
Point-of-sale (PoS) attacks are declining, while Web application attacks and cyber-espionage is increasing, according to the latest edition of the annual Verizon Data Breach Investigations Report (DBIR).
The highlight of this year’s report, however, is not the data breach numbers, but the industry-by-industry analysis of various threat types.
Verizon RISK team researchers found that 92 percent of security incidents from the past 10 years could be categorized in one of nine “threat patterns,” or attack types, according to the Verizon 2014 Data Breach Investigations Report released Tuesday.
The nine threat patterns identified by Verizon include: user errors such as sending an email to the wrong person, crimeware designed to gain control of targeted systems, insider threats and privilege misuse, physical theft or lost devices, Web application attacks, denial of service attacks, cyber-espionage, point-of-sale intrusions, and payment card skimmers.
In previous years, the highly regarded report from Verizon focused on actual data breaches investigated by either Verizon’s security team or by one of its global partners. This year, the team decided to expand the report definition to include security incidents that didn’t result in breaches in order to “gain a better understanding of the cybersecurity landscape,” Marc Spitler, a senior risk analyst with Verizon’s RISK team, told SecurityWeek.
The report utilized two data sets; the first set looked at 1,367 confirmed data breaches and 63,437 security incidents from 2013. The second data set looked at over ten years of data, or about 3,800 data breaches and 100,000 security incidents. The data came from over 50 different sources and covers 95 countries, Spitler said.
“This evolution of the DBIR reflects the experience of many security practitioners and executives who know that an incident needn’t result in data exfiltration for it to have a significant impact on the targeted business,” the report said.
The 2013 Numbers
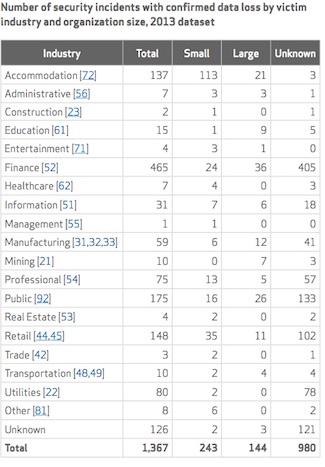 In the 2013 data set, researchers found that the public sector had the most security incidents, with 47,479 incidents. The financial services sector had the highest number of data breaches in 2013, the report found, followed by the public sector and retail.
In the 2013 data set, researchers found that the public sector had the most security incidents, with 47,479 incidents. The financial services sector had the highest number of data breaches in 2013, the report found, followed by the public sector and retail.
As expected, there were increases in attacks against specific industry sectors, especially those that are more attractive to financially-motivated adversaries because they store payment card or other financial data. Even so, there weren’t any sectors “flying completely under the radar,” the report found. The real takeaway of the report was that everyone was vulnerable to some kind of event, the researchers concluded.
“Organizations need to realize no one is immune from a data breach,” Wade Baker, principal author of the Data Breach Investigations Report, said in a statement. Even if the organization is at low risk for one type of attack, such as by an external attack, there is still the possibility of insider misuse and errors.
Not The DBIR We Know
The bulk of the new and revamped DBIR examined patterns that came out from analyzing ten years of data. “This year’s report offers unparalleled perspective into the world of cybercrime, based on big data analysis,” Eddie Schwartz, vice president of global cybersecurity and consulting solutions at Verizon Enterprise Solutions, said in a statement.
Instead of looking at trends such as spikes in types of malware or how often specific types of attacks occur, researchers focused on incident patterns, Spitler said. In previous years, researchers focused on actor types, behavior, and targeted assets, such as identifying hacking, nation-state actors, and compromised laptops as various categories. This year, researchers identified common patterns and then identified the various actors associated with the attack types, the actions the actors took, the assets they targeted, and the timeline for the attacks. Instead of saying that SQL injection is prevalent 90 percent of the time, “which is not actionable,” the report identified attacks against Web apps as a pattern, and then identified how some actors may use SQL injection, Spitler said.
“We took the information and brought in a different way of looking at the data,” Spitler said.
There were three reasons for changing the report focus and format, according to Verizon. Researchers found that the vast majority of incidents could be placed into one of nine patterns, and that it was possible to draw a correlation between incident patterns and industries, Spitler said. Finally, the goal of the new report was to provide “actionable information” and specific recommendations that organizations can use to defend against the threats, he said.
“After analyzing 10 years of data, we realize most organizations cannot keep up with cybercrime – and the bad guys are winning,” Baker said. By applying big data analytics to security risk management, organizations would be able to “combat cybercrime more effectively and strategically,” he said.
Mapping Incidents to Industry
The prevalence of the pattern varied from industry to industry. For example, the biggest threats affecting healthcare organizations were physical theft and loss, at 46 percent, followed by insider misuse and error, at 15 percent and 12 percent, respectively. In contrast, PoS attacks accounted for 75 percent of incidents in accommodation sector, followed by denial of service at 10 percent and insider misuse at 8 percent. Theft or loss accounted for just 1 percent. The education sector, on the other hand, was almost evenly split between Web app attacks, user error, and “everything else,” according to the report.
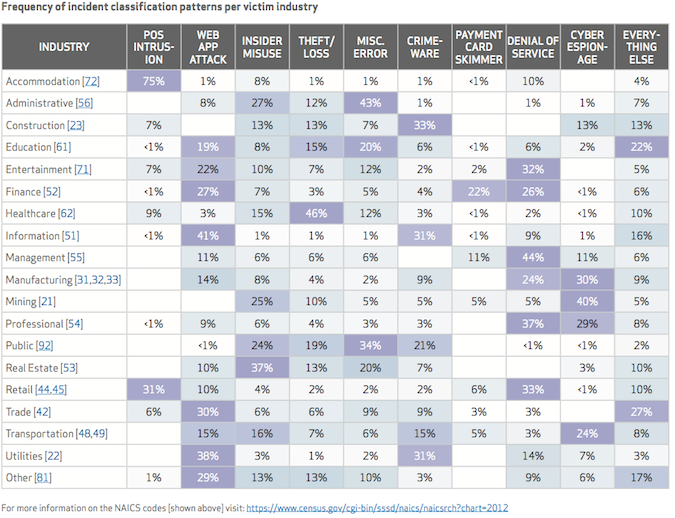
Mapping incidents to industries shows which incident patterns are more common for which industries, making it easier for organizations reading the report to read sections of the report most relevant to their sector, Spitler said.
Researchers also found that on average, 72 percent of the incidents in any industry fell into one of three patterns. In the financial services sector, 75 percent of the incidents came from Web application attacks, distributed denial of service (DDoS) and payment card skimming. For retail organizations, the most prevalent pattern was DDoS, accounting for 33 percent of incidents, followed by PoS attacks, at 31 percent. A little over half of all manufacturing attacks could be traced to either cyber-espionage or DDoS, the report found.
Types, Methods, and Targets
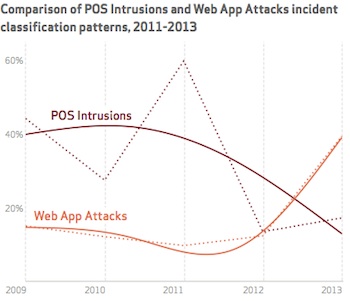
The use of stolen and/or misused credentials (user name/passwords) continues to be the No. 1 way to gain access to information. Two out of three breaches exploit weak or stolen passwords, making a case for strong two-factor authentication.
Despite the increased focus on PoS attacks in 2013, retail PoS attacks continued its decline, according to the DBIR. “While POS breaches have been in the headlines lately, it is not indicative of the actual picture of cybercrime,” the report concluded.
Researchers also found that while external attacks still outnumbered insider threats, those cases are increasing, especially in cases of intellectual property. Almost 85 percent of insider and privilege-abuse attacks used the corporate LAN, and 22 percent took advantage of physical access, the report found. Verizon also included DDoS attacks for the first time in the DBIR, noting that they commonly target financial services, retail, professional, information and public sector industries.
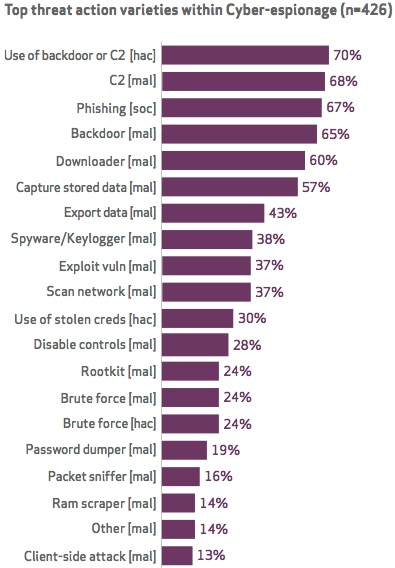 Cyber-espionage turned out to be a complex and diverse category, with a long list of threat patterns, Verizon found. (figure 60) While China remained the most active source of cyber-espionage activity, other regions of the world appeared in the report, including Eastern Europe.
Cyber-espionage turned out to be a complex and diverse category, with a long list of threat patterns, Verizon found. (figure 60) While China remained the most active source of cyber-espionage activity, other regions of the world appeared in the report, including Eastern Europe.
A Broader, In-Depth Look
There are many threat reports from a variety of sources. Despite using some of the same data sources, DBIR remains unique because it provides deeper and broader insights, Spitler said. The sheer volume of incidents the report examines and the number of sources minimizes any biases that may exist in the data.
The report gives organizations hard data about what threats they need to worry about, Spitler said. Previously, someone could argue that data loss prevention would be important for public sector organization but not be able to back up the information. DBIR now provides that person with actual numbers showing that misuse, theft/loss, and error are all big issues for the public sector, which makes for a more convincing argument.
Organizations can also use the report to ask, “Based on where my industry is now (which reflects the controls already in place and the threats they often face), what should we focus on next?”
“It’s fascinating to study what goes wrong,” the report concludes. “But the real purpose of this research is to help you reduce the risk that these bad things will happen to you. At the end of the day, we do this work to support evidence-based risk management. We think the perspective of studying clustered incident patterns enables more tailored strategies to reduce risk, and toward that end, we did two specific things this year.”
The full report is available online in PDF format.













