The number of industrial control systems (ICS) accessible from the Internet has increased significantly in the past year, reaching more than 175,000 components, according to a new report from Positive Technologies.
Using the Shodan, Censys and Google search engines, researchers identified 175,632 ICS components accessible from the Web. In comparison, similar searches conducted in the previous year uncovered just over 162,000 systems.
Of all the systems identified in 2017, more than 66,000 were accessible via HTTP, followed by the Fox building automation protocol associated with Honeywell’s Niagara framework (39,000), Ethernet/IP (25,000), BACnet (13,000), and the Lantronix discovery protocol (10,000).
The highest percentage of exposed devices, representing 42% of the total, was spotted in the United States. The number of Internet-accessible ICS components in the U.S. increased by 10% compared to 2016, from roughly 50,000 to 64,000. The U.S. is followed at a distance by Germany (13,000 accessible systems), France (7,000), and Canada (7,000).
Many of the industrial systems connected to the Web come from Honeywell (26,000), Lantronix (12,000), SMA (9,000), Beck IPC (9,000), Siemens (6,000) and Rockwell Automation (5,000).
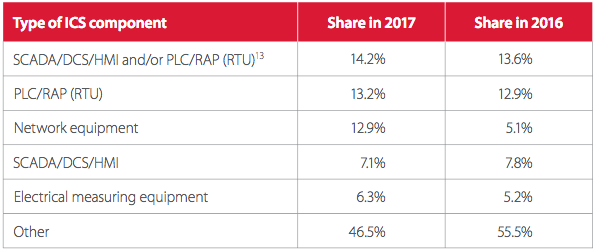
The distribution of Internet-exposed components by type has remained largely the same compared to 2016.
John Matherly, CEO of the search engine Shodan, has confirmed for SecurityWeek that there has been an increase of roughly 10% year-over-year in terms of ICS exposure on the Internet.
“The increase is mostly in building automation protocols and despite the news coverage we haven’t seen any decrease in devices,” Matherly said.
Related: Learn More at SecurityWeek’s ICS Cyber Security Conference
According to Positive Technologies, a total of nearly 200 new vulnerabilities were disclosed in 2017, compared to 115 in 2016. Worryingly, 61% of the flaws whose existence was made public last year were rated critical and high severity.
The most common types of vulnerabilities were remote code execution (24%), information disclosure (17%), and buffer overflows (12%). “Most vulnerabilities detected in 2017 can be exploited remotely without needing to obtain any privileges in advance,” Positive Technologies said in its report.
A report published in October by CyberX revealed that one-third of industrial and critical infrastructure systems had been connected to the Internet, based on data obtained by the industrial security firm by passively monitoring traffic from hundreds of operational technology (OT) networks.
Related: Industrial Firms Slow to Adopt Cybersecurity Measures, Says Honeywell














