Cybercriminals have planted a payment card skimmer on the websites of several organizations using the Playback Now conference platform, Malwarebytes reported on Thursday.
Playback Now enables organizations to record events and deliver the content via live streaming or on demand. It also provides a virtual conference hall and helps companies market their events.
Malwarebytes researchers noticed that a server owned by Playback Now, which hosts conference materials for the company’s customers, was compromised. The customer websites hosted on it — customers receive a dedicated website which they can use to serve their content — had been injected with a payment card skimmer that allowed the attackers to steal the financial information of users purchasing conference materials from those sites.
Tens of these websites appear to be impacted, many of them belonging to educational or medical organizations. It’s worth noting that Playback Now’s official website, playbacknow.com, does not appear to be affected.
Based on Malwarbytes’ analysis, the attackers likely used a previously documented piece of malware designed to provide access to e-commerce websites by brute-forcing credentials. The cybercriminals then inserted one line of code that fetched malicious JavaScript from a domain with a name similar to the official Playback Now website, specifically playbacknows.com, which they registered only a few weeks ago.
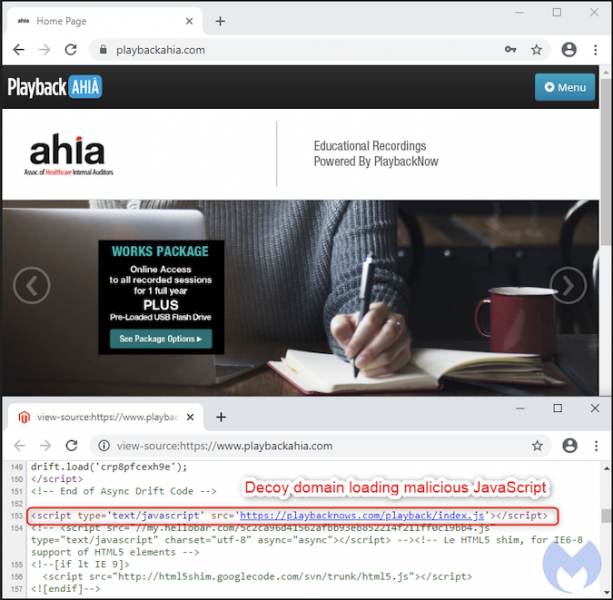
The affected websites were reportedly powered by Magento version 1, which is no longer supported. Tens of thousands of e-commerce websites are still powered by this outdated version of the platform.
Digital skimming protection solutions provider Sansec reported last month that hundreds of Magento stores were hacked daily in what the company described as the largest ever skimming campaign.
The company said at the time that the attackers possibly used a new exploit that had been sold for $5,000. The exploit, which allows users to hack Magento 1 websites, may have been used in this attack as well, possibly by the same group that was monitored by Sansec.
Malwarebytes said it reported its findings to Playback Now, but it’s unclear if any action has been taken. SecurityWeek has reached out to the vendor for comment and will update this article if they respond.
Related: Six Critical Vulnerabilities Patched in Magento
Related: Hackers Accessed Magento Marketplace User Data
Related: Magento 2.3.4 Patches Critical Code Execution Vulnerabilities















