PRAGUE – Virus Bulletin 2015 – Gatekeeper, the security feature designed to protect OS X users against malware downloaded from the Internet, can be easily bypassed by malicious actors, a researcher has warned.
Gatekeeper is designed to automatically block applications downloaded from the Internet if they come from an unknown developer or if they’ve been tampered with. Gatekeeper checks if these conditions are met after the file is quarantined, a process that most downloaded files go through.
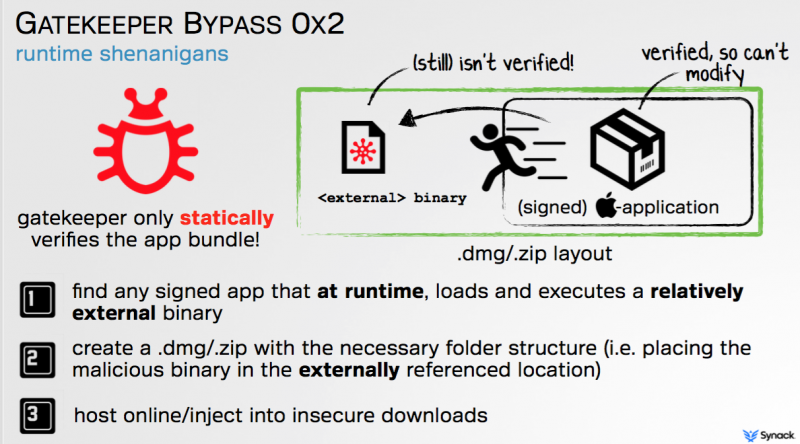
The problem, according to Patrick Wardle, director of research at Synack, is that Gatekeeper only statically verifies the app bundle, without ensuring that it doesn’t execute a relatively external binary.
This allows an attacker to deliver OS X malware to users by following three steps. First, they must find a signed application that loads and executes an external binary at runtime. Then, they create a .dmg file in which the external binary is replaced with a file containing the malicious code they want to execute (e.g. keylogger). Finally, they can deliver the malicious .dmg file to victims by hosting it on third-party app stores or by injecting it into insecure download connections.
The expert initially tested his findings on Adobe Photoshop, which is allowed by Gatekeeper to execute because it’s signed by a known developer. However, Photoshop is designed to load plugins after it’s executed and these plugins are not validated by Gatekeeper, allowing an attacker to leverage these components to load malicious code.
Some might argue that using Photoshop as an attack vector might not be very efficient, so Wardle identified a command-line app signed by Apple that could be used in the same way.
In order to avoid raising suspicion, the attacker can set a top-level alias to the malicious app, change its icon and background, and rename its extension to .app to ensure that the victim doesn’t see a terminal window in case the Apple-signed application exploited in the attack is a command-line tool.
Wardle told SecurityWeek that he reported his findings to Apple at the middle of summer, but the issue appears to remain unfixed even in the latest version of OS X, dubbed “El Capitan.” The expert says Synack has a 60-day vulnerability disclosure deadline, which is why he disclosed the details of the attack at the Virus Bulletin conference in Prague on Thursday. Some limited information on this issue was also presented at the Black Hat conference in August.
One day before his presentation at Virus Bulletin, Apple asked the expert to redact the name of the app he used for proof-of-concept in his slides. The researcher has agreed not to disclose the name of the app, but he believes there could be numerous applications signed by Apple that can facilitate such an attack.
The expert believes that the best way to prevent such attacks is for Apple to validate all binaries at runtime to ensure that no unsigned binaries are executed. Until Apple releases a fix, users are advised to only download software from trusted sources, and ensure such downloads are secured (i.e. are done over HTTPS).
Wardle previously disclosed a somewhat similar Gatekeeper bypass technique involving dynamic library (dylib) hijacking. The researcher has developed a series of tools that can be used to determine what software is installed persistently on a Mac, explore all running processes, protect devices against malware by continually monitoring persistence locations, and scan devices for applications vulnerable to dylib hijacking.














