While Fraudsters May be Equal in Terms of Rank, when it comes to Sophistication – they are not. The Higher the Sophistication Level of Individuals, the Fewer they are in Numbers
Much like the cantina on Star Wars’ desert planet Tatooine, the underground economy is a hub of criminal activity and trade. Fraudsters from all over the world congregate to trade stolen record sets of credit cards, personally identifiable information and online banking credentials. Law enforcement has called it “organized crime” and indeed it is very organized – but not in the sense of The Godfather. Although these crime forums do have administrators, they’re not Dons whose bidding must be obeyed by everyone beneath them in the social hierarchy.
The underground is organized in the same way that eBay is organized – there’s a set of laws between buyers and sellers that must be followed, a set of services designed to improve the security of all parties (escrow services, for example) as well as a dispute resolution process. While there are certain statuses such as a “verified vendor” status that can be obtained, and while hierarchy may exist within the groups that are represented in the forums, all members (as long as they are not a ripper) are considered equal.
While fraudsters may be equal in terms of rank, when it comes to sophistication – they are not. Much like in the hacking community, the higher the sophistication level of individuals, the lesser they are in numbers. Most of the “hackers” out there are script kiddies, who are only sophisticated enough to follow a set of actions that were invented by someone more sophisticated. The same applies to fraudsters. Naturally, there are less “big fish” (or should I say “big phish”) in the ocean than “little fish.”
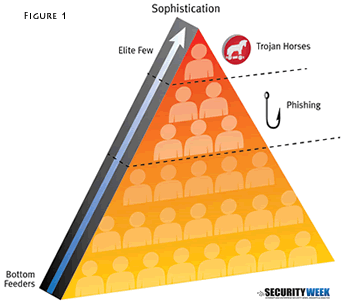 Imagine a pyramid where the most sophisticated fraudsters are at the top (see Figure 1). These are the fraudsters on the cutting edge of fraud, coding their own malware, looking for ways to crack the security of EMV (chip cards). At the bottom of the pyramid lie the least sophisticated fraudsters, who scavenge small forums for free credit cards and rip off other fraudsters for nickels and dimes. For each fraudulent activity, such as cloning the magnetic stripe off credit cards or stealing money through online banking services, you can draw a line on the pyramid. Anyone above the line is sophisticated enough to participate in this activity, while the ones below it are not. In other words, the line represents the “bar of entry” into the true criminal underground.
Imagine a pyramid where the most sophisticated fraudsters are at the top (see Figure 1). These are the fraudsters on the cutting edge of fraud, coding their own malware, looking for ways to crack the security of EMV (chip cards). At the bottom of the pyramid lie the least sophisticated fraudsters, who scavenge small forums for free credit cards and rip off other fraudsters for nickels and dimes. For each fraudulent activity, such as cloning the magnetic stripe off credit cards or stealing money through online banking services, you can draw a line on the pyramid. Anyone above the line is sophisticated enough to participate in this activity, while the ones below it are not. In other words, the line represents the “bar of entry” into the true criminal underground.
Consider this comparison to the differences between Trojans and phishing today. The line representing the use of banking Trojans is typically higher than the line representing phishing, as phishing attacks require less sophistication and their “bar of entry” is lower. Therefore, the number of fraudsters sophisticated enough to launch a phishing attack is higher than those capable of setting up a botnet to distribute malware. That is the reason why phishing is still relevant in a world where Zeus and SpyEye exist.
One of the effects the underground economy has on the actual ability for one to commit fraud is that it lowers the bar of entry for each activity on the pyramid. By having fraudsters who specialize in specific areas instead of the entire process, by creating a market of commodities and services and by the sharing of knowledge, less sophisticated fraudsters can join in on the fun that would have been out of their reach otherwise. A fraudster who lacks the sophistication to hack into a merchant’s site to get a list of credit cards could simply buy them from someone who is. A fraudster who lacks the sophistication to build a scam page for his phishing attack can simply get a free phishing kit from one of the multiple repositories available.
Over time, the tools and techniques that were solely used by the “big fish” trickle down through the pyramid. The ability to conduct a phishing attack became more accessible when they were bundled into kits and distributed for free. The same holds true for Trojans. While some versions of the Zeus banking Trojan still cost several thousands of dollars, the older versions are available free of charge. New services and tools are constantly being developed by fraudsters, continuously driving the bar of entry for various fraudulent activities lower and lower.
Fortunately, this model doesn’t only pose risks to organizations targeted by fraudsters – but opportunities as well. Anti-fraud professionals can use the current model of the underground to disrupt fraudster activities and reduce fraud levels, at least temporarily, even when dealing with a sophisticated issue such as automatic money transfers executed by Man-in-the-browser (MITB) scripts.
When issuing a fraudulent transaction automatically, Man-in-the-browser modules for Zeus and SpyEye are programmed to auto-fill a transaction form based on the name or location of each field in the form. A simple addition to a bank’s website, one that would generate random field names as well as place hidden fields in a random order, could thwart the Trojans’ ability to make fraudulent transactions.
“But that doesn’t really solve anything. The next version of Zeus/SpyEye could easily circumvent that,” you must be thinking – and you would be right. This is far from being a solution to the woes of Man-in-the-browser attacks. However, if you consider that there are more unsophisticated fraudsters than there are sophisticated ones, only the latter group would have the advanced skills required to develop a workaround to this relatively quickly. As most fraudsters use kits containing older Trojan versions, they would essentially be left in the dust.
Even if only a temporary fix (and far from being bulletproof), it could still affect the bottom-line and reduce fraud losses perpetrated by banking Trojans. By the time the new version would be widely available, the ante could be upped once again. These cat and mouse games can also help ensure that Trojan developers are forced to keep their focus on retaining the existing abilities of their malware (in the case of Man-in-the-browser, the ability to transfer funds automatically out of a victim’s accounts) rather than focus on developing new and more innovative fraud tools.
These types of temporary “disruptions” can also be applied to other activities that are much less sophisticated. Changing the data required to authorize a transaction or even simply logging into the online banking service may render many phishing kits unusable, as they will not obtain all the required information. Many fraudsters will be able to easily add the required fields, but there will also be a “layer” in the pyramid who would just go target someone else instead.
The question is how many fraudsters from the bottom of the pyramid target the bank. If a financial institution is considered relatively hard to defraud and it is almost exclusively targeted by sophisticated fraudsters, these actions will have very little effect. However, if among the attackers there are many unsophisticated fraudsters, these disruptions could have positive results. Considering that even minor changes in websites require resources, especially websites of large organizations such as financial institutions, the first step would be to assess the sophistication of the attackers.
In the world of fraud mitigation, financial institutions mostly play on the defensive. Every soldier will tell you that a good defensive tactic would be to change things up a bit from time to time. The effects may only be temporary, but throwing the enemy off guard, even if only for awhile, may be the difference between win or lose.















