AMSTERDAM – HACK IN THE BOX – Researchers have demonstrated that remote attackers can wirelessly change the time on network time protocol (NTP) servers over long distances using inexpensive devices.
NTP is a networking protocol utilized to synchronize time between computer systems. NTP uses a hierarchical system of time sources where the first level (stratum 0) is represented by reference clocks, such as atomic, GPS and radio clocks (JJY, WWVB, DCF77 and WWVH). The computers on the other levels (stratum 1, stratum 2, etc.) are synchronized with the previous stratum and also with devices on the same stratum for sanity checks, stability and robustness.
NTP servers can be used by organizations to synchronize the time on devices within their network, but they also play an important role in industrial and power generation networks.
Shifting time on an NTP server can have serious consequences — it allows attackers not only to damage or disrupt systems, but also to authenticate to services using expired credentials, bypass HTTP STS and certificate pinning, and cause TLS clients to accept revoked or expired certificates.
In a presentation at the Hack in the Box (HITB) conference this week, Yuwei Zheng and Haoqi Shan of China-based security firm Qihoo360 showed how a remote attacker can shift time on a stratum 1 NTP server by wirelessly sending it forged radio time signals.
The researchers noted that if an attacker attempts to modify the time on the NTP server too much in one go, the server will either ignore the signal or crash. In order to alter the time without crashing the machine, the attacker can make modifications of up to 1,000 seconds at a time. Researchers told SecurityWeek in an interview that a malicious actor can send multiple spoofed signals to modify the time by 1,000 seconds, and each of them takes roughly 6 minutes to process.
Yuwei Zheng and Haoqi Shan used widely available, low-cost parts to develop proof-of-concept (PoC) devices that can be used to target NTP servers by emitting fake GPS and JJY signals. They demonstrated the capabilities of these devices by targeting an NTP server that they had set up to provide the time to a smartphone.
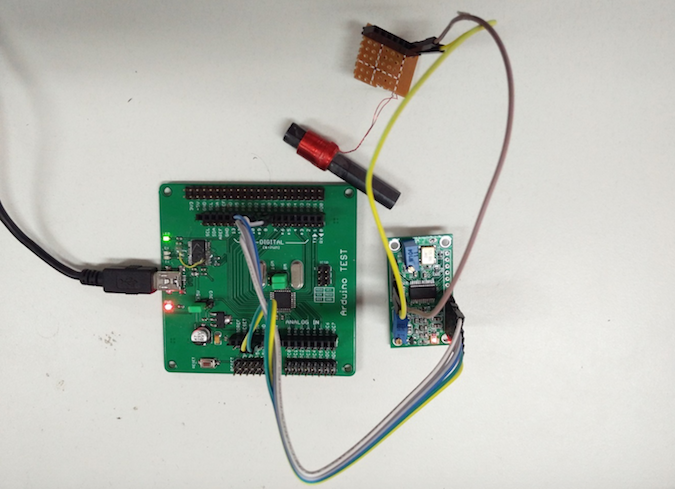
The experts said a GPS attack can work on distances between 50 and 100 meters (164 – 328 feet), but the fake signals can also be amplified and focused to target devices from up to 2 km (1.2 mi) away. The researchers noted that NTP servers using GPS as a reference clock usually have a GPS antenna on the roof or in a window of the building that houses them, which makes them easy to target.
In the case of JJY, which is used to synchronize radio-controlled clocks in Japan, researchers believe attacks can also be launched over distances of up to 2 km (1.2 mi).
Based on their analysis and discussions with NTP server vendors, the researchers determined that their attack method works against devices that are widely deployed in China, North America and Europe. However, the experts said vendors don’t appear to be too concerned, despite some of them admitting that their products don’t include any protections for these types of attacks.














