The Future of Cyber Attacks – Do Recent BGP Anomalies Shed a Light on What’s to Come?
When experts consider modern cyber attacks they are traditionally focused on denial of service (DDoS), global botnet, and DNS hi-jack attacks. Each of these tends to cause downtime or service outages and require partnering with service providers to remediate the incident. However, as recent as last month’s experiment run by Duke University and the YouTube outage of two years ago we are starting to see anomalies with the Internet’s core protocol, BGP, that may be just as disruptive, with the potential to be even worse.
Border Gateway Protocol (BGP) is the protocol that supports routing decisions made to pass data across the Internet. BPG makes decisions based on path availability, network policies and rules built into routing tables. The healthy operation of the global Internet is based on the trust that BGP route information is accurate and reliable. More and more this trust is being broken. Internet disruptions due to corrupt or improperly formatted or assigned BGP announcements are becoming more prevalent.
The Internet snafu caused by the Duke University experiment resulted in the disruption of a small portion (about 1%) of all Internet traffic but serves to demonstrate how fragile this backbone is and how far reaching a coordinated attack against this core protocol could be. An experimental data format used to make BGP announcements triggered the activity. The problem was further complicated when routers incorrectly translated the experimental format and passed along corrupt routes to their peers. Within minutes thousands of IP address blocks worldwide became unstable. Fortunately, the announcements were stopped once the defect was realized.
Similarly, in 2008, replication of BGP data created by the Pakistan Telecommunications Authority (PTA) attempting to block the country’s ISPs access to YouTube resulted in unintended consequences. The broadcast ended up being shared with Hong Kong’s PCCW, who in turn shared it with other ISPs throughout the Internet resulting in a widespread YouTube outage. In fact the announcements were more specific (or precise) than YouTube’s own Internet servers, therefore these announcements superseded and served as the overriding routes.
While these incidents were not intentionally malicious, it is not hard to imagine the potential impacts if they had been. It is certain that over the last few years the attack spectrum has evolved and will continue to evolve. The traditional form of defense-in-depth is being challenged as attacks are targeted at infrastructure outside the traditional perimeter and as such are much more sophisticated and subtle. It’s hard for organizations to monitor for and respond to those attacks. It is no longer a world of script kiddies, attackers are now motivated more than ever with criminal intent to do harm and are going after high value targets. This means more risk is introduced and requires a new pro-active and far-reaching approach to defense. You can only manage the risk for which you are aware.
While much of what occurs outside the perimeter of your enterprise is out of your control, there are actions to take in order to maintain some manor of visibility. This visibility is essential since disruptions to your ecosystem or extended enterprise may have direct impact to your business operations. BGP routes and announcements are often considered by most corporations to be the responsibility of the service provider. However, as with anything, it is not advisable to leave something so important in the hands of others. There are a couple specific conditions important to be monitored in order to prevent and/or minimize the impact of a BGP anomaly.
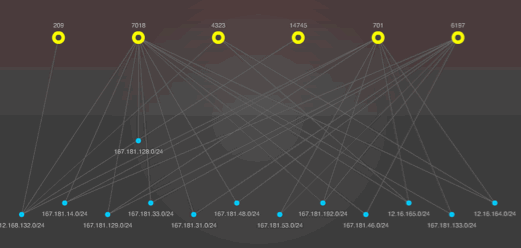
Autonomous System (AS) Peering Changes
A change to an upstream or downstream AS may directly impact routing capability and/or redundancy. Awareness of this condition will also alert the enterprise of Internet connectivity that is reliant on single-honed peers. A situation that may be important to rectify should the single-honed peer be providing service to a critical asset.
Unauthorized Prefix Announcement
An unauthorized prefix announcement indicates that someone other than the originator of the prefix is advertising the IP block. This is a significant anomaly and may be evidence of a BGP-hijack. Whether intentional or not, this is a condition that must be explored as it indicates someone else is using IP space assigned to you.
More-specifics Announcements
More-specifics are used to assign IP address space to a specific subnet. A more-specific announcement becomes cause for alarm when an AS announces a more specific prefix than what is announced by the true originating AS. This again could be evidence of a BGP-hijack or an outside entity using IP space that was not intended for its use.
These conditions should be monitored for assets assigned to you, your partners, your customers, and others that make up your extended enterprise. The positive identification of an occurrence of any one of these conditions should trigger an analysis effort to determine the root cause and nature of the event. The impact of the disruption is directly related to the time in which it goes undiscovered. Therefore, early detection is critical. Once the cause is identified, remediation and recovery can take place, which may involve working closely with security vendors and service providers. Identifying malicious intent is a completely different discovery. Even with an unauthorized announcement there is no guarantee of malicious intent. Consequently, even the most benign occurrence can be quite damaging. A motivated attacker could deliver a devastating blow to an unexpected, uneducated, and unaware victim.














