Many manufacturers and healthcare delivery organizations (HDO) are concerned about medical device attacks, but only few have taken significant steps to address the threat, according to a study commissioned by electronic design automation solutions provider Synopsys.
The study, based on a survey of 550 individuals conducted by the Ponemon Institute, shows that 67 percent of medical device makers and 56 percent of HDOs believe an attack on the medical devices they build or use is likely to occur in the next 12 months.
In fact, roughly one-third of respondents said they were aware of cyber incidents that had a negative impact on patients, including inappropriate therapy or treatment delivery, ransomware attacks, denial-of-service (DoS) attacks, and hijacking of medical devices.
On the other hand, only 17 percent of device manufacturers and 15 percent of HDOs have taken significant steps to prevent attacks. Roughly 40 percent on both sides admitted that they haven’t done anything to prevent attacks.
Only 25 percent of device makers and 38 percent of HDOs are confident that the security mechanisms built inside devices can adequately protect patients and the clinicians who use these systems.
While mobile devices help clinicians be more efficient, approximately half of respondents believe that their use in hospitals and other healthcare organizations significantly increases security risks.
A majority of respondents believe securing medical devices is very difficult. The survey showed that many focus on security requirements instead of more efficient practices, such as security testing throughout the development lifecycle, code review, and dynamic testing.
The study shows that more than half of device manufacturers and HDOs blame the presence of vulnerable code on lack of quality assurance and testing procedures, while nearly 50 percent also blame the rush-to-release pressure on the development team, accidental coding errors, and lack of training on secure coding practices.
The study shows that 36 percent of manufacturers and 45 percent of HDOs do not test devices. Some of those that do test have admitted finding vulnerabilities and even malware.
While medical device manufacturers are most concerned about hacker attacks and the challenges posed by securing new medical technologies, service providers are more concerned about keeping up with regulatory requirements, and the medical industry’s lack of protection for patients and users.
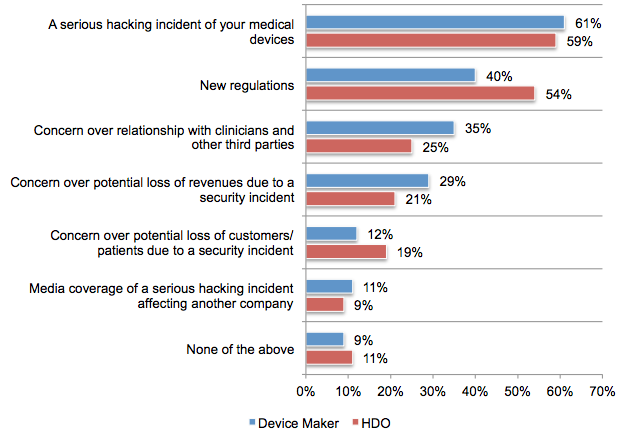
When it comes to budget, a majority believe a serious hacking incident affecting medical devices would likely lead to a budget increase. A significant percentage of respondents also believes new regulations would also influence budget.
Related Reading: Thousands of Third-Party Library Flaws Put Pacemakers at Risk
Related Reading: Sobering Thoughts When a Connected Medical Device Is Connected to You
Related Reading: Medical Devices Infected With WannaCry Ransomware













