaws.
Orange Tsai told SecurityWeek that they combined the unauthenticated file read issue (CVE-2019-11510) with a post-authentication command injection bug (CVE-2019-11539) to achieve remote code execution.
In the case of the FortiGate SSL VPN, the researchers discovered arbitrary file read, XSS and heap overflow flaws that can be exploited without authentication, as well as a post-authentication heap overflow, and a weakness that can be exploited to modify any user’s password. They chained an unauthenticated arbitrary file read issue (CVE-2018-13379) with a post-authentication heap overflow (CVE-2018-13382) to achieve remote code execution.
The researchers plan on detailing their findings at the upcoming Black Hat USA and DEFCON conferences next month, but they have already shared some details and proof-of-concept (PoC) code for the remote code execution vulnerability affecting the Palo Alto Networks products. During their analysis of the GlobalProtect flaw, they noticed that the product had been used by Uber on 22 of its servers.
“An attacker can gain the root shell on the target SSL VPN system with no authentication required! The only thing he needs to do is to send several malicious/crafted requests,” Orange Tsai said about the vulnerabilities in an email.
He says an attacker can exploit the vulnerabilities to infiltrate an organization’s intranet and access internal services storing sensitive data, they can obtain personal information and passwords belonging to employees, and they can extract private keys that would allow them to decrypt HTTPS connections and eavesdrop on communications.
“Moreover, we propose a new method to hack back all the VPN clients! With our research, we can not only compromise the corporation network but also the employee’s personal laptop,” the researcher explained.
Pulse Secure told SecurityWeek that it released patches on April 24, roughly one month after being notified.
“Pulse Secure is not aware of any exploit of this vulnerability,” Pulse Secure said. “Users that have enabled logging of unauthenticated access to their appliance would know if a breach has occurred by looking at the system logs. Audit logging is a security best practice, as a vulnerability scanner would not have detected this vulnerability. It would have been very difficult to exploit this vulnerability because it requires in-depth knowledge of the Pulse Connect Secure product, as well as a specially crafted URI (Uniform Resource Identifier) string and an untraditional combination of steps.”
Fortinet fixed the flaws with FortiOS updates released in May. The company has published individual advisories for each of the vulnerabilities.
Palo Alto Networks said it identified the vulnerability internally before it was contacted by the researchers and released patches. However, the company only released an advisory this month, after the experts made their findings public.
Related: BlackBerry Cylance Downplays, Patches Antivirus Bypass














