The Verizon Data Breach Investigations Report (DBIR) is industry’s go-to analysis of security incidents and successful breaches over the previous year. The latest report was published Thursday.
The 2017 DBIR (PDF) marks the report’s 10-year anniversary. Over the last decade, it has grown from an analysis of Verizon’s own breach data knowledgebase to now include breach data from 65 different organizations. The latest report includes analyses of 42,068 incidents and 1,935 breaches from 84 countries.
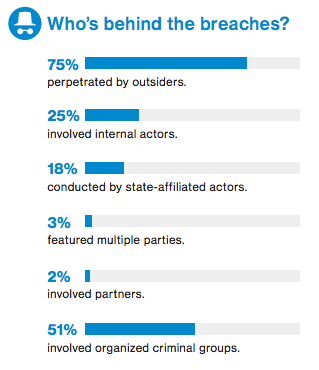
Highlights show that the insider threat remains fairly constant as the cause of 25% of breaches, but with 75% being perpetrated by outsiders. The externally-caused breaches, according to Verizon, comprise 51% involving organized crime groups, 18% from state-affiliated actors, 3% comprising multiple parties, and 2% involving partners.
 Sixty-two percent of all breaches involved hacking; and 81% of those leveraged either stolen and/or weak passwords. The clear implication is that both organizations and individuals are still, or at least in 2016, were still not exercising adequate password hygiene; that is, strong and regularly changed passwords.
Sixty-two percent of all breaches involved hacking; and 81% of those leveraged either stolen and/or weak passwords. The clear implication is that both organizations and individuals are still, or at least in 2016, were still not exercising adequate password hygiene; that is, strong and regularly changed passwords.
Verizon’s figures show that the finance sector is the most frequently breached vertical. Twenty-four percent of breaches affected financial organizations. This was followed by healthcare at 15%; retail and accommodation combined at 15%; and public entities at 12%.
Other key statistics highlighted by Verizon include most of malware is installed via malicious email (66%); an even higher percentage (73%) of breaches are financially motivated; and that 21% were related to cyberespionage.
Verizon hopes that these statistics on recent breaches can help practitioners better protect their organizations today.
“Insights provided in the DBIR are leveling the cybersecurity playing field,” said George Fischer, president of Verizon Enterprise Solutions. “Our data is giving governments and organizations the information they need to anticipate cyberattacks and more effectively mitigate cyber-risk. By analyzing data from our own security team and that of other leading security practitioners from around the world, we’re able to offer valuable intelligence that can be used to transform an organization’s risk profile.”
This intent is further aided by a breakdown of methods used to attack the different vertical sectors. For example, the report notes that the accommodation and food services sector “was dominated by POS breaches. Most of them are opportunistic and financially motivated and involve primarily malware and hacking threat actions. Time-to-compromise is quick but time-to-discovery and containment remains in the months category.”
One frequently highlighted attack vector is the web application attack, noted particularly in the financial and insurance; information; and retail sectors. “Attackers are always looking for the weakest link in your IT infrastructure, before leveraging expensive 0-days and complicated APT attacks,” explains Ilia Kolochenko, CEO of High-Tech Bridge. “Today, the majority of large organizations and governments can be easily breached via their web and mobile (backend) applications.”
He adds that this attack vector is still growing with the increasing use of third-party cloud services and applications, “which are exploited by hackers to compromise your trusted third-party and get access to your data afterwards… The report confirms Google’s research, which found a 32% increase in website hacking in 2016. Application security becomes a major problem for organizations and should be addressed as a high priority,” he suggests.
If there is any weakness in the DBIR as a guide for what to do today, it is that DBIR is an historical analysis of what has already happened in the recent past. For example, the report states that 51% of breaches included malware. On its own, this could persuade organizations to beef up their anti-malware defenses. However, because the analysis looks at past breaches rather than current threats, there is no clear indication of the current growth in non-malware attacks. Anti-malware defenses will not detect such attacks (which typically might use OS apps such as PowerShell) because there is no malware to detect.
Another example could be ransomware. Ransomware is difficult to place in the analysis because it is not a breach within Verizon’s definition of breach (actual exfiltration of data), but clearly more than an incident. Furthermore, it is not unusual for infected organizations to decline to disclose the incident — both of which factors could affect Verizon’s statistics. To solve this issue, Verizon used telemetry data from McAFee for its information source.
McAfee’s figures confirmed Verizon’s own statistics — that is, that the incidence of ransomware continues to rise — but McAfee can provide greater detail. The difference is that McAfee’s telemetry provides threat statistics, while the DBIR provides breach statistics. To get a complete view of the current situation, organizations need to consider both recent breaches and currently evolving threats.
Nevertheless, DBIR remains an invaluable resource for security practitioners. “From the beginning, it concludes, “our primary goal was, and still remains, to help organizations understand the threats they are facing, and enable them to make sound evidence-based risk management decisions.”












