A recent report from Blue Coat Systems, has revealed that the number of malicious networks – or “Malnets” – has tripled in the last six months. Collectively, the Malnets themselves are responsible for millions of attacks each month on systems used at home and the office.
Malnets are infrastructures that exist online for one reason; to deliver mass market attacks to the largest number of systems and people as possible. That’s it. There is nothing else for them to do, but those who control them are able to make massive amounts of money by renting them out, or launching their own attacks and keeping all the profits. In 2012, Blue Coat says that these infrastructures are responsible for more than two-thirds of the attacks seen online.
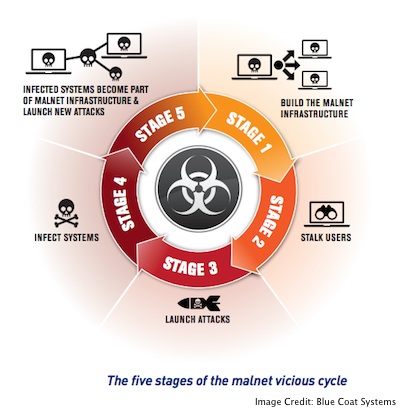 The fact that such networks exist isn’t new, or unsurprising to security administrators. What is new, is the role that automation plays in their development and usage, and the fact that the controllers can launch new attacks with ease. The fact that Malnets themselves can be interconnected also plays a part in their dark existence.
The fact that such networks exist isn’t new, or unsurprising to security administrators. What is new, is the role that automation plays in their development and usage, and the fact that the controllers can launch new attacks with ease. The fact that Malnets themselves can be interconnected also plays a part in their dark existence.
“First the Malnet drives a user to the malware. Then the user’s computer is infected with a Trojan. Once the computer is compromised it can be used by the botnet to lure new users into the Malnet by using the infected machine to send spam to email contact lists, for example. A compromised system can also be used to steal the victim’s personal information or money, and, in some cases, can also function as a jumping-off point for attacks on neighboring machines,” Blue Coat explains in their report.
As mentioned, the number of Malnets has tripled over the last six months, from 500 to 1,500. This represents 3.4 million attacks a day. Email remained the second most popular entry point into Malnets, confirming that the ease with which it can be exploited makes it useful for driving users to malware. Email, via spam attacks, is also one of the leading ways in which botnet-infected computers are used, the report noted.
They are nearly impossible to shutdown completely as well, the design of the Malnets means that their controllers can alter C&Cs at will. For example, the largest Malnet, Shnakule, issued changes to its host C&C 56,000 times so far.
“Malnets will continue to dominate the threat landscape in the future since it is virtually impossible to shut them down. Yet traditional security solutions are focused on identifying and blocking malware payloads, not the infrastructures that deliver them,” the company said.
The full report is available here.















