805,000 Cybersecurity Professionals Are Currently Estimated to be Working in the U.S., Study Finds
The biggest surprise about the cybersecurity skills gap is that it exists at all. The job description painted by the latest (ISC)2 workforce study, based on responses from 3,237 existing cybersecurity professionals, is attractive.
The pay is good — especially if you have professional certifications (average $90,000 in North America, and $58,000 in Europe). Motivation is also high: “high demand, the ability to work in a continuously evolving field, the ability to constantly solve puzzles and never get bored, and job security. A strong majority — 65% — intend to work in cybersecurity for the rest of their careers,” states (ISC)2 in its new Cybersecurity Workforce Study, 2019 (PDF).
The purpose of this year’s study differs slightly from earlier studies. It doesn’t merely attempt to assess the workforce gap, but also seeks to assess the number of cybersecurity professionals currently in employment. The workforce gap is calculated from the hiring organizations times their expected headcount minus the current supply.
(ISC)2 asserts that these two sets of figures (the current gap and the current number employed) provide a better understanding of what is required to succeed in the cybersecurity age. “We know,” for example, it says, “that the global cybersecurity workforce needs to grow by 145% to meet the demand for skilled cybersecurity talent. In the U.S. specifically, it needs to grow 62%.”
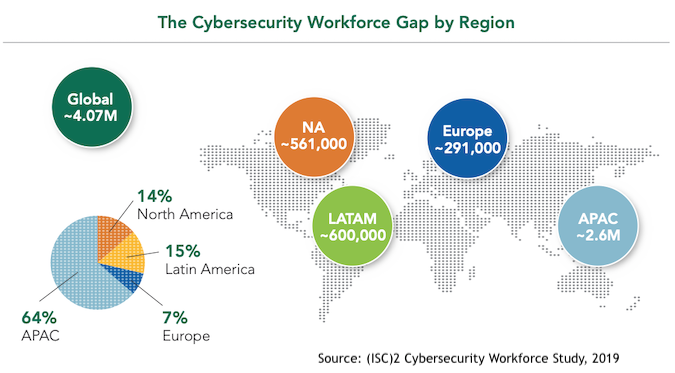
The report then goes on to discuss “insights into immediate and longer-term methods for building qualified and resilient cybersecurity teams now and in the future.” It is, in effect, a report in three sections: the size of the workforce gap, the status of employed professionals, and how to gain and maintain good staffing levels.
“We’ve been evolving our research approach for 15 years to get to this point today, where we can confidently estimate the current workforce and better understand what it will take as an industry to add enough professionals to protect our critical assets,” said Wesley Simpson, chief operating officer, (ISC)2. “Perhaps more importantly, the study provides actionable insights and strategies for building and growing strong cybersecurity teams. Knowing where we stand and the delta that needs to be filled is a powerful step along the pathway to overcoming our industry’s staffing challenges.”
The report starts strongly. The number of participants has doubled from last year’s survey — from 1,452 to 3,237 — giving a claimed margin of error as low as 1.7%. The report also uses a complex method to assess the overall employed workforce based on market inputs.
Available data is greater in the U.S., so this region was used to develop the methodology. It led to the conclusion that “nearly 805,000 cybersecurity professionals are estimated to be working in the U.S.” The methodology was then extrapolated to other regions around the globe; but conservatively, since there is generally less available data outside of the U.S. Nevertheless, this led to estimates that there is an 84,000-strong workforce in Canada, a 133,000-strong workforce in Germany, and a 289,000-strong workforce in the UK.
The (ISC)2 respondents, presumably from the various employed workforces, were questioned over their current views on, and experience in, their employment. There is, frankly, little that is new or surprising in the details (lack of resources, difficult work/life balance etcetera); except, perhaps, the importance placed on academic achievements, industry certifications, and prior experience. Only 12% of professionals do not have a university degree at some level. Once they are in employment, security certifications become more important. “On average,” says (ISC)2, “they hold about four security organization certifications and three security organization memberships.”
Academic qualifications are consequently important to get into cybersecurity, while industry qualifications are important to progress through it. It is not surprising, then, that the primary hurdle to career progression in cybersecurity is the cost of cybersecurity certifications. “The cost of cybersecurity certification is the number one career hurdle, with more than half of respondents having to pay out-of-pocket for at least some of the costs of cybersecurity certifications,” says (ISC)2. The value placed on this certification by employees is amply demonstrated by the higher pay levels for certified staff — certified personnel have an average global salary of $71,000, while those without certifications average $55,000.
Armed with an understanding of the workforce gap, and the nature of the current workforce, the (ISC)2 report moves on to provide advice on ‘building cyber-strong teams’, and ‘developing your cybersecurity dream team’. Building is either from the outside, or from the inside. From the outside, (ISC)2 comments that organizations are “looking for relevant and extensive work experience, advanced knowledge of concepts, and cybersecurity certifications. So, they’re also seeking to hire people who are currently acting as consultants, contractors, and working within security and hardware vendors.” Basically, budding cybersecurity professionals either need academic excellence straight from university, or demonstrable experience from other employment. This is not likely to close the workforce gap.
Building from the inside might help the gap if different disciplines are attracted into cybersecurity. “In building their cybersecurity teams,” says (ISC)2, “70% of organizations give priority to training and promoting from within, according to previous (ISC)2 research. 57% offer training and certification opportunities to employees to strengthen their teams, and 55% offer cross-training on cybersecurity skills and responsibilities.”
Advice on developing a dream team offers three separate strategies. The first is to ensure that the job opportunity is appealing. The first advice given ‘to help mitigate the typical challenge professionals face’ is “Contributing toward the cost of cybersecurity certifications.”
The second strategy “is to level-set on cybersecurity applicant qualifications. Many entry-level and even mid-level positions will be appealing to candidates without the years of experience required to earn many of today’s in-demand cybersecurity certifications,” says the report. “But as our study has revealed, these professionals will be driven to obtain those certifications during their career, which will provide you with even more confidence in your cybersecurity team.”
The third strategy is to recruit from outside — firstly from university graduates with relevant degrees, and secondly by poaching from consultants, contractors, and security and hardware vendors. But the report adds, “Don’t underestimate the power of certifications when it comes to job satisfaction and recruiting… Offer certifications and training in the areas that cybersecurity professionals are most interested in.”
The fourth strategy is to grow the team from within the organization. “Start by identifying talented and motivated non-security-focused IT professionals and paying for cybersecurity trainings and/or certifications.”
The report’s own conclusion states that, “By estimating the global cybersecurity workforce, we know that it needs to grow by 145%. That’s a number organizations can get their arms around. By recruiting talented men and women into the field, attracting experts from outside the organization, and helping to train and develop existing team members, organizations can improve their security stance and help close the gap in their corner of the world.”
But if there is one single theme that pervades this report, it is the value of cybersecurity certifications; and the need for companies to consider subsidizing the cost of those certifications. It should be noted, of course, that (ISC)2 is primarily a vendor of cybersecurity certifications.
Related: Can You Trust Security Vendor Surveys?
Related: CISSP Price Hike Dismays Certified Security Professionals














