One of the vulnerabilities Microsoft addressed with the June 2018 security patches was a flaw in Cortana that could allow an attacker to elevate privileges and execute code from the lock screen.
The issue, discovered by Cedric Cochin, Cyber Security Architect and Senior Principle Engineer at McAfee, is tracked as CVE-2018-8140. The bug can be abused to execute code on the impacted machine, directly from the lock screen.
In an advisory, Microsoft explains that the vulnerability “exists when Cortana retrieves data from user input services without consideration for status.” The company confirms the possible exploitation to execute commands with elevated permissions.
The vulnerability requires physical access to the impacted device and appears connected to a flaw independent researchers Amichai Shulman and Tal Be’ery detailed in March, and which could be abused to install malware on the affected computers.
In order to exploit the issue, an attacker with access to the impacted computer needs to have Cortana assistance enabled. A user can interact with the voice-based assistant even from the lock screen, by saying “Hey Cortana.”
Cortana can also be tricked to display search results with the contextual search menu, from the lock screen. This, however, requires the use of a keyboard-timing sequence: “any keystroke can trigger the menu from the time when Cortana begins to listen to when the answer is displayed.”
According to Cochin, because Windows indexes file content, including strings in documents, Cortana can be abused to leak sensitive information. Specifically, if the right search phrase is used when clicking on the “tap and say” button, Cortana could show the content of confidential files, such as those storing passwords.
“Armed with this knowledge, you can use your imagination to come up with specific keywords that could be used to start harvesting confidential information from the locked device,” the researcher notes.
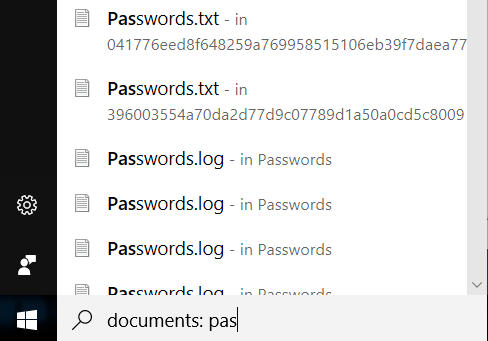
When hovering over a file in the search results provided by Cortana, the full path or content of the file would be displayed. When clicking on the file, it is launched using the appropriate program, but would only be accessible after the user logs in.
“At this point we can execute various preloaded Windows utilities such as calculator, but we cannot pass any parameters to the command line. We can open scripts including PowerShell, but instead of being executed, they will be opened in a text editor (notepad),” Cochin says.
Basically, “live off the land” attacks that abuse existing tools for malicious purposes cannot be performed because of a lack of parameters. Other nefarious operations, however, such as uninstalling applications, are possible even with these restrictions in place.
To execute code from the lock screen using Cortana, one would need to make sure the code is indexed (appears in the contextual menu). To get results to show up in the index of an authenticated user, an attacker can abuse OneDrive, where the contents of all shared folders with “edit” rights are indexed.
Thus, an attacker can drop an executable in the OneDrive folder, which can then even be executed as an administrator by simply right-clicking on it and selecting the “Run as administrator” option. Although a user account control (UAC) prompt could be triggered, the attack might still work, as users rarely check the content of the prompt before clicking through it.
Another option the attacker has is to use a non-portable executable (PE) malicious program, such as a PowerShell script. However, Cortana would only allow for the editing of such files, and would open them in Notepad instead of the default editor (PowerShell ISE).
When searching for txt, however, Cortana would display not only the text files, but also recently opened ones, such as the PowerShell script, and would provide a different contextual menu for them. Thus, an attacker could first edit the script, then search for txt, and simply select “Run with PowerShell” from the right-click menu.
“We now have local code execution with the payload of our choosing, without any exploit, even if the device is encrypted, on an up-to-date locked Windows 10 device. This technique helps us understand some of the differences between apps, documents, extensions, and the way Windows handles them from a locked or unlocked screen,” the security researcher explains.
Although code execution is now possible, there are limitations, as no command-line parameters can be passed. However, because it is possible to use the keyboard in addition to voice commands when interacting with Cortana from the lock screen, an attacker could use this to run the PowerShell code as an administrator.
“What can we do at this point? You name it. Our demo shows a password reset and login on a Windows 10 build, using only this simple technique,” the researcher notes.
To prevent exploitation of the vulnerability, even if it can only be abused with physical access to the vulnerable machine, one could turn off Cortana on the lock screen. Installing the recently released fixes for CVE-2018-8140 also mitigates the attack.
Related: Microsoft Patches 11 Critical RCE Flaws in Windows, Browsers
Related: Cortana Can Expose Enterprises to Attacks, Researchers Warn














