Tucked away in a small town outside Moscow, Russia one of the world’s most prolific and effective cybercriminals works away on the next version of malicious software that will enable the theft of millions of dollars from unsuspecting victims around the world.
Going by the online moniker of “Paunch,” he is continuously updating his browser exploit software, called “Black Hole” and it is wreaking havoc daily amongst many of the world’s largest brands and government organizations.
 His software doesn’t actually enable the theft of money, exfiltrate data, or keylog victims as you may suspect, but it is the premier product in the “browser exploit pack” (BEP) software category. These exploit “kits” are installed onto websites, some compromised, others set up by criminals. Then, when people visit these sites using a vulnerable browser, and large portions of them are, their computers are immediately broken into. This allows for the installation of any kind of malware the exploiter wants to put on them. Often times this will be one of the very latest in crimeware like Zeus, Bugat, or Cridex.
His software doesn’t actually enable the theft of money, exfiltrate data, or keylog victims as you may suspect, but it is the premier product in the “browser exploit pack” (BEP) software category. These exploit “kits” are installed onto websites, some compromised, others set up by criminals. Then, when people visit these sites using a vulnerable browser, and large portions of them are, their computers are immediately broken into. This allows for the installation of any kind of malware the exploiter wants to put on them. Often times this will be one of the very latest in crimeware like Zeus, Bugat, or Cridex.
Over the past six to twelve months, this technique has grown rapidly, and is now responsible for a huge portion of the phishing style spam seen today. These are the spam campaigns you’ve likely seen filling up your inbox of late—warnings from the IRS, NACHA, the BBB, or financial institutions about inappropriate behaviors or mysterious charges. Some of the most effective have been fake, but spot-on alerts purporting to be from American Express, AT&T and Verizon about billing issues, using the same template that real alerts from those companies use. Other campaigns have been tied to updating software like Adobe and Intuit’s products, unpaid traffic tickets from New York City, airline ticket purchases from many major airlines like American and US Air, and a host of other highly effective lures. Unlike traditional phishing though, when someone clicks on the link embedded in the e-mail, they aren’t taken to a look-alike site and asked for credentials. Instead, they are driven to a BEP infested site, where their computer is likely to be infected, with the victim usually being none the wiser. With such high quality lures, the infection rates have been staggering, according to reports from affected companies, and some insight into back-end control panels for the malware that researchers have been able to gain access to on occasion. We’re talking well above 10% infection rates for an entire campaign.
Not an easy case to make
 Ironically, the work Paunch is doing probably isn’t technically illegal in and of itself, as he’s simply writing software that others then buy or rent to actually hack victims’ computers and steal from them. So while he’s perfectly aware of what people are doing with his creation, as he’s advertising its uses and actively providing customer support for it, the case against him is difficult to make and then prove in court. This means Paunch may be in business for a long time to come, and we’ll be dealing with this threat for the foreseeable future. While he likely has a very good idea of how many people are being affected directly by his exploits since those stats are kept up-to-date on his servers, he probably doesn’t have a clue how much damage he’s done to the value and trust consumers have in many of the most important institutions in the United States and the Western world. The hope is that this “menace to society” will find himself behind bars for a long time. In the meantime, it’s important to understand what Paunch’s online crime model is, and how to deal with it.
Ironically, the work Paunch is doing probably isn’t technically illegal in and of itself, as he’s simply writing software that others then buy or rent to actually hack victims’ computers and steal from them. So while he’s perfectly aware of what people are doing with his creation, as he’s advertising its uses and actively providing customer support for it, the case against him is difficult to make and then prove in court. This means Paunch may be in business for a long time to come, and we’ll be dealing with this threat for the foreseeable future. While he likely has a very good idea of how many people are being affected directly by his exploits since those stats are kept up-to-date on his servers, he probably doesn’t have a clue how much damage he’s done to the value and trust consumers have in many of the most important institutions in the United States and the Western world. The hope is that this “menace to society” will find himself behind bars for a long time. In the meantime, it’s important to understand what Paunch’s online crime model is, and how to deal with it.
How it works
There have been many articles written about the technical aspects of BEP software, especially Black Hole in recent months, so deep technical dives are easy to find. The main thing to remember is that this software is maintained and updated regularly, with a robust business model supporting it. Subscribers are continuously updated with the latest exploits against such software as Java, Adobe Flash Player, Adobe Reader, Microsoft Data Access Components (MDAC), and other programs and browser plug-ins. This means that cybercriminals don’t have to worry about finding exploits, engineering them, or updating their own code—that’s all done conveniently for them by Paunch and his crew.
Typically, miscreants will purchase access to a Black Hole server and configure it via a domain name or names they get. Paunch and his gang can help out there too if needed. These customers will then point a series of “redirector” sites at this server via obfuscated scripts hidden on compromised legitimate sites that reference the controlling domain name. Other “suppliers” on the black market can sell access to compromised sites like these if the buyer doesn’t have his own stable of hacked sites. Then the criminals will rent out a spamming botnet (usually Cutwail) to send out hundreds of thousands of phishing-like e-mails to drive traffic to the redirectors, or use another technique like malicious links sprinkled throughout social networks or malicious ads to drive traffic. The miscreants decide what they want to download onto victims’ computers, and the Black Hole control panel conveniently allows for any sort of file based on geography, version of operating system, and many other selection criteria. The hackers can then either take control of these computers themselves, or sell access off to other criminals who want to grow their botnets or defraud those victims directly.
So at the end of the day, we have a very sophisticated e-crime ecosystem, with customers, buyers, and traders all specializing in their areas of expertise. With the Black Hole kit as a foundation, most of the work is highly automated and well tracked so miscreants can measure campaign efficacy, just like your best online marketers.
First class e-crime infrastructure at bargain rates
Paunch’s business model is straightforward, but his pricing is a bit odd. He advertises prolifically on various hacker forums, and it is easy to rent a Black Hole server for your domains.
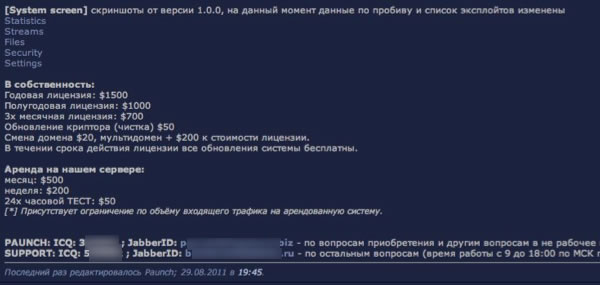
As shown in the above screen shot, his pricing model allows users to choose simple hosting provided by Paunch for $50 a day or use thier own server tied to a single domain for $700 for three months, or they can spend up to $2,000 a year allowing them to keep updating domains as they get killed. This latter point is quite important. It clearly points out that going after domains that are actually hosting the exploit sites (rather than just the spamvertized compromised redirector sites) actually drives up the costs to the criminals using them. They have to pay more for their exploit infrastructure—at least until it costs them $2,000 a year. Flipping that argument around though, for a mere $2,000 a year, they can rent out the most effective exploit system available on unlimited domain names, making the cost of becoming an effective cybercriminal pretty much chump change.
Be prepared—any organization can be targeted
Given this highly effective, automated business model, and that it is proving difficult to bring Paunch and his crew to justice, we’re going to continue seeing these attacks every day for the foreseeable future. Any organization with a large customer base should be prepared for these attacks, not just financial institutions, e-commerce companies, ISPs and others accustomed to traditional phishing attempts. Organizations need a response plan that includes detection of attacks, mitigation of source domains (you can probably ignore the redirectors), proper customer messaging about virus protection, and contingencies for handling an onslaught of calls and e-mails from customers falling for the lures. Several companies that have been spoofed in these massive attacks have been completely overwhelmed, suffering customer losses even though their sites were never compromised, or even spoofed online. The lures are usually that good. Further, adoption of e-mail authentication technologies like SPF, DKIM, and DMARC would be extremely helpful in combatting the spam lures that spoof well-known brands.
This case points out the need for law enforcement and potentially legislators to consider targeting the providers of criminal infrastructure for special consideration. BEP kits make it trivially easy for “script kiddies” and others to break into computers and do real harm. The kit creators can maintain at least an arm’s-length distance from their customers who are actually committing the traditionally prosecuted crimes, yet they are typically fully aware and supportive of those illegal activities. Improved coordination and communication amongst law enforcement and the security community with these attacks, combined with creative legal theories and casework is likely necessary to break these gangs.
Related: Black Hole Exploit Kit Gets an Upgrade
Related: Oracle Java Vulnerability Exploit Rolled into BlackHole Kit















