Cisco announced on Monday that it has added some important security, compliance and analytics features to its Spark collaboration platform.
Launched in March 2015, Cisco Spark provides cloud-based tools for team messaging, online meetings and whiteboarding. One year after its launch, the company announced $150 million in funding to drive application development for Spark.
Cisco has now announced four major improvements to Spark, including end-to-end message encryption and compliance features typically required in enterprise environments, such as e-discovery and data loss prevention.
Another data protection feature allows organizations to protect sensitive assets against attacks targeting the Cisco Collaboration Cloud by running an on-premises key server to encrypt and decrypt data sent to Spark. This way, customers benefit from Spark’s capabilities while having the data security equivalent of on-premises storage.
The latest improvements made to the Spark platform also aim to help IT and security teams address the challenges posed by bring-your-own-device (BYOD) initiatives. Cisco Spark now includes device and application management features that allow administrators to enable device-level PIN lock, automatic logout for apps running outside the company network, and enterprise certificate pinning to protect users from malicious hotspots.
Cisco has also added analytics capabilities to help IT teams determine if users are experiencing call quality problems. Administrators can easily obtain data from their browser via what Cisco calls “fluid analytics,” which is available for both Spark and WebEx.
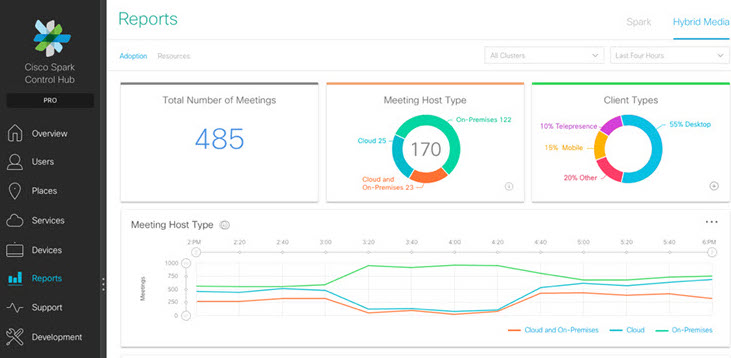
The four new Spark features are available through the new Spark Control Hub, the new Pro Pack and third-party integrations.
The Control Hub is a tool that allows administrators to provision and manage Spark services, and view analytics data. The Pro Pack for the Control Hub is a premium offer for organizations that require more control and more advanced capabilities.
Cisco has teamed up with various companies to provide Pro Pack capabilities. Actiance and Global Relay provide compliance and archiving services, while Cisco’s Cloudlock, Symantec and Skyhigh Networks provide data loss prevention capabilities. Identity management is provided by Okta, Microsoft Azure Active Directory, and Ping Identity.
Related: Cisco Releases Open Source Malware Signature Generator
Related: Apple, Cisco Partner to Improve Cyber Insurance Policies
Related: Corvil Integrates its Security Analytics Into Cisco’s Tetration Platform
















