Data breaches affecting corporate and internal networks increased considerably in 2015 compared to the previous year, according to the 2016 Global Security Report published by Trustwave on Tuesday.
Corporate and internal network breaches accounted for 40 percent of the incidents investigated last year by the security firm, compared to 2014 when only 18 percent of compromises affected these types of environments.
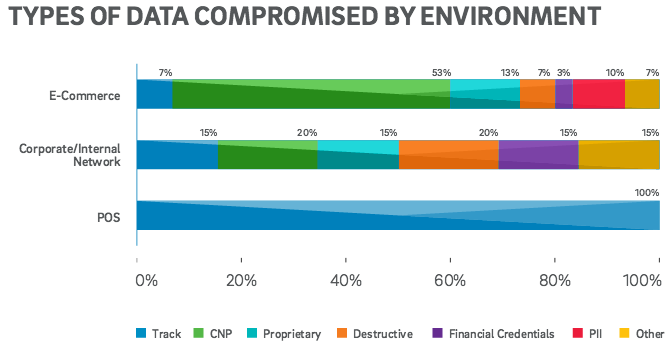
Since corporate and internal environments comprise the enterprise network in general, attackers managed to gain access to various types of data, including payment card data, proprietary information, financial credentials, and personally identifiable information. In 20 percent of malicious operations targeting corporate environments, the attackers sought to damage information, not steal it.
The number of attacks aimed at e-commerce environments accounted for 38 percent of the attacks analyzed in 2015 by Trustwave, roughly the same as in the previous year. Magento had been running on 85 percent of the compromised systems, which is not surprising considering the platform’s popularity.
As for incidents involving point-of-sale (PoS) systems, the share of attacks investigated by the security firm dropped to almost half compared to the previous year.
Similar to 2014, most of the incidents analyzed by the security firm occurred in North America (45%), followed by the Asia-Pacific region (27%), the EMEA region (15%) and Latin America (13%).
While the retail industry remained the most targeted sector, the share of attacks aimed at retail organizations dropped to 23 percent, compared to 43 percent in 2014. The second most targeted sector was hospitality, followed by food and beverage, entertainment, finance and insurance, travel, professional services and transport.
Of the attacks targeting retail organizations, 17 percent were aimed at the corporate network and, according to Trustwave, more than 80 percent of the data stolen from the retail sector was from card-not-present (CNP) transactions.
Trustwave determined that the median number of days it took companies to detect an intrusion was 80.5 in 2015, a slight improvement from 86 days in 2014. A more significant improvement is seen in the time needed to contain an intrusion after detection — experts report a drop from 7 days in 2014 to 2 days in 2015.
Organizations seem to be getting better at detecting malicious activity within their networks. Last year, 40 percent of attacks analyzed by Trustwave were first detected by the victims themselves — up from 19 percent in 2014.
The factors that allowed malicious actors to access targeted systems were insecure remote access software and policies (13%), SQL injection flaws (12%), misconfiguration issues (12%) and file upload vulnerabilities (10%). Social engineering, malicious insiders, code injection flaws, weak passwords, and authentication bypasses each accounted for 7-8 percent of breaches.
The complete 2016 Trustwave Global Security Report is available for download in PDF format. In addition to data compromise trends, the 90-page report details a wide range of topics classified as “threat intelligence” and “state of security.”













