Report Details How Attackers Can Mask Dangerous Threat Activity
Network security firm Palo Alto Networks has released the latest version of its Application Usage and Threat Report, which sheds light on how attackers are exploiting commonly-used business applications to bypass security controls.
According to the report released Monday, common sharing applications such as e-mail, social media, and video remain the attack vehicles of choice for cybercriminals, but are often only the start of multi-phased attacks rather than the focus of threat activity.
“This isn’t really groundbreaking, but we think it’s important for people to understand that threats coming into your network and the data going out of your network are often through completely different means,” Ryan Olson, head of threat intelligence at Palo Alto Networks, told SecurityWeek.
“You really need to have good visibility to tie those together and understand all the applications that are on your network and inspect that traffic,” Olson said.
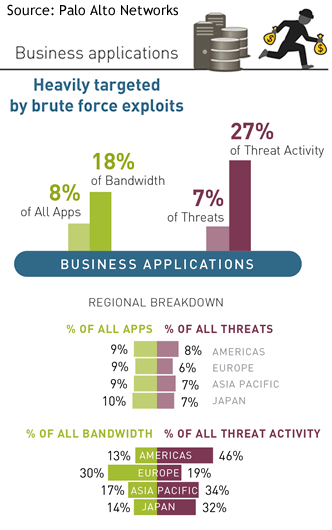 “Our research shows an inextricable link between commonly-used enterprise applications and cyber threats,” explained Matt Keil, senior research analyst at Palo Alto Networks. “Most significant network breaches start with an application such as e-mail delivering an exploit,” Keil said. “Then, once on the network, attackers use other applications or services to continue their malicious activity – in essence, hiding in plain sight. Knowing how cyber criminals exploit applications will help enterprises make more informed decisions when it comes to protecting their organizations from attacks.”
“Our research shows an inextricable link between commonly-used enterprise applications and cyber threats,” explained Matt Keil, senior research analyst at Palo Alto Networks. “Most significant network breaches start with an application such as e-mail delivering an exploit,” Keil said. “Then, once on the network, attackers use other applications or services to continue their malicious activity – in essence, hiding in plain sight. Knowing how cyber criminals exploit applications will help enterprises make more informed decisions when it comes to protecting their organizations from attacks.”
Accorring to the report, 34 percent of the roughly 2100 applications observed can use SSL encryption. As a result, many network administrators are unaware of what applications on their networks use unpatched versions of OpenSSL, which can leave them exposed to vulnerabilities such as Heartbleed, the security firm warned.
Interestingly, Palo Alto Networks found that 99 percent of all malware logs were generated by a single threat using UDP; attackers also use applications like FTP, RDP, SSL, and NetBIOS to mask their activities.
Taking Action
In addition to sharing findings in its report, Palo Alto Networks provided some actionable advice that security teams can use to better protect their networks. According to the company, some things enterprises should do include:
• Deploy a balanced safe enablement policy for common sharing applications – key to the success of this recommendation is documentation of the policies, education of users, and periodically updating the policy.
• Control unknown traffic – every network has unknown traffic: small in volume, averaging only 10 percent of bandwidth we observed, but high in risk. Controlling unknown UDP/TCP will quickly eliminate a significant volume of malware.
• Determine and selectively decrypt applications that use SSL – selective decryption, in conjunction with enablement policies outlined above, can help businesses uncover and eliminate potential hiding places for cyber threats.
The Application Usage report is particularly interesting because it’s generated based on raw data coming from activity happening on enterprise networks, and not through a user-based survey. The data gathered for the reports comes from evaluation units of the company’s Next Generation Firewalls deployed at potential customer locations. This most recent report was compiled based on analysis of traffic data collected from 5,500 network assessments and billions of threat logs over a 12-month span between March 2013 and March 2014, the company said.
Register for the upcoming Webcast on July 9: Detecting and Preventing Advanced Persistent Threats















