It’s been over a month since the spam-spewing Grum botnet has been shut down, but spam experts say there hasn’t been a noticeable impact on global spam volume.
Security researchers from FireEye worked with Internet service providers in Russia, the Netherlands, and Panema to shut down the command-and-control servers controlling the Grum botnet. The last server Ukraine was shut down July 18. Symantec researchers at the time estimated that Grum was responsible for one-third of all spam being sent worldwide, and its takedown led to an immediate drop in global spam email volumes by as much as 15 to 20 percent, according to July’s Symantec Intelligence Report.
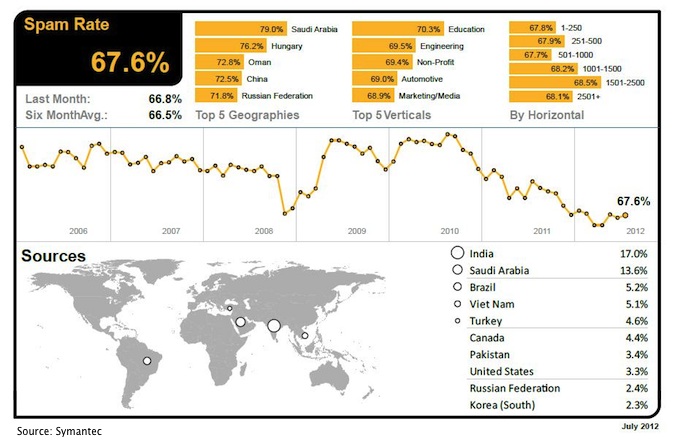
However, the drop was only temporary, since in the days since, the global volumes have been creeping up, Eric Park, an Abuse Desk Analyst at Symantec, told SecurityWeek. In fact, if the present trend continues, August may wind up with a higher global spam volume than in July, Park said. According to Symantec’s July report, global spam volume was 67.6 percent (1 in 1.48 emails was flagged as spam), an 0.8 percent increase over June.
There’s been “minimal to no change” in spam as a result of the Grum takedown, Park said.
While Grum had an estimated hundred thousand zombies sending spam, the machines were likely blocked for sending emails too frequently, or wound up on IP blacklists, said Andrew Conway, Cloudmark researcher. IP filtering is fast and cheap, and is a good first line of defense against spam, Conway said. Grum spam was easy to blacklist, and despite its size, most spam messages from the botnet probably never reached user inboxes.
Even in the heyday of spam botnets, in the period between 2007 and 2010, Grum was “a distant sixth” in terms of size and in number of spam generated, Mary Landesman, a senior security researcher at Cloudmark, told SecurityWeek. Rustock, shut down in 2011, had 150,000 bots and sent out 30 billion messages per day at its peak, compared to Grum, with a mere 50,000 bots and only 2 billion spam messages per day, Landesman said.
The big players, such as Storm, Rustock, and Srizbi, are no longer in action, which left Cutwail, Bobax and Grum as the “top 3” spam botnets. Cutwail and Bobax has been up and down over the past two years and haven’t really had much of an impact, making Grum appear to be a larger player in the botnet-drive spam space than it really was, Landesman pointed out.
Considering that users never saw Grum-delivered spam to begin with, the lack of an impact is not surprising, Landesman said.
Global spam has actually been declining since 2008. Symantec’s Park ran some numbers, and saw that a month before the McColo botnet was shutdown in 2008, global spam volume was 5.8 trillion. In June 2008, when the botnet was shutdown, spam volume was 3.1 trillion, and a month later, spam had dropped even more to 2.5 million. The numbers crept up a bit after that, and a month before the Bredolab botnet and Spamit affiliates were knocked off line in 2010, total spam volume was 3.8 trillion. In October 2010, after the botnets were no longer operational, the spam volume was 2.9 trillion, and dropped to 2.4 million a month later.
By the time Microsoft focused its attention on the Rustock botnet, global spam volume was a shadow of what it was before McColo’s demise. A month before Rustock’s shutdown, spam volume was 1.6 trillion. Volume dropped to 1.3 trillion in March 2011 when authorities seized the C&C servers, and slid down to 1.2 trillion a mother later.
Each botnet shutdown has had less impact on global spam volumes compared to earlier shutdowns, Park pointed out. While the percentages look great —spam declined 57 percent after McColo, 37 percent after Bredolab and Spamit affiliates,and 25 percent after Rustock—the drop in numbers are getting smaller, Park said.
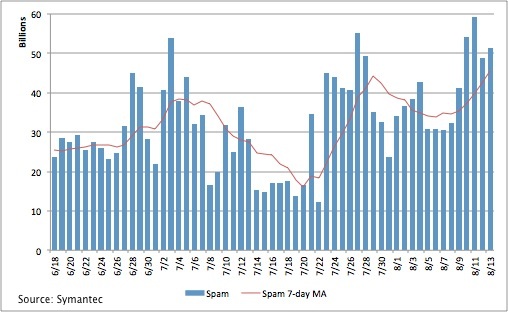 While Park didn’t have global spam volume figures handy for the most current month, he noted that daily global spam volume was about 25 billion in mid-June, a month before Grum’s last C&S server was turned off on July 18. The number dropped to about 12 billion to 15 billion between July 18 and July 22, Park said. By Aug. 13, daily spam volume was consistently over 50 billion by Aug. 9.
While Park didn’t have global spam volume figures handy for the most current month, he noted that daily global spam volume was about 25 billion in mid-June, a month before Grum’s last C&S server was turned off on July 18. The number dropped to about 12 billion to 15 billion between July 18 and July 22, Park said. By Aug. 13, daily spam volume was consistently over 50 billion by Aug. 9.
Recovering from the spam drop was really quick, surprisingly so, after the Grum takedown, Park said.
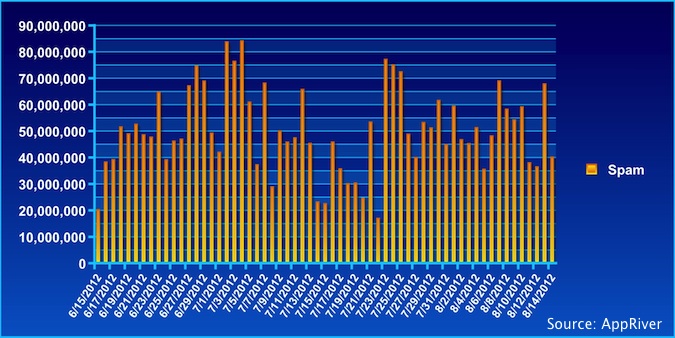
The numbers are different, but the trend tells the same story when looking at spam volume figures from other companies. AppRiver saw spam volumes recover within a week to the levels observed in June, Troy Gill, a security analyst with AppRiver, told SecurityWeek.
“We do not currently see any signs of a comeback from the Grum botnet, yet traffic remains equal to the rates we were seeing before the takedown,” Gill said.
It’s important to note, also, that spammers have turned away from very large botnets for spam delivery in favor of smaller, more focused and presumably more easily managed botnets, Landesman said. This means there are more botnets, each one with less individual impact, while the total impact on global spam volume remained about the same.
The spam-delivery market is “very fluid,” Gunter Ollmann, vice-president of research at Damballa, told SecurityWeek. There are multiple “suppliers” offering medium-to-large botnets for spam campaigns, and the operators tend to “subscribe” to multiple suppliers, Ollmann said. As a result, “takedowns of an individual supplier can be counteracted within a day or two,” Ollmann said.
Symantec’s Park also felt that the spammers had learned their lessons from previous takedowns and have diversified their infrastructure. Instead of one large botnet they are using for all their needs, they have multiple networks, one for fake pharmaceutical, one for online gambling, and so on, making it easy to remain in business even after one takedown. They’ve learned “not to put all their eggs in one basket,” Park said.
The Grum takedown has important implications from a law enforcement standpoint, because increasing the cost of business can act as a deterrent for future operations, Park and Landesman agreed. However, it’s also important to consider the dissenting opinion, that the takedown did nothing to stop the criminals, and may have actually caused some harm, Gunter Ollmann, vice-president of research at Damballa, told SecurityWeek.
“The ‘Takedown’ was ineffectual,” Ollmann said, as it shut down servers but did nothing to stop the techniques the operators had used to infect victims and build the botnet in the first place, nor did it result in the arrests of the actual criminals. In fact, the “ill-conceived takedown” alerted the botnet operators to some of the mistakes the Grum team had made that allowed the researchers to track them, which means it will be even more difficult to build up future evidence against these spammers, Ollmann said.
These actions have simply caused “the bot masters to improve their botnets and further insulate themselves from the errors that allow more strategic law enforcement operations to be successful,” Ollmann said.