
Colonial Pipeline halts all fuel pipeline operations in response to ransomware attack
A cyberattack has forced an operational shutdown of the Colonial Pipeline, the largest refined products pipeline in the United States.
The Colonial Pipeline Company said late Friday that it was the victim of a cyberattack, sparking the company to proactively take certain systems offline and temporarily halt all pipeline operations. The company said the attack had impacted some of its IT systems, but did not say if any of its operational technology (OT) systems were directly impacted.
Colonial said in an update Saturday that the incident does involve ransomware.
[Update: Colonial Pipeline Aims Recovery From Ransomware Attack by End of Week
[Update: Colonial Pipeline Struggles to Restart After Ransomware Attack]
[Update: Cyberattack on US Pipeline is Linked to Criminal Gang]
The company has hired a third-party cybersecurity firm (reportedly FireEye) which has already launched an investigation into the nature and scope of this incident.
“Colonial Pipeline is taking steps to understand and resolve this issue,” the pipeline operator said in a statement. “At this time, our primary focus is the safe and efficient restoration of our service and our efforts to return to normal operation. This process is already underway, and we are working diligently to address this matter and to minimize disruption to our customers and those who rely on Colonial Pipeline.”
The Colonial Pipeline is the largest refined products pipeline in the United States, transporting more than 100 million gallons of fuel daily through a pipeline system that spans more than 5,500 miles between Houston, Texas and Linden, New Jersey.
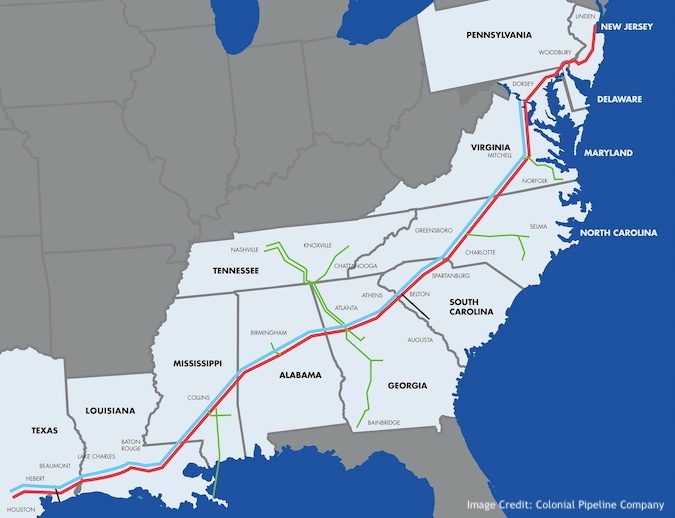
The incident comes just days after the U.S. National Security Agency (NSA) released a cybersecurity advisory focusing on the security of OT systems, particularly in terms of connectivity to IT systems.
Last year, the NSA and the Cybersecurity and Infrastructure Security Agency (CISA) issued a joint alert urging critical infrastructure operators to take immediate measures to reduce the exposure of OT systems to cyberattacks.
In 2019, an audit from the Government Accountability Office (GAO) showed that the U.S. Department of Homeland Security’s (DHS) Transportation Security Administration (TSA) needed to address weaknesses in the management of key aspects of its pipeline security program.
Learn More About ICS Security at SecurityWeek’s ICS Cyber Security Conference
Following a review in how the TSA manages its pipeline security program, the GAO made a series of recommendations in December 2018 to address discovered weaknesses, which include updating pipeline security guidelines, planning for workforce needs, assessing pipeline risks, and monitoring program performance.
Back in 2012, the Department of Homeland Security (DHS) warned that malicious actors had been targeting the natural gas industry.
*Updated with commentary
Related: Cyber Attacks Targeted Key Components of Natural Gas Pipeline Systems
Related: Several U.S. Gas Pipeline Firms Affected by Cyberattack
















