What could be less threatening than the old office fax machine? Nothing. That’s precisely why it’s used as a backdoor for hackers to get into an organization’s network.
Check Point, a cyber security firm in Israel, said Sunday that their research discovered security flaws in tens of millions of fax machines.
The hack works by sending an image file through the phone line — or a file that the fax machine thinks is an image file — and that is coded to contain malicious software. When a company receives the photo, the image is decoded and uploaded into the fax-printer’s memory, allowing the hackers to take over the device and spreading the malicious code through the network.
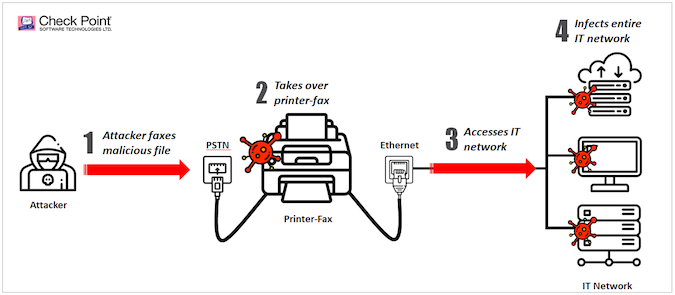
“Many companies may not even be aware they have a fax machine connected to their network, but fax capability is built into many multifunction office and home printers,” said Yaniv Balmas, group manager of security research at Check Point.
The researchers focused on Hewlett Packard’s OfficeJet Pro all-in-one fax printers — the global market leader for fax machines. Hewlett Packard quickly fixed the issue — a patch is available on their support page — but the same vulnerabilities are present in most fax machines, including those by Canon and Epson.
Many machines are too old to even update. That means it will be difficult for companies to stop hackers from entering their system.
Globally, businesses use an estimated 45 million fax machines. Faxes are still widely used in healthcare, banking, and law, sectors in which highly sensitive data is stored. In the U.S. medical sector, 75 percent of all communications are sent by fax.
To prevent organizations’ networks from becoming compromised, experts recommend that companies check if their fax machines can be updated, or place fax devices on a secure network that is separate from the networks that carry sensitive information.















