Over the last several days, weeks really for some, people have noticed an uptick in the amount of spam coming from compromised Yahoo accounts. SecurityWeek staff has witnessed this uptick in spam as well. But this spam run is designed to spread malware to Android devices, so it’s likely not as simple as a weak password issue.
Compromised email accounts, on services such as AOL, Yahoo, Hotmail (before it was Outlook), and Gmail have been used to spread spam for years. Often, someone has their account hijacked and an email is delivered to their entire address book requesting that the recipients follow a link somewhere. Mostly, those types of messages are pharmaceutical-based (‘Buy these pills now with no RX needed’), but some have been known to push malware that helps compromise additional email accounts.
This latest Yahoo-based spam campaign is similar. Visit the spammed link via a PC and you’ll see health-product related spam. However, access the link on an Android device, and you’re getting hit with the “NotCompatible Trojan”.
According to Android-based security vendor Lookout:
“NotCompatible is a new Android Trojan that appears to serve as a simple TCP relay / proxy while posing as a system update. This threat does not currently appear to cause any direct harm to a target device, but could potentially be used to gain illicit access to private networks by turning an infected Android device into a proxy.”
This malware has been used before. Similar to this most recent example, those attacks also originated from spammed links via compromised email accounts that only served malware to mobile devices.
In a report from Virus Bulletin, the links used in this most recent attack are still active. The registrar responsible for maintaining them has been unresponsive to requests for help and security alerts. However, the root problem may be Yahoo’s and not the account owners – who often take the blame for these types of attacks due to weak password usage.
“We have reasons to believe that, in this case, the problem lies on Yahoo!’s side,” wrote Martijn Grooten, on the Virus Bulletin blog.
“Firstly, the volume of spam from compromised Yahoo! accounts is significantly larger than that sent from other webmail providers. We have noticed this before – and, if anything, the problem has since become worse. More importantly, from various reliable sources, we know that accounts that had not been used for a very long time have been compromised as part of this campaign.”
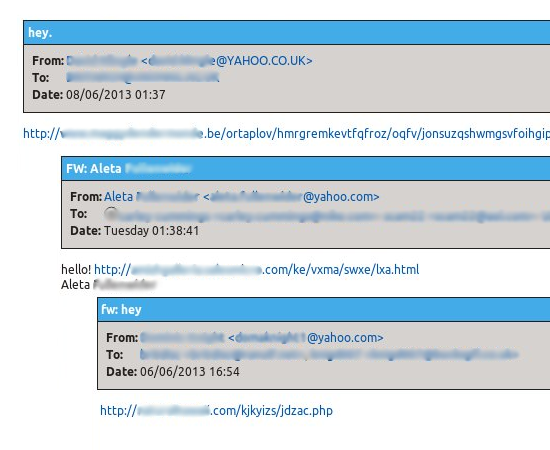
As mentioned, the links used in the campaign are all active, and the best advice is simply to avoid random links – even if they come from a legit Yahoo account. In this campaign, the emails often have a random subject such as “Hey” or “Christen G” and a single link. They stand out as suspicious, especially of you know the account they come from and the message is outside of the norm.
There is no word as of yet if Yahoo! has responded to Virus Bulletin.













