Akamai Introduces Integrated Security Suite Designed to Help Enterprises Defend Against DDoS and Application Security Attacks
Akamai Technologies today introduced Kona Site Defender, a new suite of security services designed to provide Distributed Denial of Service (DDoS) attack mitigation and Web application security protections.
Kona, playing off the Hawaiian branding of the company (Akamai means “clever” or “cool” in Hawaiian), is designed for enterprises that need to ensure Web sites and applications remain online and available in the face of increasing attacks, and that associated data is kept secure.
 Powering Akamai’s security offerings is a massive global network of over 100,000 servers that makes up what the company calls the “Akamai Intelligent Platform”.
Powering Akamai’s security offerings is a massive global network of over 100,000 servers that makes up what the company calls the “Akamai Intelligent Platform”.
The secret sauce in how Site Defender stops multi-vector DDoS attacks, is that the platform only accepts valid HTTP and HTTPS requests on port 80 and port 443, and ignores network layer attacks such as TCP SYN floods, UDP floods, and other network packet based attacks.
For example, Kona Site Defender will help defend against the Low Orbit Ion Cannon (LOIC), a favorite attack tool used by hacker collective Anonymous. LOIC was originally developed by the “good guys” to stress test websites, but is often used by Anonymous to take its targets offline by sending a flood of TCP/UDP packets in an attempt to overwhelm a system and make it inaccessible. Anonymous has had much success taking down targets, including recent attacks on Music industry sites, Government sites, and more. LOIC has recently even been ported to Android, enabling attacks to be launched from mobile devices, or even a Web browser.
In addition to large scale attacks, other Denial of Service attacks can take a site offline with relatively little firepower and scale. In fact, a recent report from Radware showed that when it comes to DDoS attacks, size doesn’t always matter. According to Radware, a smaller attack can actually cause more damage than DDoS attacks that gobble ten times the amount of bandwidth, noting that a much smaller HTTP flood on the application level may do more damage than a larger UDP flood on the network.
Akamai’s platform is designed to address these application layer attacks, including built-in protections against HTTP “slow client” attacks (e.g. Slowloris) and HTTP Request Smuggling attacks.
Also on the application layer, Akamai’s Web Application Firewall (WAF) helps defend against attacks such as SQL injection and cross site scripting, and provides approximately 100 rules that can be configured to protect against things such as HTTP protocol violation protections, HTTP request limits, HTTP policy limits, and other malicious HTTP attacks. The WAF also helps protect against scanners and bad robots, Trojans, and includes outbound content protections.
Akamai’s web application firewall can also block requests based on the geographic location of the IP address and define custom rules for individual Web applications.
Kona Site Defender helps protects customers from some of the potential costs associated with bursting fees that could be caused by a DDoS attack and can prevent customers from incurring a performance penalty often associated with other mitigation methods such as traffic scrubbing. Deployed natively in the existing traffic path, Akamai eliminates the need for traffic rerouting, preventing additional latency and incurring no single point of failure.
Also part of the suite, Kona Site Defender includes a new Security Monitor, a tool built on Akamai’s Media Analytics platform that provides a real-time look into Web sites or applications that may be under attack, and provide visibility into the nature and source of the attack. IT security teams can drill down into attack alerts to view detailed information on the origin of attacks, what assets are being attacked, and what triggered site defenses. Log data is archived and available for 90 days to aid in post-attack analysis, the company said.
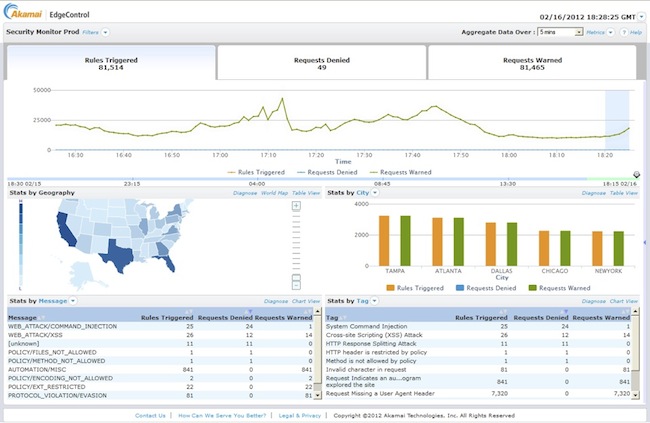
By monitoring the rate of requests coming from individual IP addresses and gathering statistics about each, Site Defender adds another layer of defense by being able to block client IPs identified and flagged as malicious as a result of behavior such as sending too many requests per second or causing too many origin errors.
“Attackers don’t stay on one layer anymore; they tend to include both network and application-based techniques, which makes defending against them more complicated,” said Wendy Nather, research director of 451 Research’s Enterprise Security Practice.
“We’re in a position to handle low and slow or fast and big attacks,” Jeff Aliber, senior product marketing manager at Akamai, told SecurityWeek. “On a daily basis we are handling traffic close to 6TB/s and spike well over 8TB/s without the platform even yawning,” Aliber added.
For readers who will be attending the RSA Conference next week in San Francisco, Akamai will be demonstrating Kona Site Defender and running live attacks so you can see the tool in action. Industry experts, Jeremiah Grossman of WhiteHat Security and Ryan Barnett and Nicholas Percoco of Trustwave SpiderLabs who helped design the attacks, will be on hand to discuss how Web attacks are evolving and the challenges in defending against such attacks.
Kona Site Defender will be generally available April 11, 2012, and customers looking to utilize the solution don’t need to be an existing Akamai client or utilize the company’s acceleration and optimization services.












