Symantec has released details of an extremely sophisticated cyber espionage tool that the company says has been used in “systematic spying campaigns” against a range of international targets since at least 2008.
The malware, dubbed “Regin” by Symantec, is a back door-type Trojan whose structure displays a degree of technical competence rarely seen, indicating that a nation state is behind it.
In a report released Sunday by Symantec, Regin was described as an “extremely complex piece of software that can be customized with a wide range of different capabilities that can be deployed depending on the target.”
Symantec first got its hands on the threat back in December 2013, when a customer submitted the file to Symantec for analysis, Liam O’Murchu, a security researcher and malware analysis expert at Symantec, told SecurityWeek.
Threats of this nature are rare and are only comparable to the Stuxnet/Duqu family of malware, Symantec said, however O’Murchu said Regin does not appear to share any common code with those threats.
An advanced spying tool, Regin has been used in spying operations against governments, infrastructure operators, businesses, researchers, and private individuals.
The design and operation of Regin makes it highly suited for persistent, long term surveillance operations against targets, and would have required a significant investment of time and resources to build and deploy. Some of Regin’s custom payloads indicate that its developers had a high level of knowledge in particular sectors, such as telecoms infrastructure software, Symantec said in its report (PDF).
Symantec observed infections a variety of organizations between 2008 and 2011, after which it was “abruptly withdrawn.” A new version of the malware resurfaced in 2013, which has been used against targets including private companies, government entities and research institutes, Symantec said.
Infection Locations
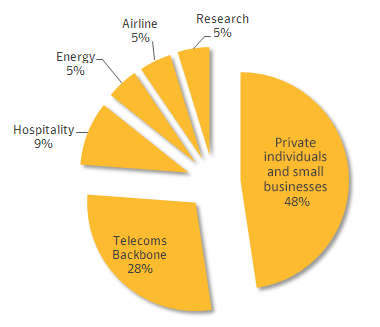
Interestingly, roughly half of the infections targeted private individuals and small businesses, and attacks on telecoms companies appear to be designed to gain access to calls being routed through their infrastructure.
Confirmed Regin infections by sector
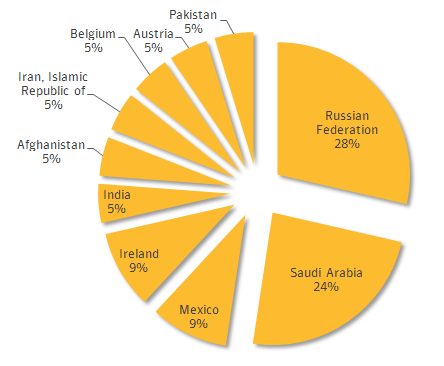
The highest percentage of infections discovered was in Russia (28 percent), followed by Saudi Arabia at 24 percent. Regin was also found found included Mexico, Ireland, India, Afghanistan, Iran, Belgium, Austria and Pakistan.
According to the report, there were no confirmed infections in the United States or the UK.
Confirmed Regin Infections by Country
Regin is a multi-staged, modular threat and has a number of components, each depending on others, to perform attack operations. The cyber attack platform was built using a six-stage architecture, each stage of which is hidden and encrypted, with the exception of the first stage.
“Executing the first stage starts a domino chain of decryption and loading of each subsequent stage for a total of five stages,” the report explained.”
“The initial stages involve the installation and configuration of the threat’s internal services. The later stages bring Regin’s main payloads into play.”
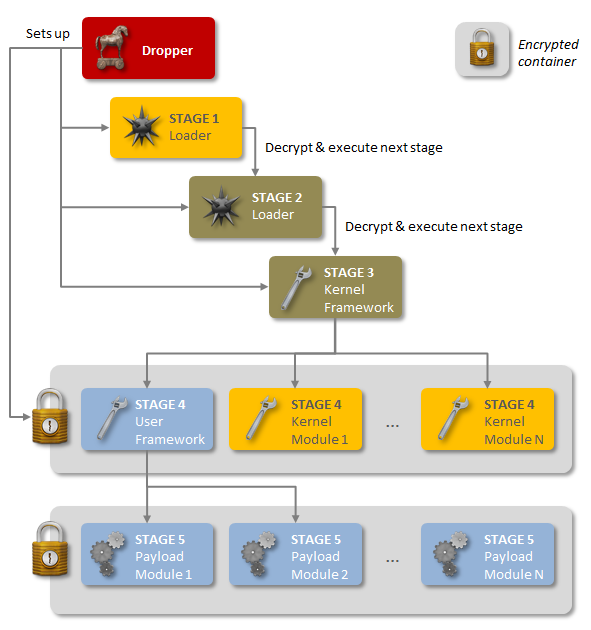
Regin also uses a modular approach, allowing it to load custom features tailored to specific targets.
Infection vector and payloads
Symantec said they have not yet been able to determine the threat vector used to infect systems at the time of publishing its report, but believes the attackers used various tactics among targets, and that some may be tricked into visiting spoofed versions of well-known websites and the threat may be installed through a Web browser or by exploiting an application.
One system analyzed by Symantec had log files showing that a Regin infection originated from Yahoo! Instant via an unconfirmed exploit.
Regin uses a modular approach, giving flexibility to the threat operators as they can load custom features tailored to individual targets when required.
According to Symantec, there are dozens of Regin payloads. The threat’s standard capabilities include several Remote Access Trojan (RAT) features, such as capturing screenshots, taking control of the mouse’s point-and-click functions, stealing passwords, monitoring network traffic, and recovering deleted files.
“It took us a long time to try and get the pieces of the puzzle and put them together,” O’Murchu said. “We have a lot of payload modules, but we believe other people have difference modules than we have, and we’d like to get more information about these modules and payloads and how they interact.”
Symantec said that advanced payload modules exist, including a Microsoft IIS web server traffic monitor and a traffic sniffer of the administration of mobile telephone base station controllers.
Stealth
Regin’s developers put considerable effort into making the threat difficult to detect and analyze, Symantec said, including several “stealth” features such as anti-forensics capabilities, a custom-built encrypted virtual file system (EVFS), and alternative encryption in the form of a variant of RC5.
Command and Control (C&C)
Regin uses multiple sophisticated means to secretly communicate with the attacker including via ICMP/ping, embedding commands in HTTP cookies, and custom TCP and UDP protocols, the report noted.
“Rather than the infected computer having to connect out to the command and control server and needing to know where that command and control server is located, the attackers can actually send a ping into the affected computer and say ‘hey this is where the command and control server is setup today and we want you to setup an SSL connection to the command and control server,’ and then tomorrow they could lose the command and control server again,” O’Murchu said.
This setup makes the Command and Control server very dynamic and essentially allows the attackers to move the C&C server by the minute and hide their tracks.
“The discovery of Regin serves to highlight how significant investments continue to be made into the development of tools for use in intelligence gathering,” the report concluded.
Symantec also warned that many components of Regin have still gone undiscovered and additional functionality and versions may exist.















