Data Security: The Currency of Business Success. Start Building its Reserves Now!
We live in an age where technology is so easily accessible that data may be the most valuable currency that companies and individual consumers have to protect. Organized cybercrime is well-funded and has become increasingly sophisticated. According to the “2010 Identity Fraud Survey Report” by Javelin Strategy & Research, over 11 million adult consumers fell victim to identity fraud in 2009, up from nearly 10 million victimized in 2008.
Here are some of the most common fraud methods used by criminals to steal personal data today:
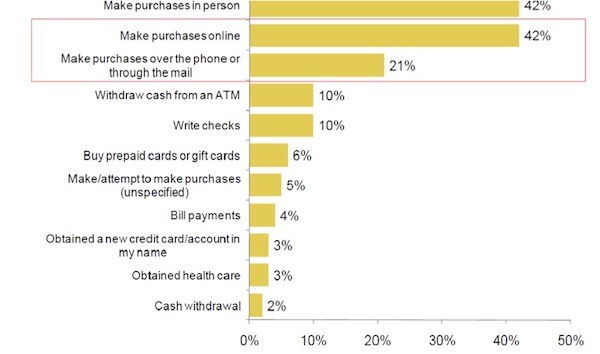
Source: © 2010 Javelin Strategy & Research “2010 Identity Fraud Survey Report”
Consumer-facing fraud (fraud that doesn’t include insider or employee fraud) costs retailers $100 billion a year, according to the “2009 LexisNexis True Cost of Fraud” study.
Companies need to evolve with the times. In this challenging economy, it is easy to make this a technology problem, and turn inwards to address the most burning topic at the moment. With this approach, companies get lost in the details, often missing the big picture and the opportunity to take a more holistic, business-minded approach to security. Companies should remember that compliance does not equal security! It is essential to step back and examine how to best meet business objectives, while taking into account the multifaceted environment that now encompases corporate risk. Every organization has the opportunity to examine internal processes and recognize the gaps in loss prevention (LP), information security, privacy, legal, business continuity, disaster recovery, and data security compliance.
If collecting and storing a particular data element puts your organization at risk because of the regulations that surround it, ask the tough questions:
Do we really need this data to conduct business?
Is there an alternate approach we could take?
For sensitive data that is business-critical, ask to limit the amount kept on file and narrow the scope of those with access.
After due diligence, consider technology. By taking this approach, businesses are better positioned to leverage a common set of tools and processes across the organization rather than falling into the trap of pursuing different tools to address different security concerns. It is easy to end up with an infrastructure that is expensive, unmanageable, and less secure because of gaps in between processes and tools, which creates opportunities for compromised security.
Specific to the retail environment, merchants have to continuously re-examine their current security infrastructure and approach to protecting cardholder data. They understand that PCI DSS (Payment Card Industry Data Security Standard) compliance does not equal security and continue to build security into their business process. Specifically, merchants can significantly elevate their efforts in protecting sensitive cardholder’s data by accelerating their efforts and focus on three areas:
Point to Point Encryption – Addresses the issue of protecting data in flight.
• Current buzz word in the market because merchants are interested in reducing the “PCI in scope” components
• Encrypts the data at the device level; decrypts upstream (corporate headquarters; gateway; processor)
Tokenization – Addresses the issue of protecting data at rest.
• Replaces the credit card number with another value that is not derived from the card itself
• Typically happens post authorization, as part of that process
• Strategy for taking back-end systems “out of scope” for PCI
• Represents and opportunity for merchants to shift their risk to a third party
• Depending upon the tokenization scheme, the amount of re-work can be minimal for the merchant
• Allows merchants to continue to utilize their current business processes with minimal risk (returns; charge backs; analytics, etc.)
Chip and Pin
– Addresses the inherent flaws in the mag stripe card product
• Technology is 15 years old – debate is on if there is something newer to leapfrog this technology
• Based on a two factor authentication strategy – customer has something that is known (card with chip technology) and something that only they know (pin)
• Consumer will likely assume fraud liability in this scenario (brands/banks assume they have been negligent in protecting their pin)
– Does not negate the PCI DSS requirement to protect cardholder data
Companies need to be aware of all methods by which important data elements come into the organization, which systems are passed through, where the data is stored, and who can access it, and they need to have the appropriate controls in place to monitor and protect the data. Without a doubt, there is a significant technology component, but data security starts with business processes – if it doesn’t make sense at the business level, the culture will never change, and it will not be sustainable.














