Container security company Prevasio has analyzed 4 million public Docker container images hosted on Docker Hub and found that over half of them had critical vulnerabilities and thousands of images included malicious or potentially harmful elements.
The cybersecurity firm used its Prevasio Analyzer service to analyze all the container images on Docker Hub, the largest library and community for container images. In order to analyze the large amount of images, the Prevasio service ran non-stop for one month on 800 machines.
The analysis found that 51% of the 4 million images included packages or app dependencies with at least one critical vulnerability and 13% had high-severity flaws.
Roughly 6,400 containers, representing 0.16% of the total, were classified as malicious or potentially harmful due to the presence of malware, cryptocurrency miners, hacking tools, a malicious npm package (flatmap-stream), and trojanized applications.
According to Prevasio, these malicious or potentially harmful Docker images have been downloaded more than 300 million times.
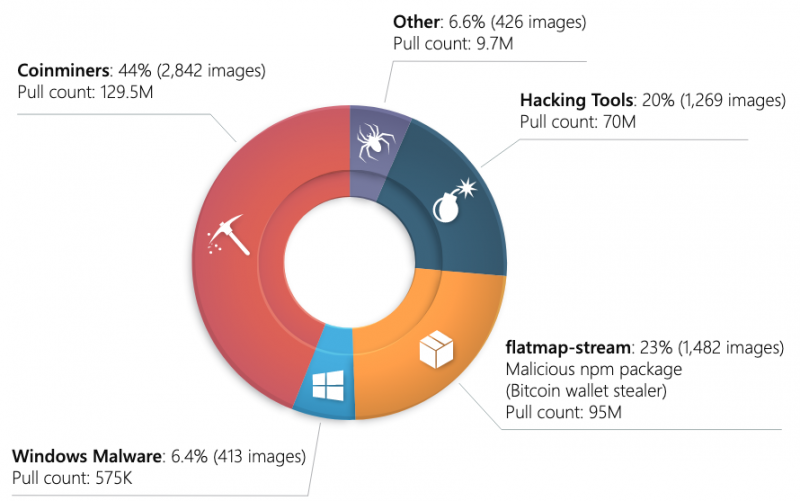
Crypto-miners were detected in 44% of the 6,400 containers and while in many cases developers clearly state that their container images contain these miners, the miners are often hidden.
“Regardless of the original intention, if an employee pulls from Docker Hub and then runs a coinmining container image at work, there is a very high chance that the company’s resources are not used as originally intended. A system administrator might find such container images undesirable for a corporate environment or even potentially harmful,” Prevasio wrote in a report detailing its findings.
The research also uncovered images with dynamic payloads, where the original image does not appear to include anything malicious, but they are scripted to — at runtime — download the source code of a miner, compile it, and execute it.
As for trojanized applications, the analysis uncovered trojanized WordPress plugins, Apache Tomcat, and Jenkins. While much of the malware currently found in the images targets Windows, malware could pose a bigger issue in the future with the rise of cross-platform threats.
“If a company’s developer takes a shortcut by fetching a pre-built image, instead of composing a new image from scratch, there is a viable risk that such pre-built image might come pre-trojanised. If such an image ends up in production, the attackers may potentially be able to access such containerized applications remotely via a backdoor,” Prevasio warned.
Related: ‘Graboid’ Crypto-Jacking Worm Targets Docker Hosts
Related: Misconfigured Docker Registries Expose Thousands of Repositories












