
SINGAPORE — SECURITYWEEK 2017 ICS CYBER SECURITY CONFERENCE | SINGAPORE — Mission-critical control systems that don’t pose an obvious risk can be hijacked and leveraged for attacks by profit-driven cybercriminals and other threat actors, researchers warned.
Cybercriminals have been increasingly relying on ransomware to make a profit by taking hostage personal and business files. Experts have also started issuing warnings regarding the possibility of ransomware attacks targeting industrial systems.
Proof-of-concept (PoC) ransomware designed to target industrial control systems (ICS) was described recently by security firm CRITIFENCE and researchers at the Georgia Institute of Technology.
These attacks focused on programmable logic controllers (PLCs), which are often critical for operations and can represent a tempting and easy target for malicious actors. However, Alexandru Ariciu, an ICS security consultant at Applied Risk, disclosed another potential target on Thursday at SecurityWeek’s 2017 Singapore ICS Cyber Security Conference.
Ariciu showed that ransomware attacks, which he has dubbed “Scythe,” can also target SCADA devices that are inconspicuous and which may be considered less risky.
Affected vendors have not been named, but the devices have been described by the expert as various types of I/O systems that stand between field devices and the OPC server (e.g. remote terminal units, or RTUs). The devices are powered by an embedded operating system and they run a web server.
Thousands of these systems are easily accessible from the Internet, allowing attackers to hijack them by replacing their firmware with a malicious version.
The attack scenario developed and demonstrated by Applied Risk starts with the attacker scanning the Web for potential targets. According to Ariciu, many devices can be identified using the Shodan search engine, but even more targets can be found via a simple Google search.
Ariciu has tested four devices from different vendors and discovered nearly 10,000 systems accessible directly from the Internet. The researcher said most of these systems lack any authentication mechanism, allowing easy access.
The expert believes an attacker could identify widely used devices and concentrate on targeting those. Once the target has been identified, the attacker first needs to acquire the device and conduct hardware debugging on it to determine how it works. The general attack process is the same for all devices, but the exploit needs to be customized for each specific product.
It took Applied Risk three months of analyzing ports, using various hardware hacking techniques, firmware dumping, and reverse engineering to determine how each device works and how it can be attacked.
Ariciu pointed out that the hands-on analysis is required to create the exploit, but once the exploit has been developed the attack can be launched remotely against devices accessible from the Internet.
The attack relies on a firmware validation bypass vulnerability that can be exploited to replace the legitimate firmware with a malicious one. In the ransomware scenario described by Applied Risk, the attacker connects to the targeted device’s interface, creates a backup for the configuration of the targeted device, and installs firmware that disrupts regular processes.
The victim sees that the compromised device has been disconnected and when they access it for analysis they are greeted with a ransomware message.
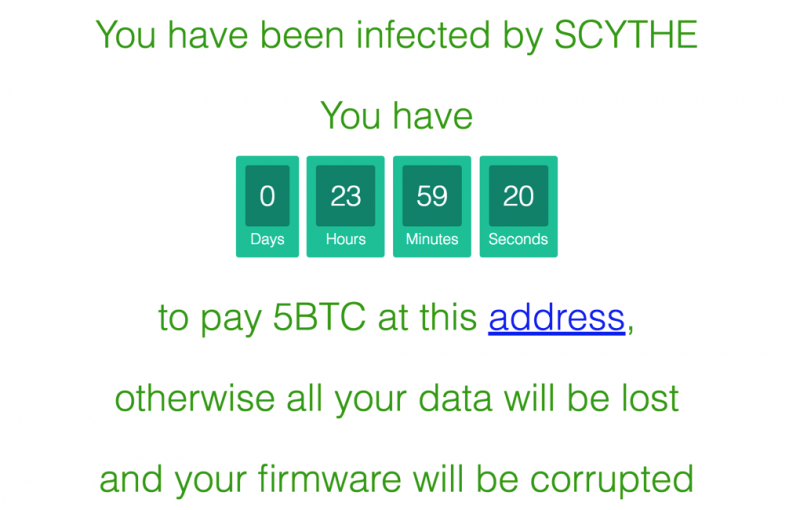
In order to prevent the victim from restoring the firmware, the attacker can “disable” the firmware and configuration update functionality. The “restore factory settings” feature does not mitigate the attack in most cases as the process does not restore the original firmware. Nevertheless, this feature can also be disabled by a hacker.
While the attack described by Ariciu prevents the victim from restoring the firmware, the attacker is still able to restore the device and its configuration if the victim pays the ransom. That is because the firmware update functionality is not actually disabled. The user needs to know the name of the firmware file in order to launch an update. If the attacker assigns a random file name of 32 characters or more, it will be impossible for the victim to determine it and conduct the firmware update.
The researcher has warned that once they determine how a specific device can be hacked, attackers may be able to launch mass attacks by leveraging the firmware update utilities provided by vendors.
Based on the number of vulnerable devices accessible from the Internet, Applied Risk believes attackers could make millions of dollars through such a campaign. According to the security firm, many organizations admitted that such an attack could cause serious disruptions — the devices are often part of mission-critical systems — which increases the chances of the ransom being paid.
Organizations alerted by the security firm indicated that they had never considered making configuration backups, especially since these devices are rarely reconfigured once they are deployed. However, losing the configuration could have serious consequences considering that a significant amount of time is spent configuring the devices.
While Applied Risk has developed a PoC demonstrating a ransomware attack that would likely be launched by profit-driven cybercriminals, Ariciu told SecurityWeek that other types of attacks are also possible. For instance, the vulnerability can be exploited by sophisticated threat actors to damage devices, either for sabotage or as a distraction while a different attack is being launched.
The four companies whose products are affected have been notified. The devices are available at prices ranging between €300 and €1,000.
Two of the vendors, including a major player, acknowledged the severity of the firmware validation bypass vulnerability. However, they indicated that fixing the security hole is not an easy task and they are still trying to identify the best approach for addressing the problem.
Related: Destructive KillDisk Malware Turns Into Ransomware
Related: Michigan Power and Water Utility Hit by Ransomware Attack
Related: Logic Bombs Pose Threat to ICS














