The World is Moving Faster and Security Can’t Keep Up.
Fiona: You didn’t slay the dragon?
Shrek: It’s on my to-do list.
— DreamWorks, Shrek
For many IT and security managers, the increased cyber threat environment is a little like the epic quest played out in the movie Shrek: a series of diabolical adventures embarked upon by extraordinary beings in and out of castles (data centers) and magical forests (clouds). The complexity and sheer number of items to track and monitor appear to be beyond the skill of mortals.
The quest business is a pretty good. Visiongain estimates today’s cybersecurity market to be worth $75B worldwide and Gartner estimates it will grow to $100B+ by 2018, a CAGR of roughly 10 percent. Contrast that with overall IT spending, which is crawling along with an annual growth rate in the low single digits.
Yet for the enormous focus on security spending, enterprises appear less safe than ever. Emotionally, enterprises feel besieged by the “hack a minute” mentality that pervades our industry. In 2015, so far, some 148 million records have been publicly breached in 129 reported incidents — incidents that sometimes go undetected for months at a time. That’s reported numbers, not the real story.
Perhaps the singular focus on detecting cyber incursions is not the answer.
Perhaps a coequal focus on containing attacks after they occur is equally as important.
If we have learned one thing in the past few years, relying exclusively on detection technologies such as IDS and APT will cause significant problems. We must also look at how attacks spread laterally and remain active over extended periods of time, especially in data center and cloud environments. It is now time to prioritize visibility and containment, augmenting the priority of looking for suspicious and anomalous communications to the attack surface.
This is doubly important in the area of distributed, dynamic, hybrid and heterogeneous computing. As agile software development and continuous delivery become more the mode of how enterprises create applications, traditional infrastructure technologies can no longer keep up with the change requirements and the speed required by developers. More significantly, as cloud infrastructure models become the norm — especially public IaaS offerings such as AWS and Azure — the lack of visibility and control they offer means enterprises need new approaches to reducing their attack surface and more quickly containing breaches.
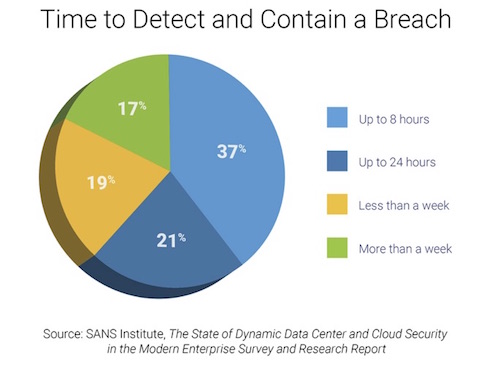
A recent SANS Institute survey, The State of Dynamic Data Center and Cloud Security in the Modern Enterprise Survey and Research Report, underscores that most IT professionals are unhappy with the level of visibility and containment provided by the traditional tools they use to monitor traffic between data centers and internal or external clouds. Nowhere is this more evident than in the time these technologies take to stop and contain breaches: fewer than 50% of breaches are detected and contained within 24 hours.
Nowhere is this more self-evident than in the recent Scottrade cyber breach, where 4.6 million customers’ contact information was taken from the company’s servers. What is so striking, even beyond the scale of sensitive data that was stolen, was the duration of the breach. It went on for months. The castle was unlocked for months.
The really bad news—and the key lesson
Today over one-third of the organizations surveyed by SANS use distributed cloud and data center computing systems. Forty-four percent of respondents said their biggest challenge was that cloud providers don’t offer the visibility needed to protect users and data. So the world is moving faster and security can’t keep up. Containment is the new detection.
This does not mean investing in technologies to detect breaches is a bad idea. However, if security professionals are going to keep up with the DevOps teams that are driving a new computing paradigm, they will need to invest in different approaches, ones that provide granular visibility and a reduced attack surface. While these new techniques may not stop breaches, they can reduce the scope of damage that a breach inflicts, and the amount of time it takes to stop it. If not, we are all going to feel a little like Shrek being chased through a castle by a fire-breathing dragon.












