A cyber-espionage group believed to be operating out of China has developed a new piece of malware that appears to be based on one of the first tools used by the threat actor.
The actor is known as APT15, Ke3chang, Mirage, Vixen Panda, Royal APT and Playful Dragon, and its tools are tracked by various cybersecurity companies as Mirage, BS2005, RoyalCLI, RoyalDNS, TidePool, BMW and MyWeb. The group has been known to target organizations in the defense, high tech, energy, government, aerospace, manufacturing and other sectors.
One of APT15’s more recent attacks was uncovered last year when the hackers targeted a UK-based customer of NCC Group. The organization provides a wide range of services to the United Kingdom government and NCC believes the attackers may have targeted government departments and military technology through its customer.
NCC noted at the time that the group had improved its tools and techniques. The company had uncovered two new backdoors used by APT15, including RoyalCLI, a successor of BS2005, and RoyalDNS.
Intezer, a cybersecurity firm that specializes in recognizing code reuse, reported last week that it had identified a new piece of malware linked to APT15 based on YARA rules created for Mirage, the oldest tool used by the threat actor, and Reaver, another piece of malware previously linked by researchers to China.
The new malware, dubbed by Intezer MirageFox based on a string found in one of the components, shares code with both Mirage and Reaver. Experts have found significant similarities to the original Mirage malware, including in the code used for a remote shell and the function for decrypting command and control (C&C) configuration data.
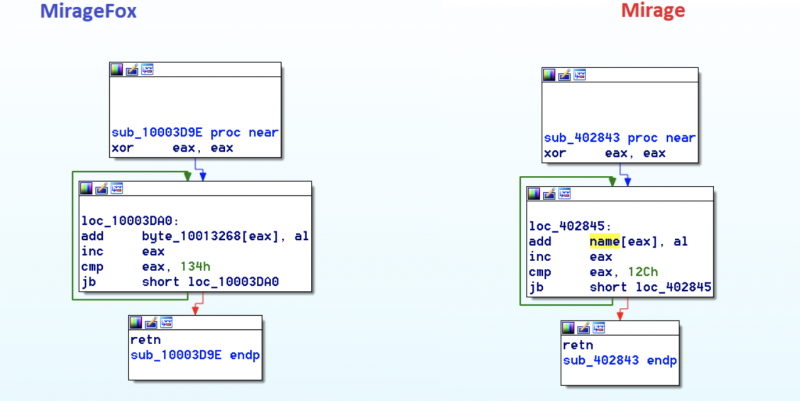
“MirageFox functions similarly to previous malware created by APT15, first collecting information about the computer like the username, CPU information, architecture, and so forth. Then it sends this information to the C&C, opens a backdoor, and sits waiting for commands from the C&C with functionality such as modifying files, launching processes, terminating itself, and more functionality typically seen in APT15’s RATs,” Jay Rosenberg, senior security researcher at Intezer, explained in a blog post.
The sample analyzed by the security firm was compiled on June 8 and uploaded to VirusTotal one day later. While it’s unclear how the malware has been distributed to victims, Intezer has made some interesting observations about MirageFox.
The malware appears to abuse a legitimate McAfee binary to load malicious processes through DLL hijacking. APT15 has been known to use DLL hijacking in its campaigns.
Intezer also noticed that a C&C server has an internal IP address, which suggests that the sample was specifically configured for the targeted organization and that, similar to the attack described earlier this year by NCC Group, the attackers gained access to the victim’s internal network using a VPN.
It’s unclear if they are connected, but Intezer pointed out that the discovery of MirageFox coincides with reports of an attack in which hackers believed to be sponsored by China stole sensitive information from a US Navy contractor.
While previous public reports on APT15 claim the group has been around since at least 2010, Rosenberg told SecurityWeek over the weekend that he has identified a Mirage sample uploaded to VirusTotal in 2009.
Rosenberg also noted that Mirage shares code with other pieces of malware attributed to APT15, including BMW, BS2005, and particularly MyWeb. The expert also believes, based on the code they share, that the developers of APT15 malware may have also created Reaver.
Related: China-linked Hackers Target Engineering and Maritime Industries
Related: Researchers Link Several State-Sponsored Chinese Spy Groups















