
We are likely to see Russian state sponsored attacks escalate as the West continues to increase sanctions and support Ukraine
The eyes of the world are focused on the war in Ukraine. As expected, Russia has targeted Ukraine with cyberattacks first, and much of the West is wondering when Russia will also retaliate against countries supporting Ukraine. Most agree that some attacks are already in progress, and the attacks against western entities are sure to escalate as the war continues and more sanctions are put in place.
The first wave of companies targeted by the Russian state, and threat actors it supports, will be those that suspend Russian operations or take direct action to support Ukraine. Information operations and subversion against these companies will likely ensue. In the event of Russian cyberwarfare, reviewing the industries, styles, and objectives of their attacks can help organizations to prepare and implement more robust defenses. These defenses include actions both inside and outside an enterprise’s perimeter.
Industries Targeted by Russian Cyberattacks
While we anticipate that companies openly assisting Ukrainians will be prioritized for Russian cyber attacks, it’s useful to be aware of the industries that have been targeted in the past year. You will note that governments, infrastructure, and technology services have consistently been the prime targets.
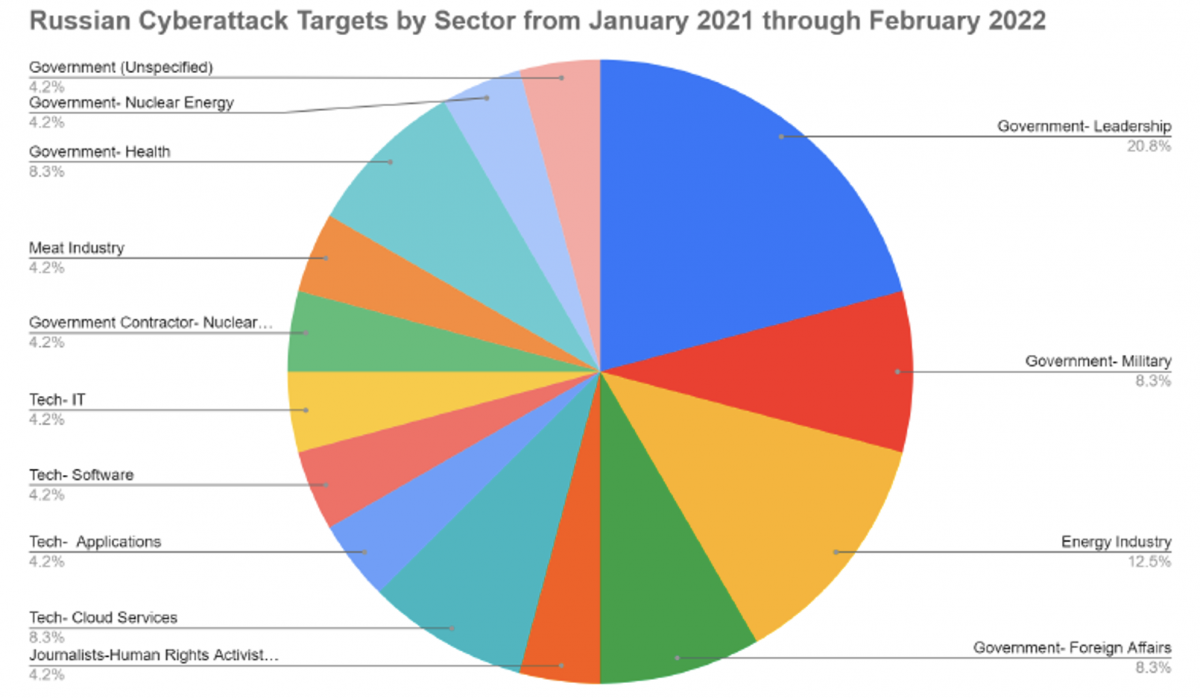
Graphic 1: Chart illustrating a sample of Russian cyber actors’ targets from January 2021 through February 2022, according to CSIS.
Common Types of Cyber Attacks
Russia-led cyberattacks have increased since the Russian invasion of Ukraine, and Russian cyber threat actors will likely use one or more of the following means to retaliate against companies and people on opposing sides of the war:
● Ransomware – The most used type of cyber threat to attack private industry since 2021
● Email Phishing – A commonly used technique to gain access to privileged information and networks
● Credential Stuffing – Another commonly used technique, which largely targets C-Suite executives and gamers for access to their accounts to gain access to privileged information and for financial gain
While these attacks are not new, they are increasingly concerning. For context, the following Russian-based actors conducted cyber attacks against public and private sector targets from January 2021 through February 2022 according to CSIS:
● Russia’s Main Intelligence Directorate of the General Staff of the Armed Forces of the Russian Federation (GRU)
● Russia’s Foreign Intelligence Service (SVR)
● DarkSide (Russian speaking hacking group)
● REvil (Russian speaking cybercrime group)
● Conti (Russian speaking cybercrime group)
Objectives of High Profile Cyber Attacks By Russian Cyber Actors
The Russian government and Russian cyber criminals targeted private industry in multiple incidents over the past year. Historically, these APT actors have used common but effective tactics—including spear phishing, brute force, and exploiting known vulnerabilities against accounts and networks with weak security—to gain initial access to target networks. We believe there are three primary objectives that will drive Russian cyber actors, both criminal and government, to target those networks:
● Influence – This involves preparing a target for military or economic combat and creating a social media environment where non-Russian companies and entities look weak so that the Russian economic environment and Russian companies can look comparatively strong.
● Retribution – In response to the support of the Ukrainian resistance, ransomware could increase, and in some cases, it is possible that ransom will no longer be a means of resolution. Businesses that have withdrawn operations from Russia may be threatened with an attack unless they agree to resume Russian operations.
● Gain – As sanctions increase and expand, Russian corporations may choose to ignore global intellectual property laws and pay cyber threat actors to target non-Russian corporate IP, in a style similar to that seen with Chinese threat actors.
With these objectives in mind, the following is a 3-step, best practice approach to proactively defend organizations, facilities, and people and prevent them from being successful targets:
Step 1 – Influence: Conduct Open Source Monitoring to Identify and Combat Influence Campaigns and Ensure Sensitive IP Is Not Leaked or Compromised
● Conduct robust open-source and dark web monitoring, which may or may not include actor engagement, to determine the following:
-
- Is the reputation of your company being targeted with misinformation or disinformation?
- Has your intellectual property been stolen and posted for sale on the dark web or in private forums?
- Are Russian competitors stealing or attempting to steal and copy your sensitive IP?
Step 2 – Retribution: Monitor the External Attack Surface to Prevent and Detect Cyber Crime, Ransomware, and More Aggressive Computer Network Exploitation
● Conduct robust attack surface monitoring that includes, but goes beyond, vulnerability management and penetration testing
● Extrapolate IOCs to new attacker infrastructure that’s relevant for your organization conducting external threat hunting
● Conduct deep-dive Requests for Information (RFIs) so you can investigate more thoroughly potential threats hitting or escaping your firewalls
● Task intelligence and threat hunt teams to review malware, credential, and exploit samples in order to identify coverage gaps in the existing security technology stack
Step 3 – Gain: Increase Protective Focus on Key Personnel and Facilities by Conducting Thorough and Aggressive Online Investigations and Attribution
● Maintain a hardened online presence for all executives and reduce their public footprint and exposure
● Implement alerts when inauthentic social media accounts are created for executives and employees
● Fund or staff the ability to quickly attribute people threatening your executives or attempting to steal Intellectual Property through online solicitation or insider recruitment
● Conduct robust background checks on potential suppliers and employees originating from targeted companies and industries in Russia or with ties to Russia
● Implement a robust training and awareness program so employees can report suspicious behavior
Russia will try to inflict economic damage similar to the GRU-backed 2017 NotPetya attacks that resulted in worldwide revenue losses greater than $10 billion. Although Russia has not yet escalated cyberattacks– likely due to their focus on Ukrainian operations – we are likely to see Russian state sponsored attacks escalate as the West continues to increase sanctions and support Ukraine.














