Radware Debunks Myths About DDoS Attacks, Says That Size Doesn’t Matter and Smaller Attacks are Often Deadlier
DDoS attacks have made their fair share of headlines over years, most recently as hacktivists took down multiple Government Web Sites and Music industry sites in response to the takedown of file sharing site MegaUpload. But when it comes to DDoS attacks, the idea that massive bandwidth cyber attacks inflict the most damage to organizations isn’t always true. In fact, according to security experts at Radware, bigger problems usually come in small packages.
Released today, Radware’s “2011 Global Application and Network Security Report” shows that when it comes to DDoS attacks, size doesn’t matter and smaller attacks can cause more harm.
“While DDoS attack numbers are easy to understand and eye catchy in the news – they only touch on the tip of the iceberg and do not really explain what is happening during a DoS attack or give other organizations any insight,” noted Ron Meyran, Director of Product Marketing for Radware’s security division.
In its research, Radware challenges several myths about how distributed denial of service (DDoS) attacks are viewed. In particular, Radware challenges the belief that while a cyber attack may feel catastrophic at the time, most organization may never experience an intense attack.
 According to Radware, a smaller attack can cause more damage than DDoS attacks that gobble ten times the amount of bandwidth. To support that argument, Radware research shows that 76 percent of attacks were less than 1Gbps in bandwidth, with 32 percent less than 10Mbps. Only nine percent of attacks in 2011 were over 10Gbps. While these statistics come from a rather small sample size of 135 responses, it should at least point out the fact that organizations need to look beyond the traditional “scale-to-defend” mentality to protect against DDoS attacks.
According to Radware, a smaller attack can cause more damage than DDoS attacks that gobble ten times the amount of bandwidth. To support that argument, Radware research shows that 76 percent of attacks were less than 1Gbps in bandwidth, with 32 percent less than 10Mbps. Only nine percent of attacks in 2011 were over 10Gbps. While these statistics come from a rather small sample size of 135 responses, it should at least point out the fact that organizations need to look beyond the traditional “scale-to-defend” mentality to protect against DDoS attacks.
“The thinking goes that if the bandwidth is bigger, then the attack is more severe,” the report notes. “In fact, Radware’s ERT found that the type of attack is also significant. A much smaller HTTP flood on the application level may do more damage than a larger UDP flood on the network. When evaluating DoS attacks it is important to understand both the size and type of attack.”
Related Resource: The Business Case for Managed DDoS Protection
Other security myths Radware is attempting to debunk include:
• Firewalls or IPS alone can stop DDoS attacks – Despite being designed to provide network security, firewalls and intrusion prevention systems (IPS) are impacted by DDoS attacks. Often the firewall is the weakest link. Radware’s report shows that in 32 percent of DDoS attacks, the firewall or IPS became the bottleneck.
• Content Delivery Network (CDN) providers protect a business against DDoS attacks – The CDN occasionally can handle the less sophisticated, large-volume attacks by simply absorbing them (while the target customer will pay for that bandwidth, of course, as it was recognized as legitimate traffic). These random request techniques force CDNs to “raise the curtain” and forward all the attacks directly to the customer premise, in essence making the CDN act as a proxy unloading the attack traffic directly at the target servers.
• The core DoS attack mitigation strategy is to defend and absorb – Businesses can and should have the ability to be proactive in their mitigation steps to stop malicious traffic or Website degradation with a strategy for going on the offense. This changes the rules in which the attacker always has the edge, and instead, levels the playing field. This can be done by identifying the attack tool used as the vehicle to carry the attack campaign and expose and exploit its inherent weaknesses to neutralize the attack tool in a “passive”, non-intrusive way.
“As the cyber security landscape continues to change with each new wave of attacks, DoS and DDoS attacks are changing as well and will continue to target organizations with more gusto than even before,” said Avi Chesla, chief technology officer, Radware. “For example, Radware’s 2011 Global Application and Network Security Report proves that in the past two years all serious cyber attack campaigns include volumetric as well as the low and slow attacks vectors, both generated simultaneously.
“Most Internet sites are inherently vulnerable, making it a major challenge for the average organization to predict whether or not their site will be attacked and what the volume of that attack might be. The fates of their organizations depend on utilizing the most advanced defensive and offensive maneuvers against these determined cyber criminals, and understanding all the intricacies of the current attack landscape,” Chesla said.
Other Report Findings include:
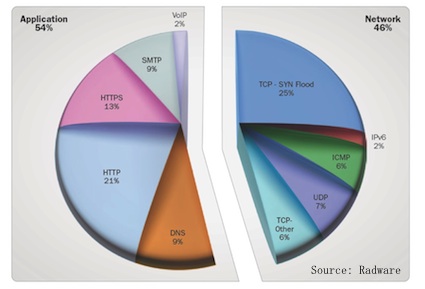
• 56% of cyber attacks were targeted at applications; 46 % at the network.
• Financial Services (28%), Government and eGaming (25% each) sites were targeted most.
• In half of the attacks, companies did not know why they were targets.
• ‘Hacktivists’ with a political or social agenda accounted for 22% of the attacks; 12% came from angry users; 7% from the competition and 4% wanted a ransom in exchange for freeing the website.
How can businesses protect against DoS and DDoS attacks?
Radware makes the following recommendations
1) Collect information about attacks such as type of attacks, size and frequency. Use the correct measures for the attack type. For example, the proper measurement for UDP floods is in bandwidth and PPS, while the measurement scale for HTTP floods is in transactions per second, concurrent connections, and new connections per second. The UDP flood may seem larger and more dangerous, but the HTTP connection-based attack can cause more damage with much less traffic than the UDP attack.
2) Perform risk analysis at the business level to determine the budget you should allocate to improve your business resilience against DDoS attacks.
3) For bandwidth saturation attacks, make sure your service provider can mitigate volumetric attacks that may saturate your bandwidth.
4) For application attacks, deploy anti-DoS and network behavioral technologies on site.
5) Have a consolidated or “context aware” view into enterprise security with a security event information management (SEIM) system.
6) Education and internal security policies are important defense tools, too. Regularly refresh technical skills and practical experience within the security group; but also help employees be aware of how hackers can exploit opportunities throughout the enterprise, especially in the age of ‘bring your own device’.
Summary
In February 2011, Arbor Networks revealed that DDoS attack Size broke 100 Gbps for first time; up 1000% Since 2005 and revealing a sharp escalation in the scale and frequency of DDoS attack activity on the Internet with many high profile attacks launched against popular Internet services and other well known targets. Traditional, massive-scale DDoS attacks can’t be ignored and need to be included in a any solid DDoS defense plan. Organizations need to open their eyes to defense strategies that go beyond the ability to scale and protect against massive bandwidth-hogging attacks, and be ready for other attacks such as application attacks.
In 2011 DoS attacks became much more organized, professional and complex , with attackers using as many as five different attack vectors in a single attack campaign. “No one point security tool could effectively block this sophisticated multi-level type of attacks,” Radware says. “What is needed is a cocktail of techniques that together provide full protection. “
“Nowadays, it is frighteningly easy for attackers to execute a DDoS attack. Botnets comprised of thousands of compromised PCs can be rented cheaply, and software capable of automating attacks can be acquired readily on the underground market,” writes Ram Mohan, EVP and CTO at Afilias and a regular SecurityWeek contributor. “A distributed denial of service attack is every business’s worst nightmare. One minute, everything is ticking along as normal. The next, your infrastructure is hit by a tsunami of spurious traffic from across the Internet. Legitimate users find themselves locked out, your ability to do business online grinds to a halt, and there’s not a great deal you can do about it – unless you prepare ahead of time.”
The full report can be found here.
Related Resource: The Business Case for Managed DDoS Protection













