The French National Agency for the Security of Information Systems (ANSSI) on Wednesday issued an alert to warn organizations that a threat group tracked as APT31 has been abusing compromised routers in its recent attacks.
According to ANSSI, this “large intrusion campaign” is ongoing and it has impacted many organizations in France. The agency has shared indicators of compromise (IOCs) to help organizations detect potential attacks.
“It appears from our investigations that the threat actor uses a network of compromised home routers as operational relay boxes in order to perform stealth reconnaissance as well as attacks,” ANSSI said.
APT31 is also known as Zirconium, Judgment Panda and Red Keres, and its activities were previously linked to the Chinese government.
APT31 is one of the three threat groups that the UK government officially attributed to China this week when Five Eyes countries, the European Union, NATO, and Japan officially attributed Microsoft Exchange server attacks to hackers affiliated with the Chinese government.
The UK said APT31 had targeted government entities, political figures, contractors and service providers in European countries, including Finland’s parliament last year.
A security researcher has highlighted that the roughly 160 IP addresses shared by ANSSI are associated with devices mostly located in Asia, Latin America, and Africa. Approximately one-third of the devices appear to be located in Russia.
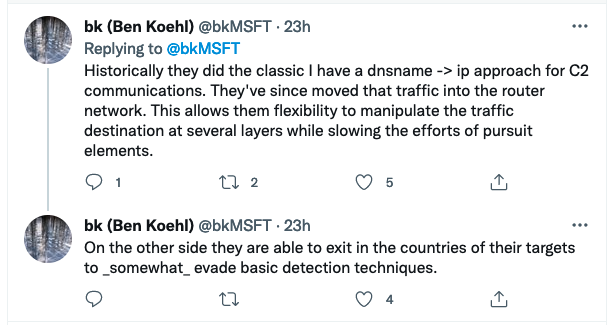
Ben Koehl, principal threat analyst at Microsoft’s Threat Intelligence Center, noted, “ZIRCONIUM appears to operate numerous router networks to facilitate these actions. They are layered together and strategically used. If investigating these IP addresses they should be used mostly as source ip’s but on occasion they are pointing implant traffic into the network.”
Related: Chinese Hackers Cloned Equation Group Exploit Years Before Shadow Brokers Leak
Related: Sophisticated Cyberspies Target Middle East, Africa via Routers
Related: Chinese Hackers Target Cisco Discovery Protocol Vulnerability













