Flashback Mac Trojan Cloaks Itself as Adobe Flash Update, Opens Backdoor to Mac OS Systems
It has been a busy few days in the world of Mac malware.
The week opened with a report that Apple had updated its blacklist of known malware to include the Trojan dropper Revir, and it is closing with reports about the spread of a new Trojan known as Flashback. While Revir disguised itself as a PDF file, Flashback cloaks itself as a Flash Player update.
While Mac security firm Intego initially the Trojan was not widespread, it has since noted an uptick in reports of infections.
According to Intego, the Trojan is spreading via malicious Websites.
“The first things you see are the crashed plugin graphic and the purported error messages,” the company explained in a blog post. “After this, the fake Adobe Flash installer screen pops up, and then the Flashback Trojan horse installation package downloads. At this point, if you have the default Safari settings – which allow “safe” downloads to open automatically – you will see an Installer window open.” (Image Below)
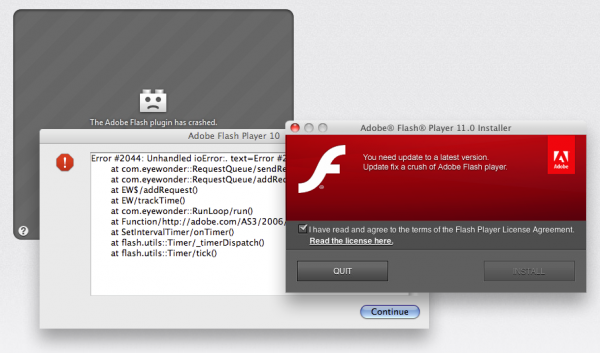
Users with the default Safari browser settings – which allow “safe” downloads to open automatically – will see an Installer window open. If the user proceeds with the installation procedure, the installer for this Trojan horse will deactivate some network security software (code in this malware specifically targets and deactivates Little Snitch, but has no effect on Intego VirusBarrier X6), and, after installation, will delete the installation package itself.
The malware installs a dyld (dynamic loader) library and auto-launch code, allowing it to inject code into applications the user launches.” The malware also installs a backdoor at ~/Library/Preferences/Preferences.dylib that communicates with a remote server and sends and receives data using RC4 encryption, according to Intego.
“This is effective social engineering,” Intego noted on its blog post. “Savvy Mac users will not be fooled, because they know that a Flash installer would never appear in this manner, but two things make this approach believable. First, Flash Player is not installed on Mac OS X Lion, so users will need to install it themselves if they want to view Flash content on the web. Second, if they do have Flash Player installed, and have set the Flash Player preference pane (in System Preferences) to automatically check for updates, they may think that this is an update alert…So this can easily fool many Mac users into downloading the malware.”
Just how users are being lured to the sites was not mentioned by Intego. However, Graham Cluley, senior technology consultant at Sophos, called it easy to imagine.
“For instance, it would be child’s play to create a website which pretends to show something salacious (“Scarlett Johansson nude video!” would probably do well at the moment, for instance) and then when you try to view it, you’re prompted to install an update to Adobe Flash. Of course, rather than the genuine Flash you would be installing the Trojan horse,” he blogged. “Similar tricks have certainly worked well in the past – against both Windows and Mac users.”
“We all know that there is much… more malware written for Windows than there is for Mac OS X,” he added. “But that doesn’t mean it’s non-existent, and it’s no excuse for leaving Apple Macs unprotected.”
















