
Cybersecurity is only as strong as the layer beneath it. The bottom layer is not the operating system, but the hardware and firmware on which the OS operates.
The usual view of security is that it’s provided by security application software. But security is only as strong as the layer beneath ‒ so attackers can subvert security software by compromising the operating system beneath the security application. Microsoft has done much to secure its Windows OS in recent years ‒ but beneath the OS is the hardware and the firmware that drives it.
If the attacker gets beneath the OS and into the firmware, security running on top of the OS has little if any visibility into the attack ‒ and little if any ability to mitigate the attack. A successful firmware attack ‒ such as that used by the Russian Fancy Bear group (aka APT28 or Strontium) will survive an OS reinstall and even a hard disk replacement. For this reason, advanced attacks against firmware have increased dramatically in recent years.
In March 2021, Microsoft research reported that more than 80 percent of enterprises had experienced at least one firmware attack in the past two years, but only 29 percent of security budgets are allocated to protect firmware.
There is no simple solution to the firmware and other hardware-level problems ‒ it basically requires a rethink of silicon capabilities, hardware practices, and the relationship between these and the operating system. Such a partnership program has been in operation for several years, resulting in the new category of PCs described by Microsoft as ‘Secured-Core‘.
The basis of this new breed of secure PC is the underlying silicon security. Secured-Core PCs combine a hardware root of trust, firmware protection, Hypervisor-enforced code integrity, and isolated and secured identity and domain credentials.
SecurityWeek talked to Michael Nordquist (Intel’s business client planning director) to discover the chip giant’s role in securing the latest and future computers from the silicon level up.
Intel Hardware Shield
The silicon security parts of Secured-Core PCs are only part of Intel’s ongoing hardware security program.
As hackers continue to evolve their techniques, moving increasingly towards the hardware infrastructure, Intel argues that organizations of all sizes must invest in better technology — from endpoint to network edge to cloud.
Intel describes its security technology program as covering three primary areas: foundational security, workload and data protection, and software reliability.
At the core of its security offerings is the Intel Hardware Shield, a set of security technologies capable of monitoring CPU behavior for signs of malicious activity and using GPUs to help with accelerated memory scanning.
At the heart of Intel Hardware Shield is TDT (Threat Detection Technology), a set of tools that harness silicon-level telemetry and acceleration capabilities to help pinpoint early signs of ransomware, crypto-mining, fileless scripts and other targeted attacks.
According to Intel, TDT has been updated with a feature called “targeted detection” that combines machine learning with hardware telemetry to profile, exploit and detect their behavior.
The company describes TDT’s advanced platform telemetry as a “low overhead tool” that does not require intrusive scanning techniques or signature databases.
“Using the telemetry we have at the chip level,” said Nordquist, “we can see things that the OS cannot. If we see some form of weird encryption going on to the hard drive, we can throw a flag at it. That’s abnormal behavior, possibly indicative of a ransomware infection. Those are the things that we’re able to do at the device level.”
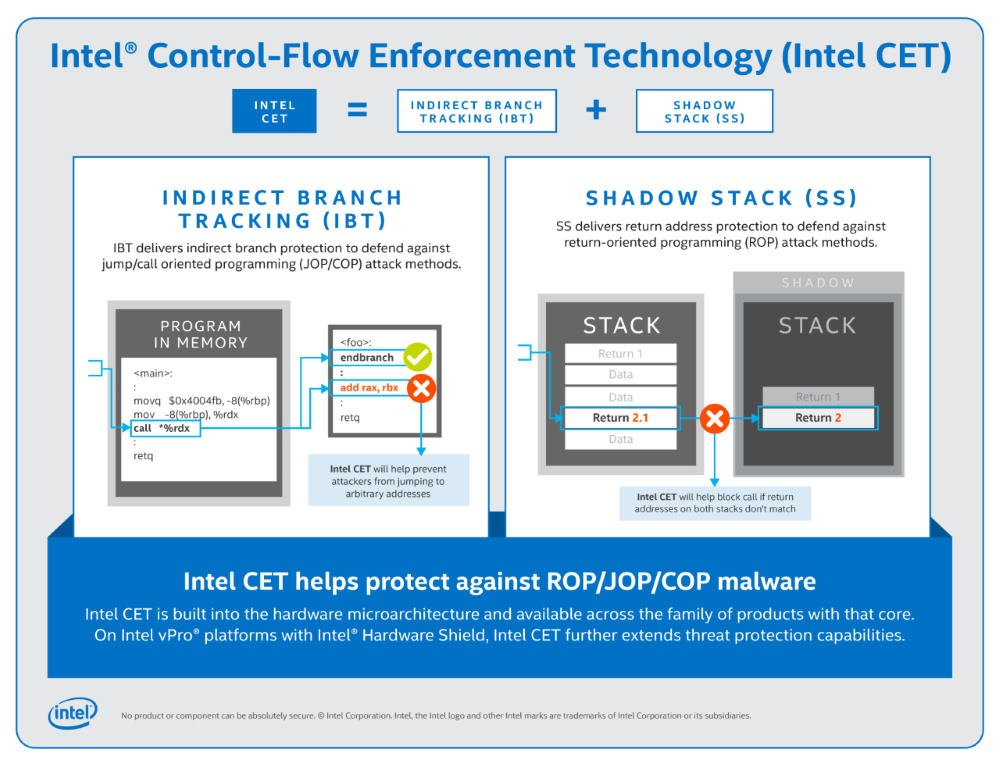
Intel Control-Flow Enforcement Technology (Intel CET)
Intel’s Control-Flow Enforcement Technology, announced in June 2020 falls under the software reliability category and provides further protection against JOP/COP and ROP memory-based attacks.
According to Nordquist, CET offers software developers two key capabilities to help against control-flow hijacking malware: shadow stack and indirect branch tracking. The first provides an indirect branch protection against jump/call-oriented programming (JOP/COP) attack methods, while the second delivers return address protection to help defend against return-oriented programming (ROP) attack methods.
JOP or ROP attacks are difficult to detect or prevent because exploit writers use existing code running from executable memory in a creative way to change program behavior. At its core, Intel CET is a hardware-based solution that triggers exceptions when hackers try to modify the natural flow of the program.
“We launched that product last year,” continued Nordquist. “Within a couple of months of launching it, we had OS support to help prevent the attacks. All you need to do is just click to upgrade to the latest version of the OS. So, we find a problem, we see where we can add value, we figure out if there is a partner we need to work with to solve the full end-to-end problem, and then we make it easy for our end customers or IT shops to just absorb it.”
Intel CET has already been turned on in Google Chrome for Windows and Microsoft is featuring the technology in its new “super duper secure mode” Edge browser security experiment.
‘Trust No One’
Zero-trust, which Intel calls ‘trust no-one’, is a security vision that the company has accepted. Intel describes its silicon as ‘a network on a chip’ and is implementing zero-trust within this network. This includes concepts such as ‘fail safe and securely’ to ensure that no secrets are lying around after, for example, a cold boot attack; ‘complete mediation’ to check the legitimacy of every single access; ‘least privilege’ to minimize the privileges of each hardware agent while also minimizing privilege ‘creep’; and more.
Having ensured the integrity of the chip with these and other silicon level developments, zero-trust can be layered on top and into the wider commercial networks. Each PC can be uniquely identified, and the silicon it contains can be trusted. The next step is to ensure the integrity of the device itself, and the user or owner of the device.
Add this to other new hardware security features – such as firmware protection – and you can have a strong foundation for saying, ‘I know this device and I know I can trust it’. All that remains is confirming the identity of the user. This is even more important for the evolving hybrid home/office work environment because the PC at home is far less protected.
[ Related: Microsoft: Firmware Attacks Outpacing Security Investments ]
Intel’s support for the zero-trust vision from the hardware level up is a work in progress, but the intention is nothing less than the elimination of required VPNs in communications across the internet ‒ because the device and its user can be trusted, and the communication can be encrypted.
Hardware upgrade cycles
Ten years ago, companies would be on a five- or six-year OS replacement cycle, and a three- or four-year PC replacement cycle. This meant, for the most part, new hardware capabilities could be in place ready for the next OS version to take advantage of them. This has changed.
“The beauty of Win10 and now Win11,” said Nordquist, “is that most enterprises are on a 6-, 9- or 12-month cycle, which means that every 6, 9 or 12 months we [Intel] are able to offer new hardware capabilities that can rapidly be supported by the OS. People can upgrade from one version of the OS to the next version way easier than when they were going from XP to Win7. It’s just about an hour’s download and reboot.”
But this just reverses the primary problem. “Sometimes, problems can be solved with downloadable firmware updates,” said Nordquist. Nowadays, the installed OS is ready to take advantage of such hardware security improvements, but must wait for the company to replace aging computers with the latest models that incorporate the hardware improvements.
Nordquist believes the hardware replacement cycle is shortening. His argument is that the board and the modern CISO now take an holistic view of cybersecurity – partly because of the potentially catastrophic effect of attacks like ransomware, and the new problem of poorly protected remote computers. “So,” he says, “companies are holistically looking at, how can I actually fix that? What can I do? How do I get the best protection against some of these things? And they’re realizing it needs to be a combination of hardware and software.” An holistic view of cybersecurity requires a closer alignment of OS and hardware replacement cycles.
This just places an additional budgetary strain on business, and only the wealthiest companies will be able to do this. We know from the length of time it has taken some organizations to replace Windows XP systems that many companies can either not afford to more regularly replace their hardware, or have additional restraints (such as a possible operational reliance on aging proprietary software) to prevent them.
The best solution would be to find some way to upgrade hardware as rapidly and easily as we now upgrade operating systems. Could silicon, motherboards and PCs be re-architected so that hardware upgrades could be a user-performed chip replacement (or additional chip plug-ins) without having to replace the entire box? This may or may not be technologically possible in the future.
Related: New Side-Channel Attack Targets Intel CPU Ring Interconnect
Related: Intel Improves Hardware Shield in New 10th Gen Core vPro Processors
Related: Microsoft, Intel Introduce ‘STAMINA’ Approach to Malware Detection











