Kaspersky Lab said that it has discovered how victims of an ongoing massive cyber espionage campaign were infected, shedding light on questions previously left unanswered in earlier research.
The campaign, called Epic Turla, targeted intelligence agencies, government institutions, embassies, military groups, education institutions, and research and pharmaceutical companies in more than 45 countries, the security firm said on Thursday.
Turla, also known as Snake or Uroburos, is considered by researchers to be one of the most sophisticated ongoing cyber-espionage campaigns. Earlier research by G-Data published in February of this year on Turla/Snake didn’t address how victims were getting infected in the first place, or the role Epic Turla/Tavdig played in the infection path.
Kaspersky Lab researchers believe Epic Turla is the first of many malicious components used by the Turla/Uroburos cyber-espionage campaign to compromise the victim and take full control of the infected system, said Kurt Baumgartner, a researcher at Kaspersky Lab.
 New research indicates that the cyber-espionage campaign has three distinct parts, with Epic Turla as the early-stage infection mechanism, and Cobra Carbon system/Pfinet and others as intermediary components upgrading functionality and communications capabilities. Snake is the “high-grade” malware platform, which included a rootkit and virtual file systems, Baumgartner said.
New research indicates that the cyber-espionage campaign has three distinct parts, with Epic Turla as the early-stage infection mechanism, and Cobra Carbon system/Pfinet and others as intermediary components upgrading functionality and communications capabilities. Snake is the “high-grade” malware platform, which included a rootkit and virtual file systems, Baumgartner said.
Attackers behind Epic Turla have used zero-day exploits, spear-phishing emails, and watering hole tactics to infect victims, Baumgartner said. Zero-day exploits include one triggering an escalation of privileges flaw in Windows XP and Windows Server 2003 (CVE-2013-5065) and another targeting Adobe Reader (CVE-2013-3346). The escalation of privileges exploit gives the Epic malware administrator privileges on the infect system and the Reader exploit affects how email attachments are viewed, her said. While Kaspersky Lab has uncovered the malicious PDF files, researchers have not yet been able to track down the attack emails themselves.
More than 100 injected websites were used to deliver Epic Turla, with the largest number of injected sites in Romania, Baumgartner said.
Detected attacks in this campaign include spear phishing emails targeting Adobe Reader, social engineering tricks to install malware from files with the .SCR extension, and watering hole attacks that convince users into running fake Flash Player installers or using exploits for Java, Adobe Flash, or Internet Explorer 6,7, and 8.
Some of the backdoors used in the campaign have names such as “WorldCupSec”, “TadjMakhal”, “Wipbot” and “Tadvig.” The malicious email attachments have file names such as, NATO position on Syria.scr, Talking Points.scr and border_security_protocol.rar.
“These filenames can provide clues about the type of victims the attackers are targeting,” Baumgartner said.
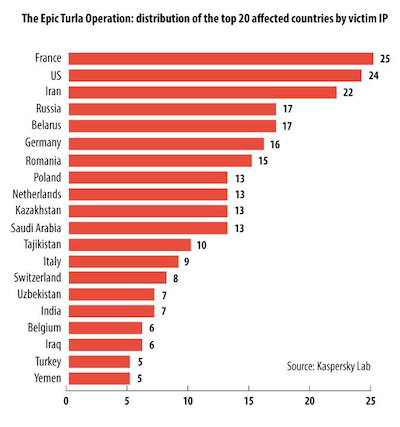
When examining victim IP addresses, Kaspersky researchers found that the majority of the victims were in Europe and the Middle East, with France, United States, and Iran topping the list. Several hundred victim IP addresses were distributed across more than 45 different countries, including Russia, Belarus, Germany, Romania, Poland, Netherlands, Kazakhstan, and Saudi Arabia, to name a few.
“Epic” targeted individuals in government entities, such as the Ministry of Interior, Ministry of Trade and Commerce, Ministry of Foreign/External affairs, and intelligence agencies, as well as embassies, military groups, research and education organizations and pharmaceutical companies. The C&C redirects to a currently suspended page, but is still online, Baumgartner said.
Research from Symantec echoed much of what Kaspersky Lab had seen. According to Symantec, many Turla infections in Western Europe occurred on computers connected to private government networks of former Eastern Bloc countries.
“These infections appear to have transpired in the embassies of these countries,” Symantec said. “Analysis of infections revealed that the attackers were heavily focused on a small number of countries. For example, in May of 2012, the office of the prime minister of a former Soviet Union member country was infected. This infection spread rapidly and up to 60 computers at the prime minister’s office were compromised.”
Other infections include a computer at the embassy to France of a second former Soviet Union member in late 2012. In 2013, Symantec said infections began to spread to other computers linked to the network of the country’s ministry of foreign affairs, and that its ministry of internal affairs was also infected.
The attackers do not appear to be native English speakers, and the backdoors hint the malware developers may have a Russian background. The internal name of one of the Epic backdoors is “Zagruzchik.dll”, which means “bootloader” or “load program” in Russian, the company noted. Kaspersky Lab also believes there may be possible connections with different cyber-espionage campaigns, such as Miniduke, which used the same Web shells to manage infected web servers.
Once Epic infects a machine, the malware connects to a command-and-control server and sends information about the victim machine. The C&C then send a customized cocktail of backdoors and exploits specific to the software installed on the machine. Kaspersky observed that Epic attempted to download a sophisticated backdoor known as Cobra/Carbon (or Pfinet) and update Carbon’s configuration file with information about different C&C servers.
“The Epic Turla is used to gain a foothold and validate the high profile victim. If the victim is interesting, it gets upgraded to the full Turla Carbon system,” explained Costin Raiu, Director of the Global Research and Analysis Team at Kaspersky Lab.
In March 2104, it was reported that dozens of computer networks in Ukraine were infected by the Snake malware.
Kaspersky Lab previously said that it first became aware of the cyber espionage campaign in March 2013, when the company’s experts were investigating an incident involving a highly sophisticated rootkit.
The attack was detected against a Kaspersky Lab user on August 5, 2014, indicating the operation remains fresh and ongoing, the company noted in a blog post.
According to Symantec, Turla is an evolution of an older piece of malware detected by the firm as Trojan.Minit, which they say has been in operation since 2004.
“The current campaign is the work of a well-resourced and technically competent attack group that is capable of penetrating many network defenses. It is focused on targets that would be of interest to a nation state, with spying and theft of sensitive data among its objectives,” Symantec wrote in a blog post Thursday afternoon.
*Updated with additional information from Symantec. Additional reporting by Mike Lennon















