With a fresh Series B funding round of $10 million, winner of this year’s “Most Innovative Company” at the RSA Conference, Altor Networks, has just introduced the latest version of its flagship security product for virtual data centers and clouds.
Due to concerns about security and compliance within virtualized environments, CIOs, CISOs and IT Directors want to be certain that the measures for auditing and protecting virtualized servers are equivalent to what is in place for the physical network. By unplugging the physical connections in the virtualization process, many enterprises are opening themselves to vulnerabilities and “blind spots” in their infrastructures that they’re often unaware of.
In a March 2010 report, Gartner predicts that through 2012, 60 percent of virtualized servers will be less secure than the physical servers they replace.
The Redwood Shores, California based company aims to address these issues and concerns with the release of Altor 4.0, the next iteration of its virtual server security product. Altor 4.0 includes a high performance stateful firewall and on board intrusion detection with complete virtual network visibility and monitoring, automated security and compliance assessment and reporting. This release is specifically designed to address the security concerns innate to a virtualized or cloud environment.
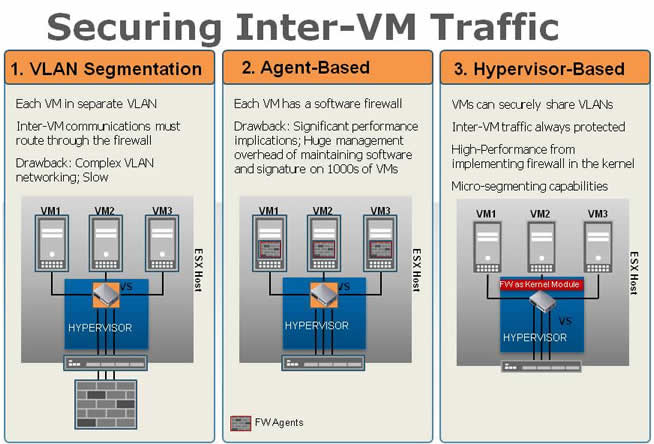
Leveraging a hypervisor-based footprint, Altor 4.0 helps detect unauthorized changes to VMs in virtual and cloud environments, and can selectively quarantine the offending VMs while alerting IT about the policy violations. Altor 4.0 also inspects all traffic to and from each VM to eliminate blind spots, and enforces policies at the global, group, and per-VM level. With Altor 4.0, enterprises can granularly define security policies within zones of trust and precisely control how VMs within these zones can communicate with one another, ensuring isolation between and within trust levels and allowing for precise micro-segmentation.
“More and more companies are broadening their virtualization deployment across the IT infrastructure,” said Brett Waldman, senior research analyst for Software Appliances and Virtualization at IDC. “However, as companies virtualization solutions mature towards a private cloud scenario, they are finding existing networking and security solutions are being stressed to their limits. Simultaneously, VM density is increasing per server, putting more eggs into a single basket and making each server a mission-critical server. To address these challenges it is time for a new security paradigm purpose-built for virtualization.”
By leveraging Introspection to collect VM attributes, such as installed applications, and coupling it with Altor’s knowledge of the virtual network, Altor 4.0 creates a database of control points by which security policies and compliance rules can be defined. Altor makes this rich data available in intuitive user interfaces (UIs) that let administrators build the entire range of policies from corporate rules on global protocol handling to discrete regulation and compliance driven policies for how VMs should be configured. Built-in templates help jumpstart the process of building policies while tools assist in customizing the rulesets.
As far as performance, Altor 4.0 consumes only 3% of total system throughput at full capacity and the same hardware can support the same number of virtual machines with or without Altor installed. Performance can be attributed to the product being Hypervisor-based and “agent-less,” requiring no additional software to be installed in the virtual machine itself.
Pricing starts at $1,500 per CPU socket. Altor 4.0 will be available in early Q3’10 with a beta evaluation version currently available for download.
In addition to winning the award of “Most Innovative Company” at the 2010 RSA Conference, it was also recently named to Gartner’s “Cool Vendors in Data and Infrastructure Protection” list. Altor Networks was founded in 2007 by former execs and engineers from Check Point Software, Cisco and Oracle.












