Programmable logic controllers (PLCs) from Germany-based industrial automation company WAGO are affected by a potentially serious vulnerability that could give a remote attacker access to an organization’s entire network.
The flaw, discovered by a researcher at security services and consulting company SEC Consult, impacts Linux-based WAGO PFC200 series PLCs, specifically a total of 17 750-820X models running firmware version 02.07.07 (10). The affected devices are advertised by the vendor as ultra-compact and secure automation systems that can be used for traditional machine control, process technology, and in the offshore sector.
The security hole exists due to the use of version 2.4.7.0 of the CODESYS Runtime Toolkit. This embedded software is developed by 3S-Smart Software Solutions and it’s used by several vendors in hundreds of PLCs and other industrial controllers.
A few years ago, researcher Reid Wightman discovered that versions 2.3.x and 2.4.x of CODESYS Runtime were affected by critical access control and directory traversal vulnerabilities that could have been exploited to hack devices.
Building on Wightman’s research, SEC Consult discovered that various functions of a service named “plclinux_rt” can be accessed without authentication by sending specially crafted TCP packets on port 2455, which is the programming port.
An attacker can use this method to write, read or delete arbitrary files, which can be done with a tool created by Digital Bonds several years ago for interacting with PLCs that use CODESYS. Since SSH is enabled by default on PFC200 PLCs, an unauthenticated hacker can exploit this to rewrite the etc/shadow file, which stores password hashes, and gain root privileges to the device.
SEC Consult said the vulnerability can also be exploited to modify the PLC program during runtime and cause the device to step over a function, restart or crash.
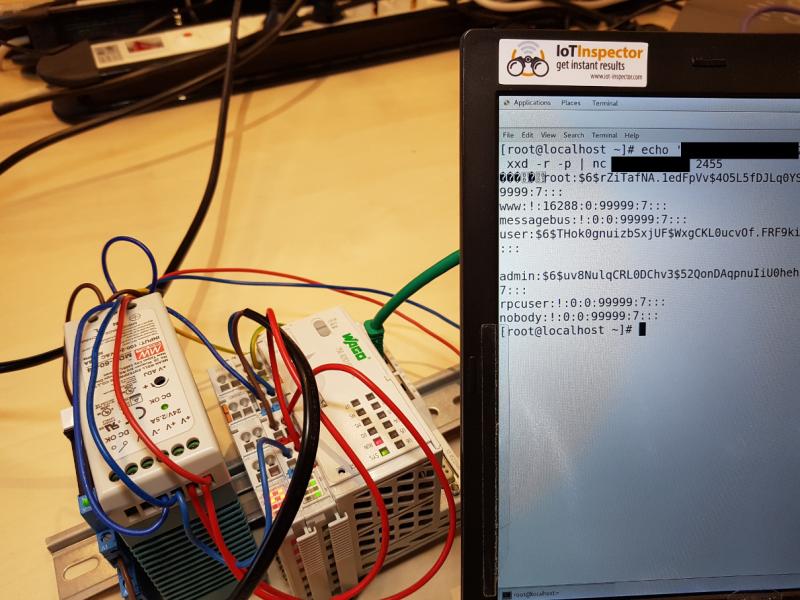
The security firm told SecurityWeek that while it hasn’t scanned the Internet for devices that can be exploited on port 2455, it has found nearly 2,500 WAGO PFC200 devices on the Web via the Censys search engine. These devices are often found in critical infrastructure organizations, including power plants, the company said.
Shodan has been crawling port 2455 since 2014 to check for CODESYS protocol (login required to view results). The search engine has identified nearly 4,000 systems reachable via this port, with a majority in the United States (911), Germany (329), China (255), France (200) and Japan (162).
These PLCs were also included in a heatmap of industrial control systems located in the APAC region, which Shodan CEO John Matherly presented earlier this year at SecurityWeek’s ICS Cyber Security Conference in Singapore.
“Because of the use in industrial and safety-critical environments the patch has to be applied as soon as it is available,” SEC Consult warned in a blog post. “We explicitly point out to all users in this sector that this device series in the mentioned device series with firmware 02.07.07(10) should not be connected directly to the internet (or even act as gateway) since it is very likely that an attacker can compromise the whole network via such an device.”
WAGO was informed about the vulnerability in August, but it has yet to release a patch. The vendor estimates that a fix will be made available in January 2018.
SEC Consult has published an advisory describing the flaw, but it will not release a proof-of-concept (PoC) exploit until a patch is available. In the meantime, the security firm has advised users to either delete the “plclinux_rt” service or close the 2455 port in order to prevent potential attacks.
The company believes the vulnerability could affect devices from other vendors that use CODESYS Runtime 2.3.x or 2.4.x. These are older versions of the tool – versions 3.x are not impacted.
This is not the first time a significant number of ICS devices have been exposed to attacks due to the use of a CODESYS component. Earlier this year, CyberX warned that hundreds of thousands of Industrial Internet of Things (IIoT) and ICS devices had been vulnerable due to a critical flaw in the web server component of the CODESYS WebVisu visualization software.
*Updated with information from Shodan
Related: Researchers Disclose Unpatched Flaws in Schneider Electric PLCs
Related: PLCs From Several Vendors Vulnerable to Replay Attacks













