Many of the applications installed on enterprise mobile devices expose potentially sensitive data by failing to properly secure the connection between the app and backend servers, enterprise mobile security firm Appthority warned in a report published on Wednesday.
An analysis conducted by researchers has shown that the attack vector, dubbed by Appthority “HospitalGown” due to similarities with hospital gowns which typically expose the patient’s backside, affects more than 1,000 iOS and Android apps installed on enterprise devices.
The attack relies on vulnerabilities in the mobile application’s architecture and infrastructure, and it requires finding weaknesses in the communications between the app and server-side components.
Enterprise applications often connect to a backend database that stores user and other information. One of the tools used to analyze and mine the data stored on backend servers is the Elasticsearch engine. Given its popularity in large enterprises, Appthority has decided to focus its investigation on apps that use Elasticsearch.
While the connection between the mobile app, its API and the Elasticsearch data store is typically secure, the Elasticsearch server is often exposed to the Internet. Appthority has identified more than 21,000 open Elasticsearch servers connecting to the 1,000 apps exposed to HospitalGown attacks. These servers exposed a total of 43 terabytes of data.
In addition to allowing access to data via unprotected Elasticsearch servers, the HospitalGown attack can leverage the way apps interact directly with the server. For example, researchers pointed out that an attacker could reverse engineer a mobile app to obtain the IP address of the Elasticsearch server, scan the Internet or the victim’s network for other vulnerable servers, and intercept traffic going to the server.
Appthority’s analysis focused on 39 popular iOS and Android applications found on enterprise mobile devices, such as ones used for agriculture, content management, dating, education, games, news, office productivity, travel, and mobile security and access management.
These apps were found to leak 163 gigabytes of data containing roughly 280 million records, including personally identifiable information (PII) and corporate data. Appthority believes the exposed data can be useful to launch further attacks, conduct fraud, or it can be sold to other malicious actors.
“Weakly secured backends leveraged by mobile app developers create opportunities for big data leaks and a signi cant increase in the risk of data misuse for spear phishing, brute force login, or other types of PII-based attacks for enterprises with employees, partners, or customers that use or have ever used these apps,” Appthority said in its report.
One of the analyzed apps was Pulse Workspace, which is used by enterprises, government agencies and service providers. While the application protected frontend Elasticsearch access using an API, the backend exposed Pulse Workspace customer data, including names, contact information, PIN reset tokens, and device information. The vendor patched the vulnerability after being notified by Appthority.
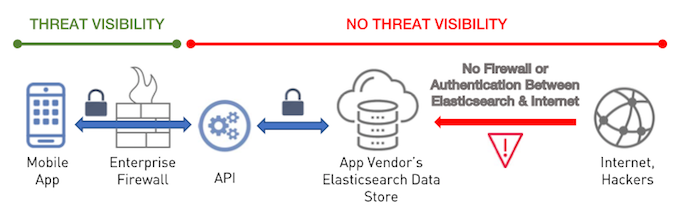
According to experts, HospitalGown attacks can be highly problematic as they are not easy to detect and prevent without comprehensive security and visibility mechanisms in place, and addressing the underlying vulnerability can prove difficult, especially if the weakness is exclusively on the backend.
Related Reading: Many Mobile Apps Unnecessarily Leak Hardcoded Keys
Related Reading: What’s Up with Your Mobile Apps? Identifying and Mitigating Digital Risk














