It’s not if, but when and how often you get attacked
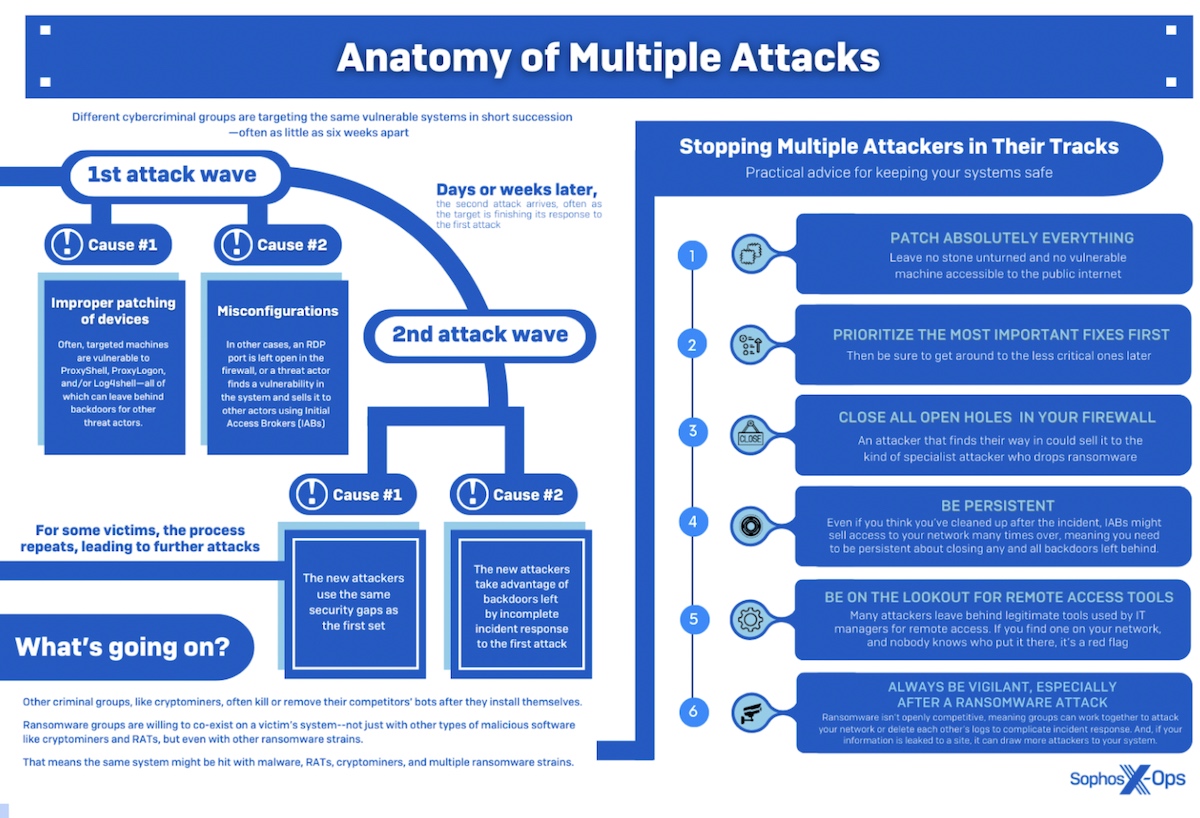
Sophos research for its Active Adversary Playbook 2022 revealed that victims are often attacked by multiple adversaries – usually, in rapid succession but sometimes simultaneously. Further analysis now suggests the aphorism ‘it’s not if, but when you are attacked’ should be expanded with the extension, ‘and how often’.
Multiple attacks are not new, but historically they tend to be separated by months or years. “Now,” John Shier, senior security advisor at Sophos told SecurityWeek, “we’re talking days, weeks or months – in one case just hours.” A new analysis from Sophos looks at the possible reasons for this evolution in attack frequency.
The report, Multiple attackers: A clear and present danger (PDF), provides several specific multiple-attack case studies.
Case #1. A threat actor gained access via an unsecured RDP on April 8, 2022. It dropped malware associated with keylogging and remote command execution on April 19. It was expelled on April 20, but the victim failed to do a domain-wide credential reset.
On May 13, 2022, a second actor authenticated over RDP. On May 29, the attacker pivoted to another host, and DNS requests for anonfiles[.]com and fex[.]net (file-sharing services popular with threat actors) were observed. Some data was uploaded before the attack was stopped on the same day.
Case #2. In March 2022, Sophos responded to a Conti ransomware attack, where the threat actor abused MSBuild.exe to execute Cobalt Strike, beaconing to edgecloud[.]ink. Within a few days, Sophos had to respond to another attack involving Hive ransomware. It also abused MSBuild.exe to execute Cobalt Strike and beaconed to the same domain. Similar instances with overlapping infrastructure suggest that this is a single affiliate of both Conti and Hive.
Case #3. Attackers attempted to exploit ProxyShell on January 6, 2022. On January 19, the attacker established an RDP connection. During January and February, further RDP connections were established, and the attacker downloaded RealVNC. On February 23, two devices communicated with the C&C over DNS, downloading and installing several legitimate tools including AnyDesk.
On March 12, further tools were downloaded. A PowerShell script was used to download and install the legitimate penetration testing tool BloodHound, used to identify potential attack paths in Active Directory. Lockbit was dropped and executed on March 17. On March 25, the victim’s data was posted on the Lockbit leak site.
On April 28, 2022, a second actor entered via a publicly exposed RDWeb portal. This actor attempted to download BloodHound, but the activity was blocked.
On June 2, 2022, a third actor entered via the AnyDesk application installed by the first attacker. Victim data was uploaded to dropmefiles[.]com, a file-sharing service. From entry to exfiltration took less than 15 minutes. On June 8, the Karakurt Team (which has been associated with Conti by some researchers) contacted the victim with a ransom demand. Karakurt typically doesn’t encrypt, but just exfiltrates data and ransoms the data.
Cryptominers
While such growth in repeat attack frequency cannot be denied, it is important to understand the reasons behind it. Sophos notes that the first attack is often from a cryptominer. “What we often see,” said Shier, “is that whenever there’s a new vulnerability that is easy to exploit, perhaps with proof-of-concept code, the cryptominers are rapidly all over it.”
Cryptominers gain access, deliver their code and walk away. This is usually done programmatically and wherever possible; and it may include code to take down competing miners that might also be resident. But because they are often the first in a sequence of attacks, cryptominers shouldn’t be tolerated as an unthreatening annoyance.
“Cryptominers,” suggested Shier, “should be considered as the canary in the coal mine – an initial indicator of almost inevitable further attacks.” The vulnerability that allowed access should immediately be sought and remediated before the same path is abused by more destructive attacks – often the delivery of RATs followed by the installation of ransomware.
Although this is a common progression in multiple attack sequences, Sophos has found no indication of it being a coordinated progression. Cryptominers and ransomware gangs appear to be separate actors, each doing their own thing in isolation from the other. It is quite possible for cryptominers and ransomware to coexist on one victim, but not by design.
Initial Access Brokers
The implication here is that the same vulnerability is found or obtained by multiple actors at the same time. Much of the Sophos analysis seeks to understand this mechanism – and a big part of the conclusion is that it is down to the work of the initial access brokers (IABs).
In a separate report published August 4, 2022, Sophos investigated the Genesis IAB – one of the more advanced marketplaces. “The attacker appeal of Genesis’ collection isn’t the size of its data aggregation; it’s the quality of the stolen information that Genesis offers and the service’s commitment to keeping that stolen information up to date,” reports Sophos. “Genesis customers aren’t making a one-time buy of stolen information of unknown vintage; they’re paying for a de facto subscription to the victim’s information.”
Some IABs go to great lengths to maintain the access they sell. “There are some that will install Cobalt Strike or Brute Ratel to maintain the access for sale,” said Shier.
But there are many other IABs, offering both bulk credentials and individual accesses to major organizations. The bulk credentials appeal to the less sophisticated attackers who carry out rapid fire cryptominer attacks. The individual accesses might be bought by more sophisticated ransomware actors. Some IABs provide a single customer service, but many do not. Access to a single victim might be purchased by multiple different actors for different purposes in a short period of time.
This explains the usual sequence of attacks, starting from those that require relatively little expertise (cryptomining) and expanding over a short period to those attackers that surveil, move laterally and finally detonate malware (ransomware).
It’s important to note, however, that some ransomware actors do not rely on IABs. While the presence of a cryptominer might indicate the likelihood of further sophisticated attacks, the absence of a miner does not indicate the reverse.
Conti is a case in point. “It seems like they pivoted,” explained Shier. “In the beginning, it looks like they were using IAB services, but as they went forward, it seems they decided to take on that that work for themselves. So, it was a bit of a bootstrapping, like a startup. They bootstrapped their organization by leveraging the services of another group for initial access; but then as they became more competent and grew their organization, they were able to bring that stuff in house.”
Multiple ransomware attackers
One surprising element of the current increase in both frequency and speed of attacks is that different ransomware attackers may be found in the same victim at the same time. These attackers are likely to be aware of other’s presence, but it does not prevent either from continuing. It is the most recent encryptor that will stand the greater chance of receiving a payout. Sophos has found no evidence of collusion between different gangs.
The conclusions from the Sophos study are complicated and disturbing. Threat actors discover the presence of new vulnerabilities by rapidly scanning the internet. Vulnerabilities become public knowledge – even with proof-of-concept code – faster than many companies can patch them. These are rapidly exploited by simpler types of malware, such as cryptominers, using programmatic methods. Such exploitation is exacerbated by the purchase of readymade access bought in bulk from the IABs.
Following the same process, more complex malware such as ransomware may follow. This is not the result of some master coordinating criminal plan, but the confluence of several factors: organizations’ inability to patch new vulnerabilities fast enough and protect credentials; increasing sophistication and automation by the criminal element; and the sheer and growing number of attackers. As such, the current increase in the number of attacks is likely to continue.
Related: It Doesn’t Pay to Pay: Study Finds Eighty Percent of Ransomware Victims Attacked Again
Related: Ransomware, Malware-as-a-Service Dominate Threat Landscape
Related: Cyber Insights 2022: Improving Criminal Sophistication














