Analysis of Ragnar Locker Ransomware that has been targeting the energy sector
The Ragnar group, operating Ragnar Locker ransomware, has been active since 2019 targeting critical industries and employing double extortion. In March 2022, the FBI warned that at least 52 entities across ten critical industry sectors have been affected. In August 2022, the group attacked Greek gas supplier Desfa, and subsequently leaked sensitive data it claimed to have stolen.
Researchers at Cybereason have analyzed the encryption process of Ragnar Locker.
On execution, Ragnar Locker does a location check. If the location is any country in the Commonwealth of Independent States (CIS), execution is terminated.
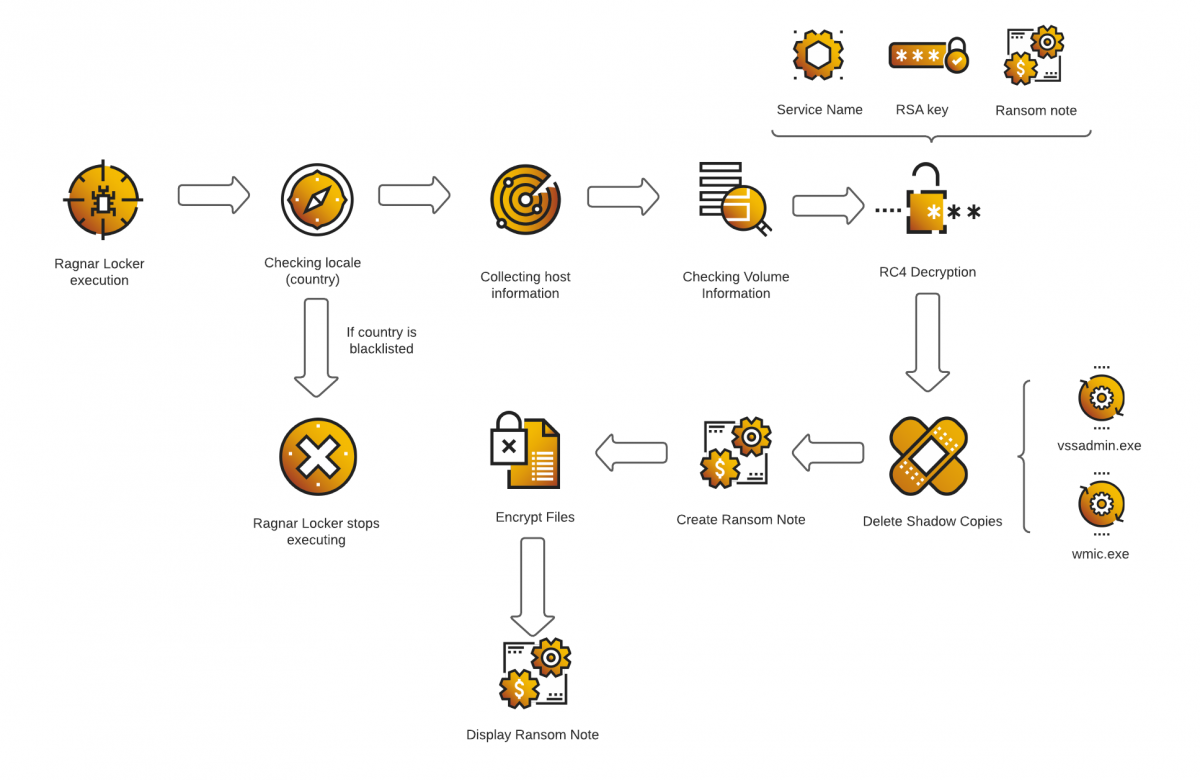
Ragnar Locker execution flow
It then collects host information, including the computer name and user name, and the machine GUID and Windows version. This data is concatenated and concealed by a custom hashing function. A new event is created using the combined hashes as the name. Ragnar Locker then seeks to identify existing file volumes using the Windows APICreateFileW.
A list of services embedded within the Ragnar Locker code is decrypted. This includes vss, sql, memtas, mepocs, sophos, veeam, backup, pulseway, logme, logmein, connectwise, splashtop, kaseya, vmcompute, Hyper-v, vmms, Dfs. If any of these are found as a running service, it is terminated by the malware.
The malware then decrypts an embedded RSA public key and prepares it for use. It decrypts the embedded ransom note and proceeds to delete any shadow copies of the host via vssadmin.exe and Wmic.exe.
In the analyzed sample, the ransom note adds, “Also, all of your sensitive and private information were gathered and if you decide NOT to pay, we will upload it for public view!” The Ragnar Locker data leak site on Tor (http [://] rgleaktxuey67yrgspmhvtnrqtgogur35lwdrup4d3igtbm3pupc4lyd [.] onion/) currently lists around 70 claimed victims.
The note demands a ransom of 25 bitcoins, but implies this could be negotiated if contact is made within two days. However, it warns that the ransom will double if there is no contact within 14 days, while the decryption key would be destroyed if no payment agreement isn’t reached within 21 days.
It also adds that the ransom figure has been tailored by the attackers based on the victim’s ‘networks size, number of employees, annual revenue’.
When the ransom note is ready, Ragnar Locker starts the encryption process. Exclusions include the files autoruns.inf, boot.ini, bootfront.bin, bootsect.bak, bootmgr, bootmgr.efi, bootmgfw.efi, desktop.ini, iconcache.db, ntldr, ntuser.dat, ntuser.dat.log, ntuser.ini, thumbs.db; specific processes and objects such as Windows.old, Tor Browser, Internet Explorer, Google, Opera, Opera Software, Mozilla, Mozilla Firefox, $Recycle.bin, ProgramData, All Users; and files with the extensions .db, .sys, .dll, lnk, .msi, .drv, .exe.
The filenames of other files are sent to the encryption function which encrypts the corresponding file and appends the suffix ‘.ragnar_[hashed computer name]’. After encryption, Ragnar Locker creates a notepad.exe process and displays the ransom note on the user’s screen.
The stolen data used in the double extortion process is exfiltrated continuously up to the point of encryption. Loic Castel, principal security analyst at Cybereason’s Global SOC told SecurityWeek, “In general, ransomware operatives doing double extortion always require full privileges on the network they are looking to encrypt.. Between the initial access phase (when they take control of an asset, for instance through spearphishing) and the encryption phase, they have access to many machines, which they can extract data from and send through exfiltration services / external domains.”
In a timeframe disclosed in the FBI alert, data exfiltration occurred almost six weeks after the initial access, and continued for about ten days before the encryption process began.
Ragnar Locker primarily targets firms within the critical industries sector. “Ragnar Locker ransomware actors work as part of a ransomware family, frequently changing obfuscation techniques to avoid detection and prevention,” warned the FBI in its March 2022 alert.
Related: EDP Renewables North America Discloses Data Breach
Related: Ragnar Locker Ransomware Uses Virtual Machines for Evasion
Related: French Shipping Giant CMA CGM Discloses Security Breach
Related: Hackers Demand $11 Million From Capcom After Ransomware Attack
















