The DHS on Thursday announced Cybersecurity Performance Goals (CPGs) to help organizations — particularly in critical infrastructure sectors — prioritize cybersecurity investments and address critical risks.
The CPGs were developed by the DHS’s Cybersecurity and Infrastructure Security Agency (CISA) in collaboration with NIST based on feedback from partners in public and private sectors.
They are a result of the White House’s efforts to improve the US’s cybersecurity, and the DHS says the goals are unique in that they address risk not only to individual entities, but also the aggregate risk to the nation.
CPGs are a set of cross-sector recommendations that can be highly useful to an organization in securing its systems, but they are voluntary — organizations are not required by the government to use them. They are designed to complement NIST’s Cybersecurity Framework.
CPGs are described as baseline cybersecurity performance goals focusing on a prioritized subset of IT and OT security practtices that can help organizations significantly reduce the likelihood and impact of risks and adversary techniques. In addition, they can serve as a benchmark for measuring and improving cybersecurity maturity.
CPG categories include account security, device security, data security, governance and training, vulnerability management, supply chain / third party, and response and recovery.
These categories cover detection of unsuccessful login attempts, password-related issues, MFA, identity and access management, hardware and software approval processes, disabling macros, asset inventories, device configurations, mitigating risks associated with unauthorized devices, logging, and sensitive data protection.
They also cover cybersecurity leadership, training, mitigating known vulnerabilities, deploying security.txt files, addressing internet exposure risks, third-party validation of cybersecurity control effectiveness, vendor security requirements, supply chain incident reporting, incident response plans, and system backups.
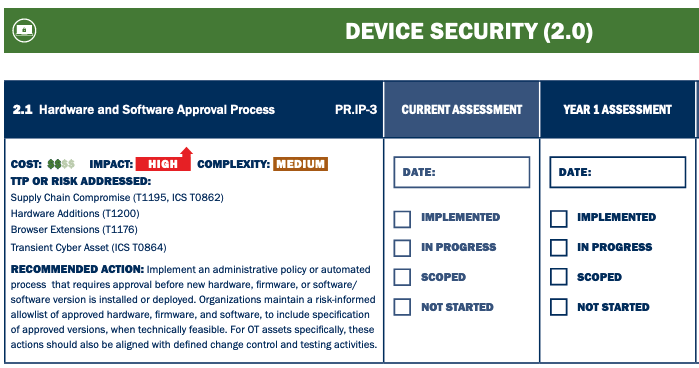
Organizations have been provided a checklist that can be used to prioritize goals based on cost, complexity and impact. CISA has also set up a page on GitHub where organizations can submit feedback.
While industry professionals applaud the initiative, some have pointed out some issues. Ron Fabela, CTO and co-founder at SynSaber, noted that the CPGs come with some challenges specific to OT systems.
“Top down guidance from CISA or other agencies are often hard to apply and measure across such large and diverse critical infrastructure sectors. Difficult to measure criteria for success are left to those doing the measurement. There’s also the tension between performance based goals that are not overly prescriptive (as they should be) and guidance that is non-applicable to the audience,” Fabela said.
“Even within this report and checklist asset owners are left analyzing what is applicable and feasible. Many of the goals have unique callouts for ‘OT’ and plenty of caveats such as ‘where technically feasible’, a phrase that has been the bane of effective cybersecurity governance of ICS,” he added.
Chris Gray, AVP of cybersecurity at Deepwatch, noted that while the CPGs are a subset of the controls present in NIST’s Cybersecurity Framework, they can still be useful.
“There is little new here other than some additional classification around IT/OT and saving the agency/group/service from having to go through the process of selecting and prioritizing controls. That is absolutely a help. Some might view it as an ‘easy button’ or ‘lazy’, but in industries where there may not be a lot of security expertise, any help is good help. In addition, these controls SHOULD help establish a minimum baseline of expected activities,” Gray said.
Related: White House Unveils Artificial Intelligence ‘Bill of Rights’
Related: White House Adds Chemical Sector to ICS Cybersecurity Initiative
Related: Biden Signs Executive Order on US-EU Personal Data Privacy
Related: Industry Reactions to Govt Requiring Security Guarantees From Software Vendors














