Cybersecurity company Darktrace issued a statement on Thursday after it was named on the leak website of the LockBit ransomware group.
“Earlier this morning we became aware of tweets from LockBit, the cyber-criminal gang, claiming that they had compromised Darktrace’s internal security systems and had accessed our data. Our security teams have run a full review of our internal systems and can see no evidence of compromise,” Darktrace said.
“None of the LockBit social media posts link to any compromised Darktrace data. We will continue to monitor the situation extremely closely, but based on our current investigations we are confident that our systems remain secure and all customer data is fully protected,” it added.
The statement was issued after a post on LockBit’s leak website seemed to suggest that the ransomware group had targeted Darktrace. The post suggested that data was stolen from Darktrace and that the cybercriminals were asking for a $1 million ransom.
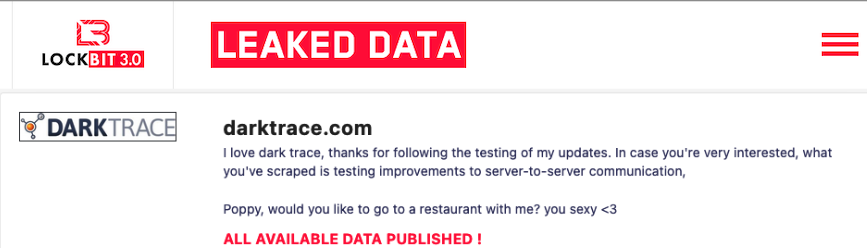
However, it appears that Darktrace was not hacked — or even targeted — by LockBit. Instead, the entry on the LockBit leak website apparently comes in response to a recent Twitter post from Singapore-based threat intelligence firm DarkTracer, which is not related in any way to Darktrace.
“The reliability of the RaaS service operated by LockBit ransomware gang seems to have declined,” DarkTracer said on Wednesday, referring to junk data being posted on the LockBit leak website.
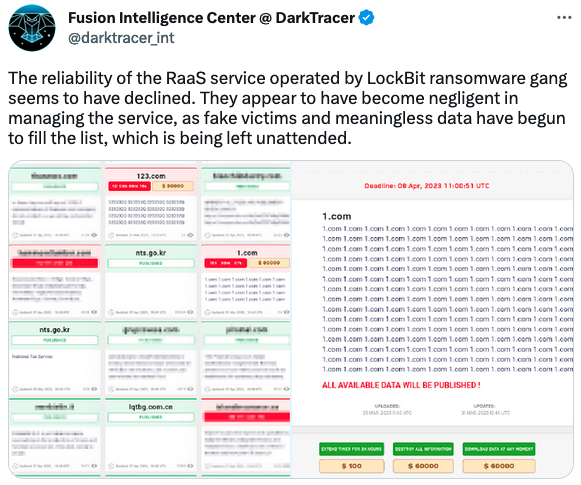
The fake data on the LockBit site was apparently test data posted by the hackers while doing maintenance.
The cybercriminals were not happy with DarkTracer’s allegations, but confused it with UK-based Darktrace and published a post suggesting that they had hacked Darktrace. These types of mistakes are not uncommon for ransomware groups.
It’s worth noting that there is also no evidence that LockBit targeted DarkTracer either.
LockBit last year claimed to have stolen hundreds of gigabytes of data from cybersecurity firm Entrust. The company confirmed that some systems used for internal operations had been breached and that some files had been stolen, but has still not publicly shared additional information on the extent of the breach.
LockBit has also been known to make false claims when it comes to cybersecurity companies. Last year, the group claimed to have stolen hundreds of thousands of files from Mandiant, but it turned out that there was no actual hack and the cybercriminals only made the claims in retribution for a report linking the group to Evil Corp.
Evil Corp is on the US government’s sanctions list and LockBit was concerned that being associated with Evil Corp will prevent ransomware victims from paying up.
Related: Self-Propagating, Fast-Encrypting ‘Rorschach’ Ransomware Emerges
Related: Windows Zero-Day Exploited in Nokoyawa Ransomware Attacks
Related: Yum Brands Discloses Data Breach Following Ransomware Attack

















