Security Professionals Can Use Strategic Threat Intelligence to Help Justify Security Spending Decisions and to Realign Budgets
In my last article, I walked through a mind map that shows the many facets of cyber threat intelligence and how they all should fit into your overall security strategy and program. With that high level understanding, over the next set of articles we’ll zoom into a different section of that mind map. This article will focus on strategic cyber threat intelligence (CTI).
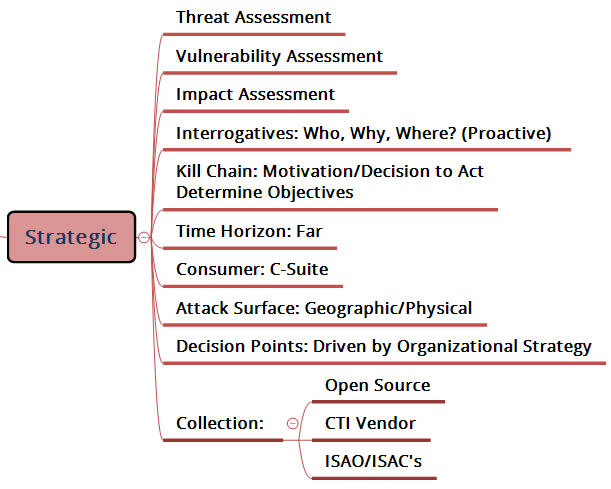 Strategic threat intelligence is where threats are tied to organizational impact in more of a proactive, risk-based view and aligned to the organization’s business objectives. This level of intel should help inform business decisions regarding cyber risks and the implication of threats to the organization. Armed with strategic CTI you can direct and/or re-direct cybersecurity efforts and investments to ensure they are in line with business priorities.
Strategic threat intelligence is where threats are tied to organizational impact in more of a proactive, risk-based view and aligned to the organization’s business objectives. This level of intel should help inform business decisions regarding cyber risks and the implication of threats to the organization. Armed with strategic CTI you can direct and/or re-direct cybersecurity efforts and investments to ensure they are in line with business priorities.
In an April 2017 Forrester report titled “Achieve Early Success In Threat Intelligence With The Right Collection Strategy”, the first of three key takeaways is:
“Start with Strategic Intelligence Capabilities. Strategic intelligence will give the maximum return for early forays into threat intelligence as the data will be consumable by you and assist in developing and communicating your security strategy to leadership.”
I think Forrester makes a good argument here. Certainly there is value to all three levels of CTI – strategic, operational and tactical – but as a starting point you should aim to “see the forest for the trees.” Without that big picture view, you end up in a reactive cybersecurity stance, which is never-ending. A security program that is driven by strategic threat intelligence is more proactive and helps the business make more informed risk-based decisions.
When thinking about strategic threat intelligence, the first step is to determine what questions (aka requirements) you want to answer. For example:
• For the Boardroom – Are we well positioned for cyber threats or are we not? If not, why not?
• For the Organization – Are there different threats to different lines of business? Are the threats changing over time? What threats are others facing in our sector? What are the most likely threats? How are they being accomplished?
• For the Business Unit Leader – What are your most important cyber assets and what is being done to keep those secure? Have there been recent cyber incidents, and if so, have the weak links been addressed? Have any of our partners or those in our supply chain suffered a cyber-attack? What are we doing about it? Have we identified our digital “level of presence” and are we actively monitoring that presence for fraud risks or cyber threat events?
Starting out by trying to answer questions, like the above, can help you establish your data collection plan. Getting data shouldn’t be challenging as there are many sources – open sources, CTI vendors, dark web, ISACs, internal data, etc. However, distilling that data into relevant intel is tough and ultimately that’s where the real value for your organization is created. Threats come from all angles and with organizations’ digital footprints also expanding, knowing where to focus your efforts is no simple solution.
Who Should be Using Strategic Cyber Threat Intelligence
While cyber risk ranked as the most important risk for both public and private boards, it was among the most challenging risks for those boards to oversee (EisnerAmper’s 2017 Board of Directors Survey). The reason is that there often remains a divide between the technical and the business side of organizations, where cyber risk management is not yet ingrained into the business strategy.
Strategic threat intelligence can help you reset the corporate culture, shifting cybersecurity accountability from its own silo and elevating cyber risk understanding and decision-making to both technical and business leaders. The way to bridge the gap – so that cyber problems and solutions are relevant and comprehensible to those in the C-suite and boardroom – is to look at cyber threats through a business intelligence lens. A good way to start is to establish “the plan” for each business unit within your organization using the seed questions highlighted above in a structured way, and shoot to deliver a finished intelligence product that gives the business unit leader insight and context into where they stand for cyber threats and what course of action they can take to reduce those threats to their business unit.
Security professionals can use strategic threat intelligence to help justify security spending decisions and to realign budgets to address the right areas of focus when it comes to cyber risk. With this intel that can be easily understood by all stakeholders, it is easier to make the case for and defend budgetary requests, and it’s easier for the business to understand the impact of a yes/no decision as it relates to the cybersecurity spend.
Business executives can benefit from strategic threat intelligence by gaining critical insights and establishing meaningful cybersecurity benchmarks to monitor and revisit as part of regular business strategy sessions. For example, if you’re looking to acquire another business, include cyber risk as part of that due diligence process. See how you stack up to your peers and competitors from a cyber risk and cybersecurity readiness perspective, as well as to show cybersecurity preparedness and due diligence with litigators and r
egulators.
Ultimately strategic cyber threat intelligence should be driving your cybersecurity program and approach. It ensures that the organizational strategy will be tied in with your cyber risk management and sets the stage for more meaningful risk assessments and threat impact analysis to help put you in more of a proactive stance that improves your overall cyber hygiene.
















